|
2 | 2 |
|
3 | 3 | ## Introduction [](https://devtron.ai/pricing) |
4 | 4 |
|
5 | | -The [Deployment Template](../../reference/glossary.md#base-deployment-template) might contain certain configurations intended for the DevOps team (e.g., `ingress`), and not meant for developers to modify. |
6 | | - |
7 | | -Therefore, Devtron allows super-admins to restrict such fields from modification or deletion. |
| 5 | +The [Deployment Template](../../reference/glossary.md#base-deployment-template) might contain certain configurations (e.g., `ingress`) that are critical to the stability and security of the applications. To prevent unauthorized or accidental changes to such configurations, Devtron allows super admins to restrict (lock) such critical configurations from modification or deletion. |
8 | 6 |
|
9 | 7 | 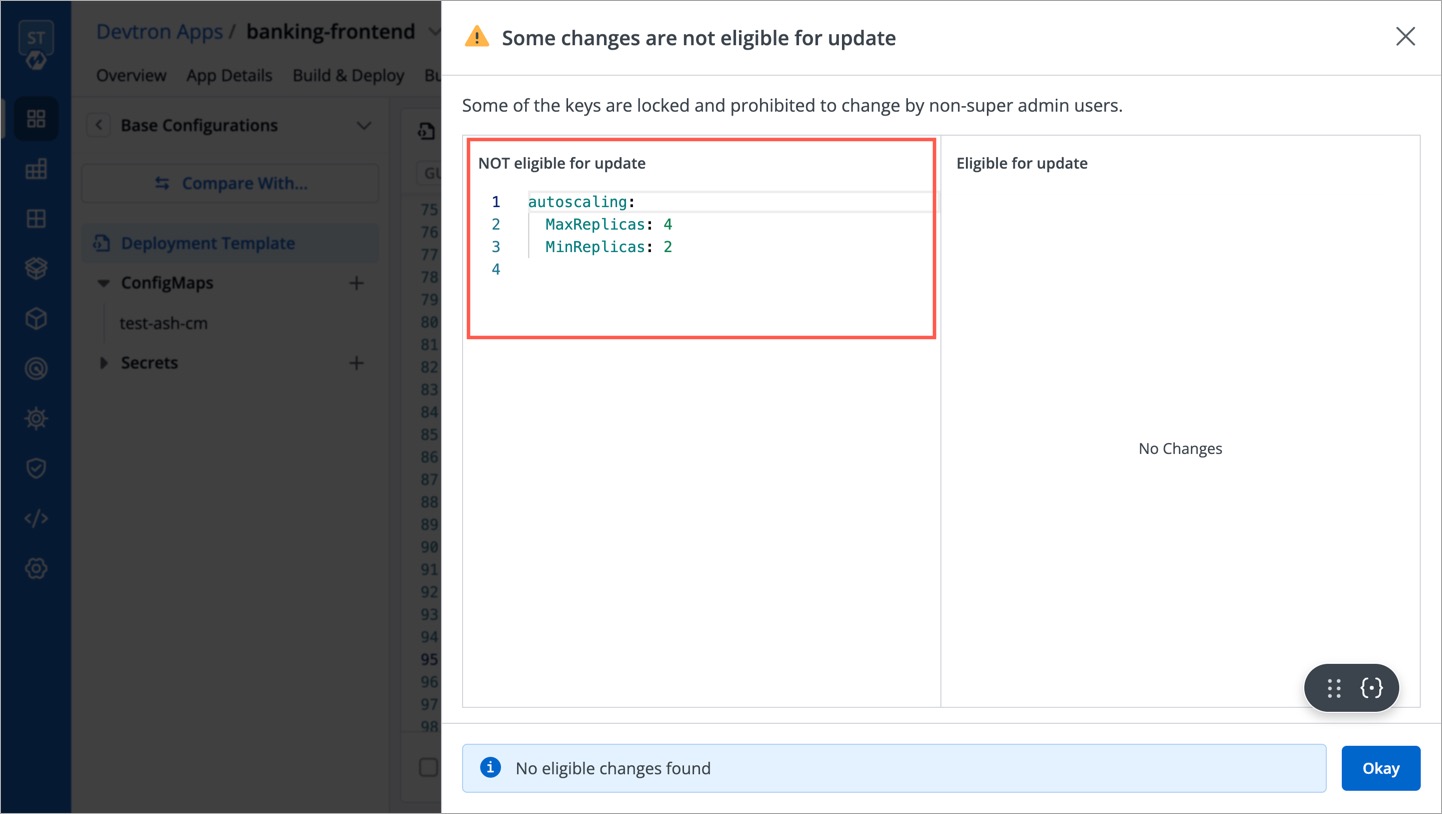 |
10 | 8 |
|
11 | | -This stands true for deployment templates in: |
| 9 | +These restrictions can be applied for deployment templates in both the: |
| 10 | + |
12 | 11 | * [Base configuration](../../user-guide/creating-application/deployment-template.md) |
13 | 12 | * [Environment-level configuration](../../user-guide/creating-application/environment-overrides.md) |
14 | 13 |
|
15 | 14 | **How is this different from the 'Protect Configuration' feature?** |
16 | 15 |
|
17 | 16 | The 'protect configuration' feature is meant to verify the edits by introducing an approval flow for any changes made to the configuration files, i.e., Deployment template, ConfigMaps, and Secrets. Refer [Approval Policy](../global-configurations/approval-policy.md). |
18 | 17 |
|
19 | | -Whereas, the 'lock deployment configuration' feature goes one step further. It is meant to prevent any edits to specific keys by non-super-admins. This applies only to deployment templates and is performed at global-level. --> |
| 18 | +Whereas, the 'lock deployment configuration' feature goes one step further. It is meant to prevent any edits to specific keys by non-super-admins. This applies only to deployment templates and is performed at the global level. |
20 | 19 |
|
21 | 20 | --- |
22 | 21 |
|
23 | | -## Locking Deployment Keys |
| 22 | +## Locking Deployment Configurations |
24 | 23 |
|
25 | 24 | {% hint style="warning" %} |
26 | 25 | ### Who Can Perform This Action? |
27 | 26 | Users need to have super-admin permission to lock deployment keys. |
28 | 27 | {% endhint %} |
29 | 28 |
|
30 | | -1. Go to **Global Configurations** → **Lock Deployment Config**. Click **Configure Lock**. |
| 29 | +To lock deployment configurations, you must first create a profile and apply it to the specific deployment templates. |
| 30 | + |
| 31 | +{% hint style="success" %} |
| 32 | +### What is a Lock Deployment Profile? |
| 33 | + |
| 34 | +A lock deployment configuration profile is a template that specifies which configurations (keys) in the deployment template cannot be edited or deleted by non-super admin users. By using lock deployment configuration profiles, super-admins can manage edit access at different levels, such as global, cluster, environment, application, or a combination of application and environment. |
| 35 | + |
| 36 | +This allows for better control by making sure critical deployment template configurations are locked in sensitive environments (production), while giving flexibility to change deployment template configurations in other less critical environments (QA, Staging, etc.). |
| 37 | +{% endhint %} |
| 38 | + |
| 39 | +### Creating Profile |
31 | 40 |
|
32 | | -  |
| 41 | +To create a profile, follow the steps below: |
33 | 42 |
|
34 | | -2. (Optional) Click **Refer Values.YAML** to check which keys you wish to lock. |
| 43 | +1. Go to **Global Configurations** → **Lock Deployment Configuration**. |
35 | 44 |
|
36 | | - 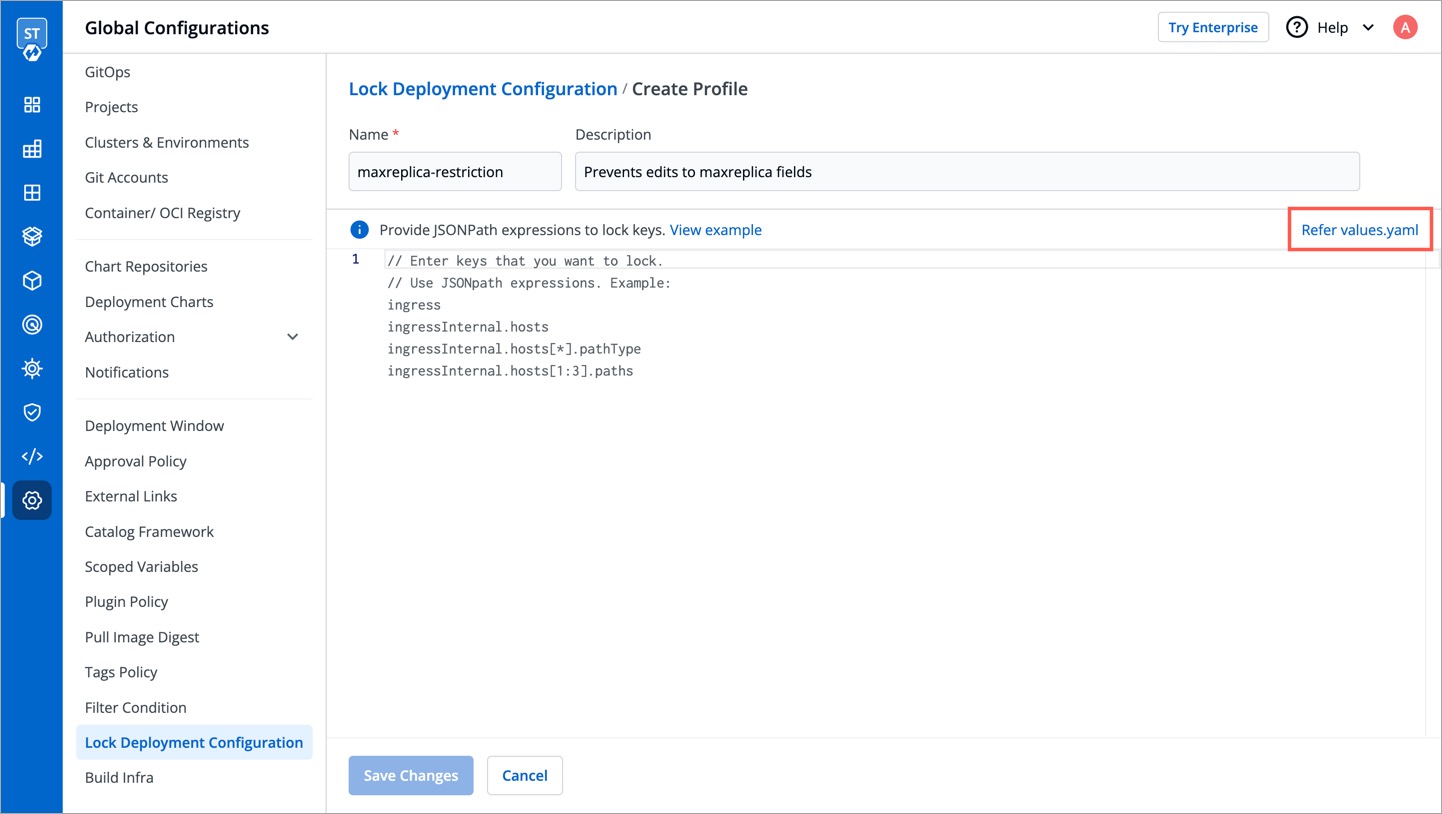 |
| 45 | +2. Click **+ Create Profile**; a new **Create Profile** page will open. |
37 | 46 |
|
38 | | -3. Enter the keys inside the editor on the left-hand side, e.g., `autoscaling.MaxReplicas`. Use <a href="https://goessner.net/articles/JsonPath/index.html" target="_blank">JSONpath expressions</a> to enter specific keys, lists, or objects to lock. |
| 47 | +  |
| 48 | + |
| 49 | +3. Enter the **Name** (Required) and a **Description** (Optional) for the profile. |
| 50 | + |
| 51 | +4. (Optional) Click **Refer values.yaml** to check which keys you wish to lock. |
| 52 | + |
| 53 | + * Select the relevant Chart type and its version to reference the keys. |
| 54 | + |
| 55 | +  |
| 56 | + |
| 57 | +5. Enter the keys inside the editor on the left-hand side, e.g., `autoscaling.MaxReplicas`. Use [JSONpath expressions](https://goessner.net/articles/JsonPath/index.html) to enter specific keys, lists, or objects to lock. |
39 | 58 |
|
40 | 59 | 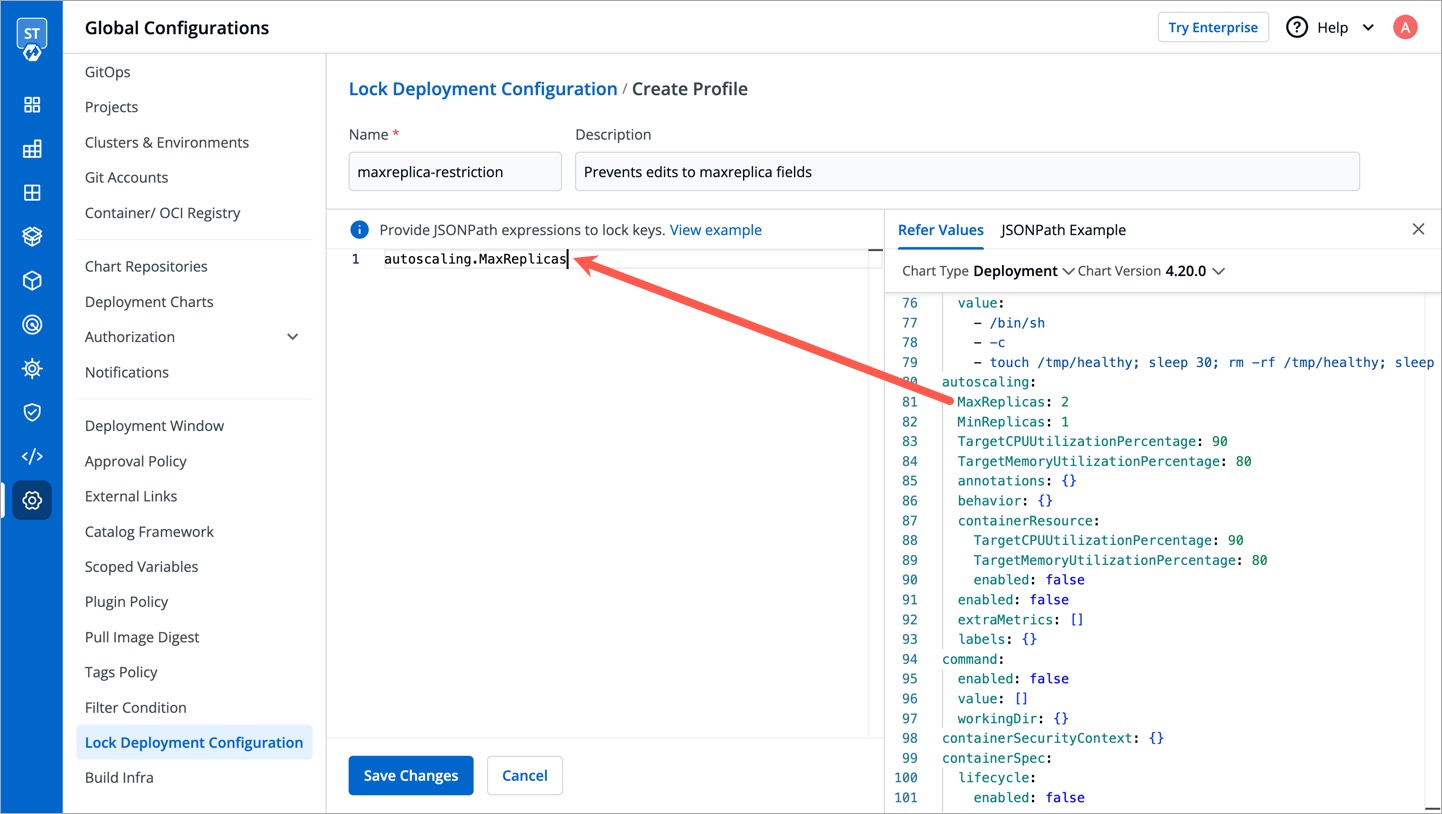 |
41 | 60 |
|
42 | | -4. Click **Save**. |
| 61 | +{% hint style="warning" %} |
| 62 | +### Keys are case-sensitive |
| 63 | +Use the exact case as defined in the deployment template, otherwise the keys will not be locked. |
| 64 | +{% endhint %} |
| 65 | + |
| 66 | + |
| 67 | +{% hint style=“info” %} |
| 68 | +### Locking custom configurations (keys) |
| 69 | + |
| 70 | +You can lock custom configurations (keys) defined in your deployment template, even if they are not listed in the **Refer values.yaml** section. As long as the key matches your lock rule, it will be locked. |
| 71 | + |
| 72 | +{% endhint %} |
| 73 | + |
| 74 | +6. Click **Save Changes**. |
43 | 75 |
|
44 | 76 | 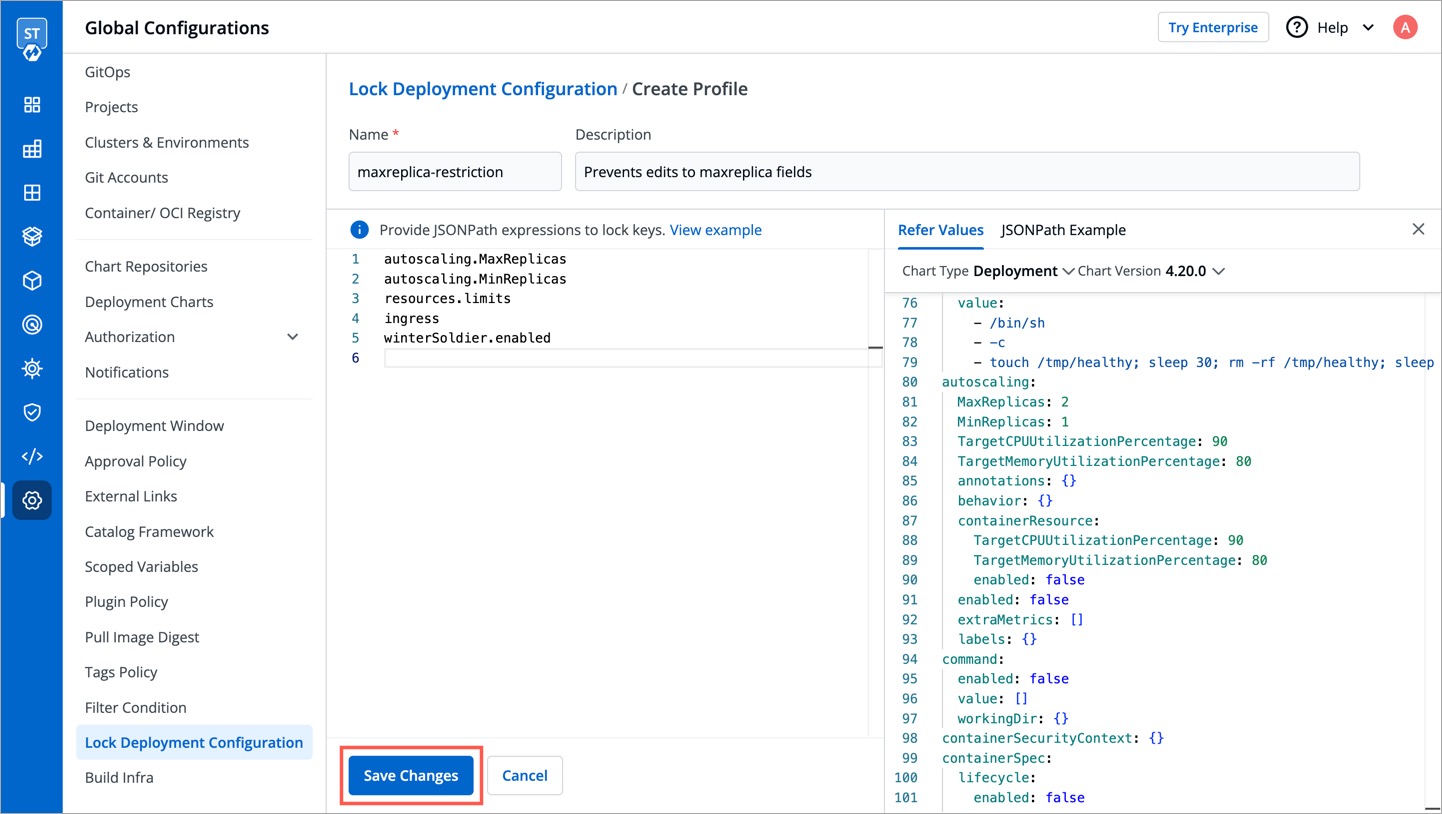 |
45 | 77 |
|
46 | | -5. A confirmation dialog box would appear. Read it and click **Confirm**. |
| 78 | +7. Profile will be created, and available under the **Profiles** tab. |
47 | 79 |
|
48 | 80 | 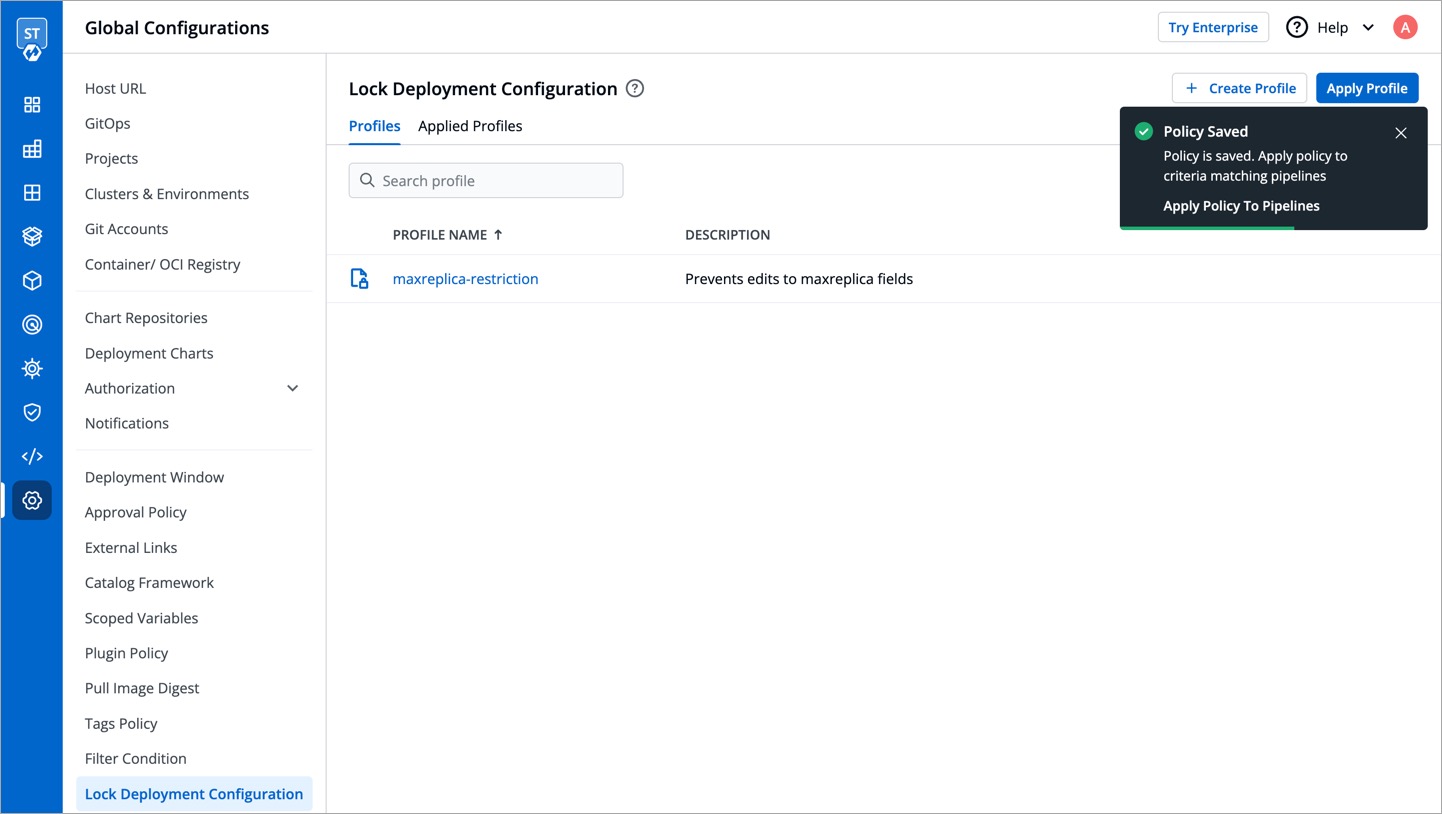 |
49 | 81 |
|
| 82 | +{% hint style="Warning" %} |
| 83 | +### Handling Locked Index Ranges |
| 84 | + |
| 85 | +If you have locked a range of configurations using JSONPath (e.g., `ingressInternal.hosts[1:3].paths`), the specified index positions are protected. |
| 86 | + |
| 87 | +If you want to add a new configuration entry (e.g., a new host), it should be added after the locked range i.e., in case of `ingressInternal.hosts[1:3].paths`, new host configuration entry should be added at the index 4. |
| 88 | + |
| 89 | +Adding an entry within the locked range may shift the indices and result in validation errors or unintended modifications of locked values. |
| 90 | + |
| 91 | +{% endhint %} |
| 92 | + |
| 93 | +### Applying Profile |
| 94 | + |
| 95 | +After creating a profile, the next step is to apply the profile to the specific deployment templates according to your use case. To apply a profile, follow the steps below: |
| 96 | + |
| 97 | +1. Go to **Global Configurations** → **Lock Deployment Configuration**. |
| 98 | + |
| 99 | + 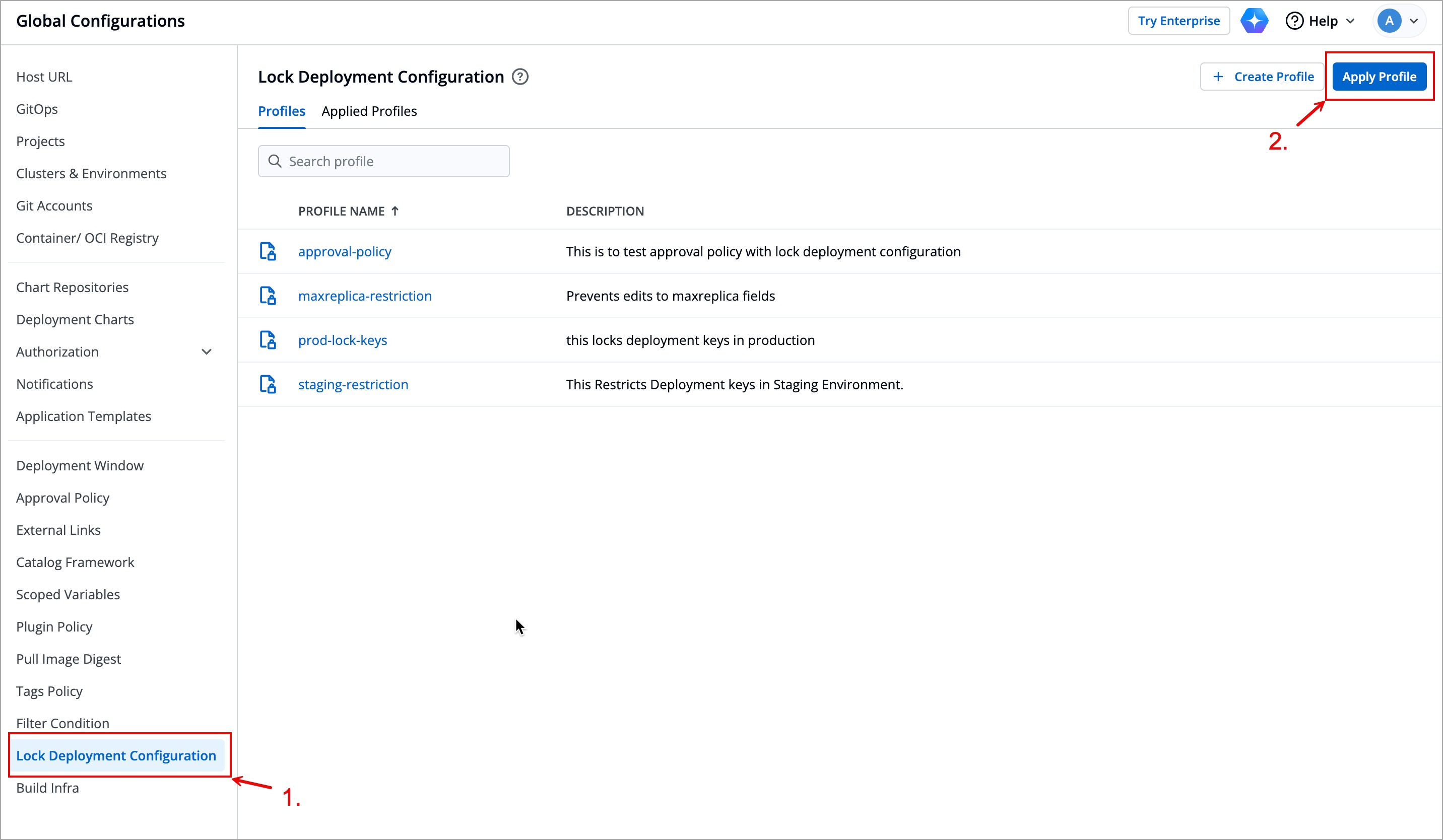 |
| 100 | + |
| 101 | +2. Click **Apply Profile**; a new **Apply Profile** page will open. |
| 102 | + |
| 103 | +3. Select the profiles that you want to apply from the dropdown under **Select profiles to apply**; you can select multiple profiles. |
| 104 | + |
| 105 | + 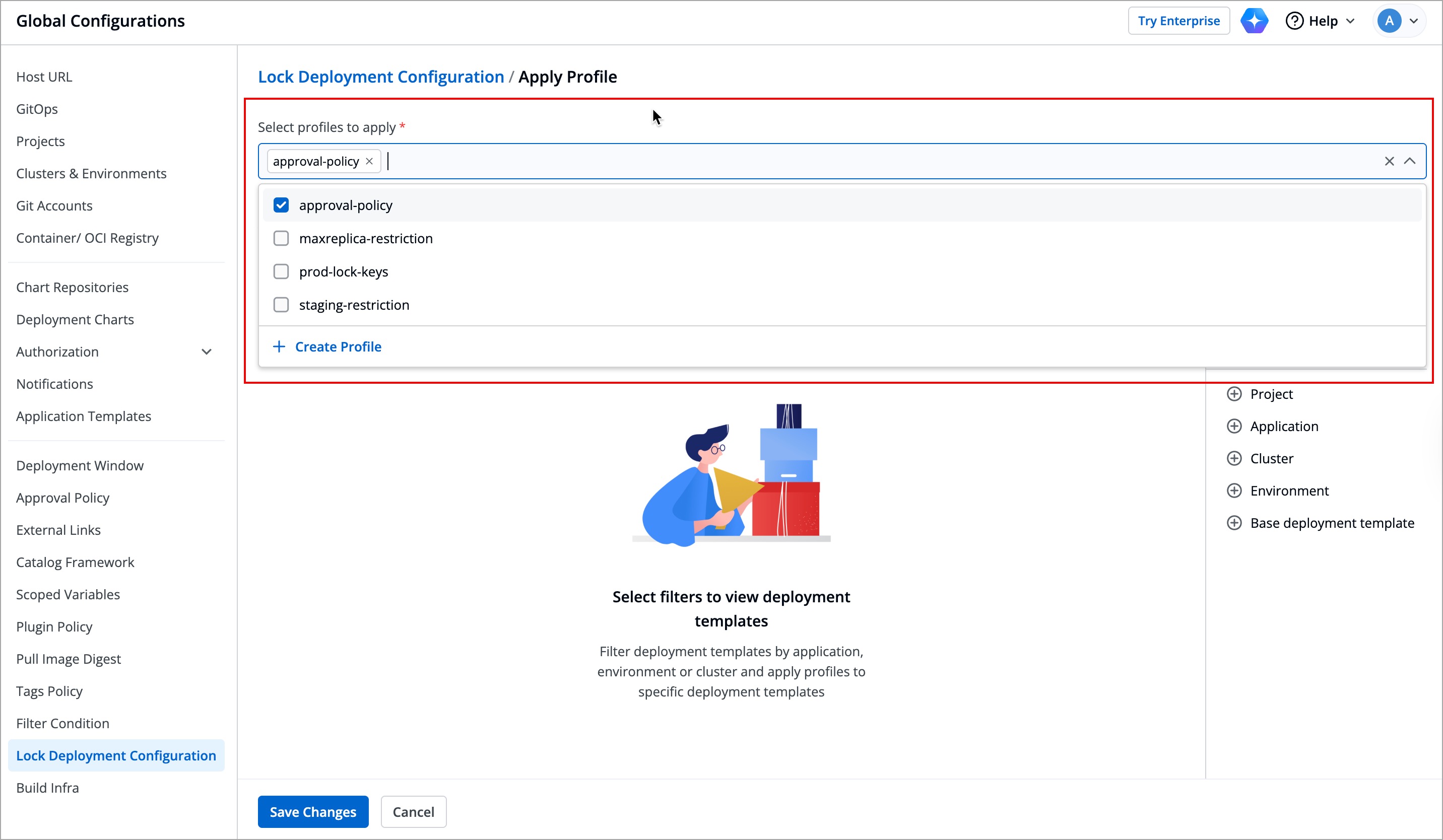 |
| 106 | + |
| 107 | +4. Select how you want to apply the profiles under **Apply selected profiles to deployment templates of**. |
| 108 | + |
| 109 | + There are three options you can choose from: |
| 110 | + |
| 111 | + 1. **Specific deployment templates**: This option allows you to apply the lock deployment configuration profile to the deployment template(s) of specific application(s) within particular environment(s). |
| 112 | + |
| 113 | + 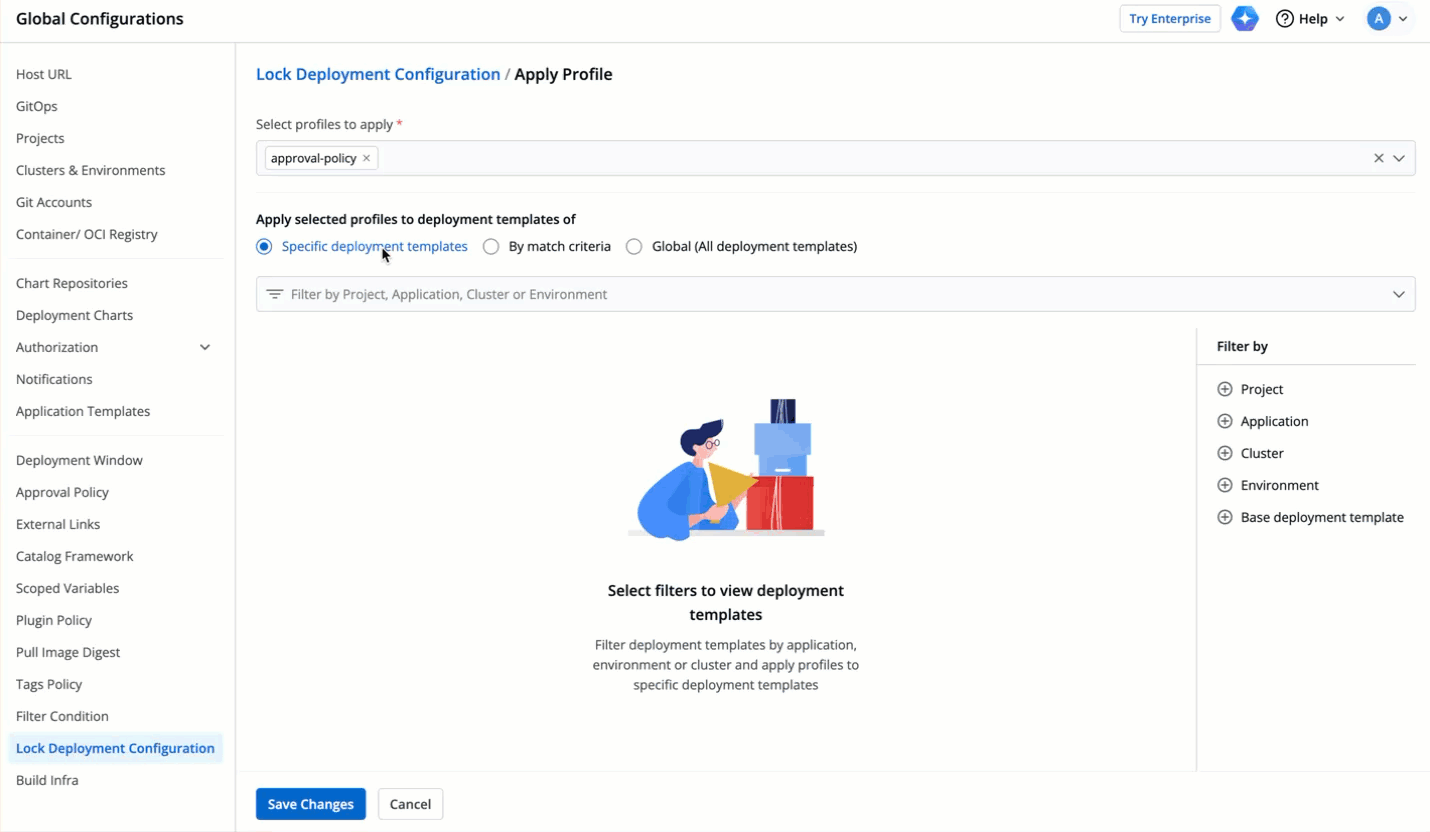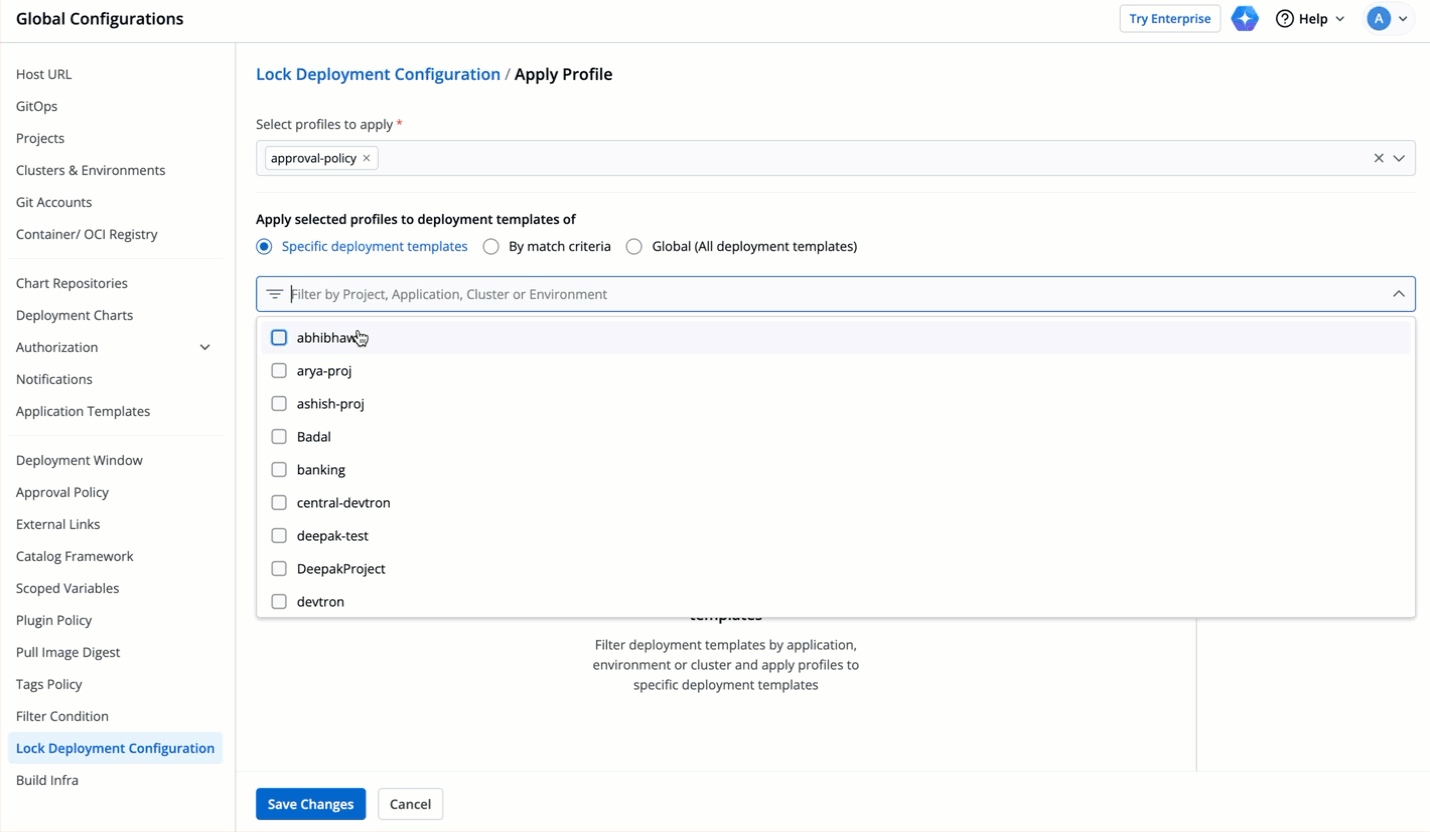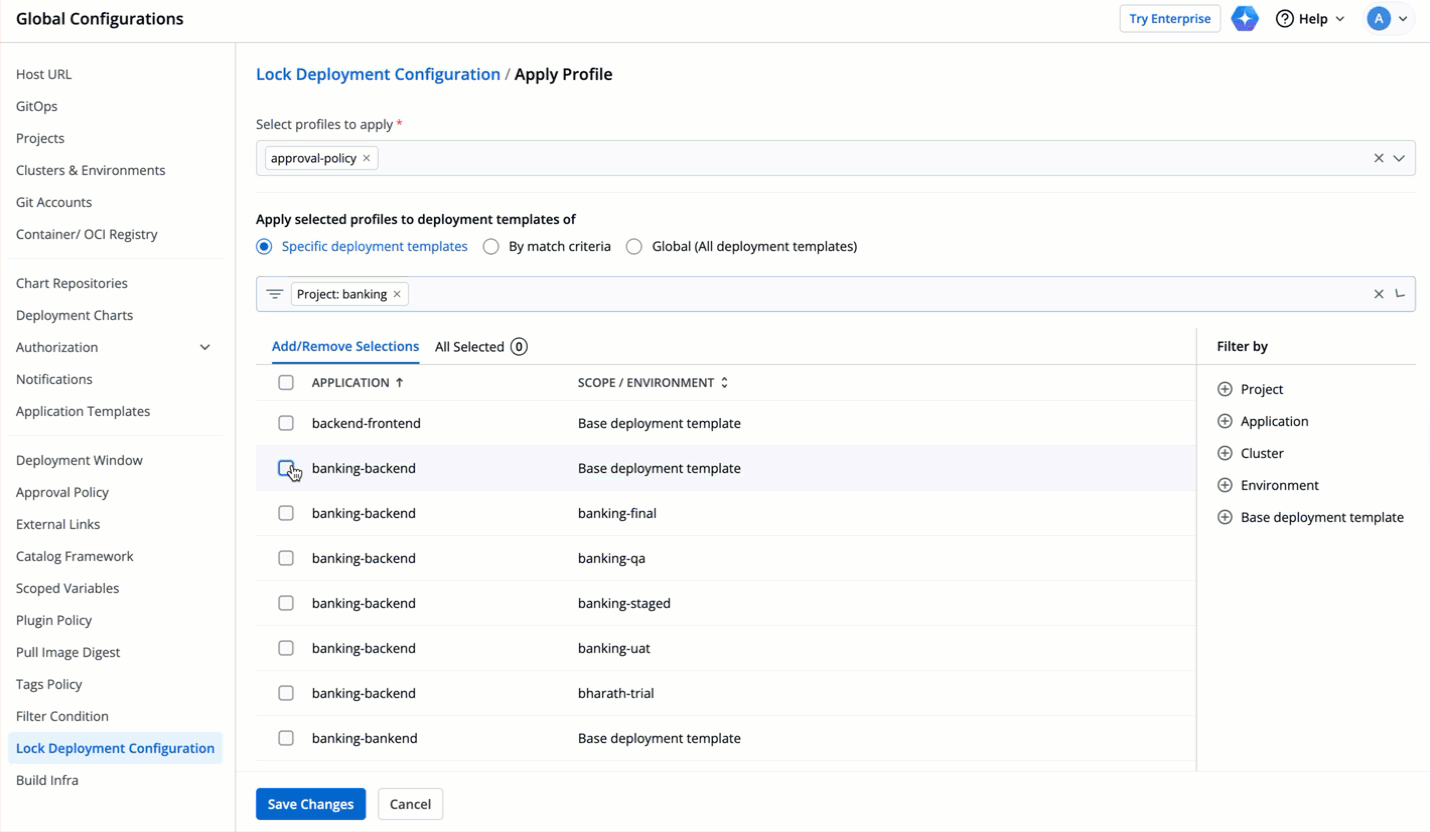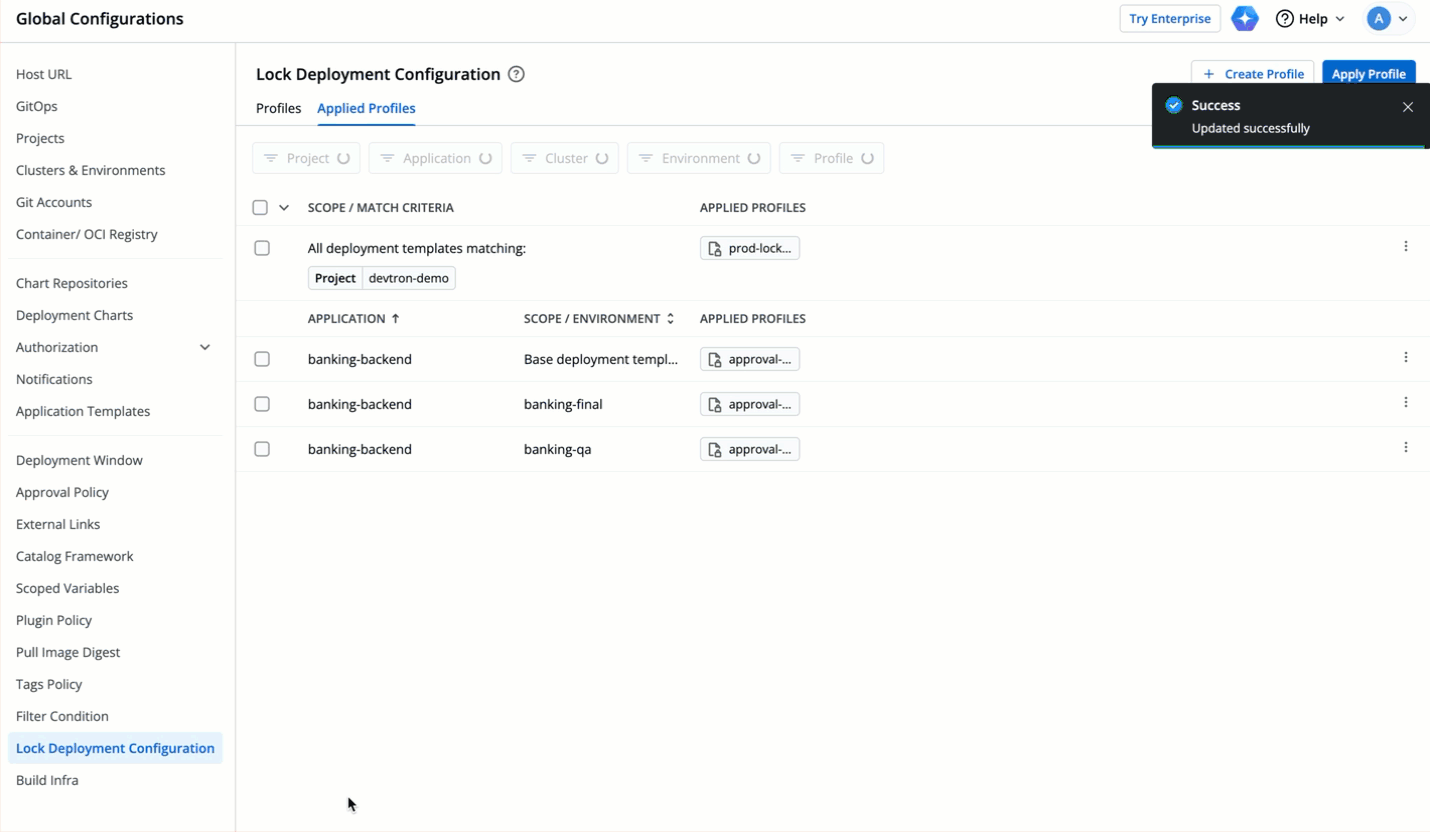 |
| 114 | + |
| 115 | + 2. **By match criteria**: This option allows you to use a combination of filters to create criteria. Lock deployment configuration profile will only apply to the deployment templates of the applications fulfilling your criteria (including existing and future ones).<br>(Optional) You may also write a note for your other team members to understand the intent and context of your policy. |
| 116 | + |
| 117 | + Let's understand how to use **By match criteria** with the below example:<br><br> |
| 118 | + |
| 119 | + Suppose you want to apply a lock deployment configuration profile to all applications in a particular project. You can achieve this by selecting that project as the match criteria. |
| 120 | + |
| 121 | + 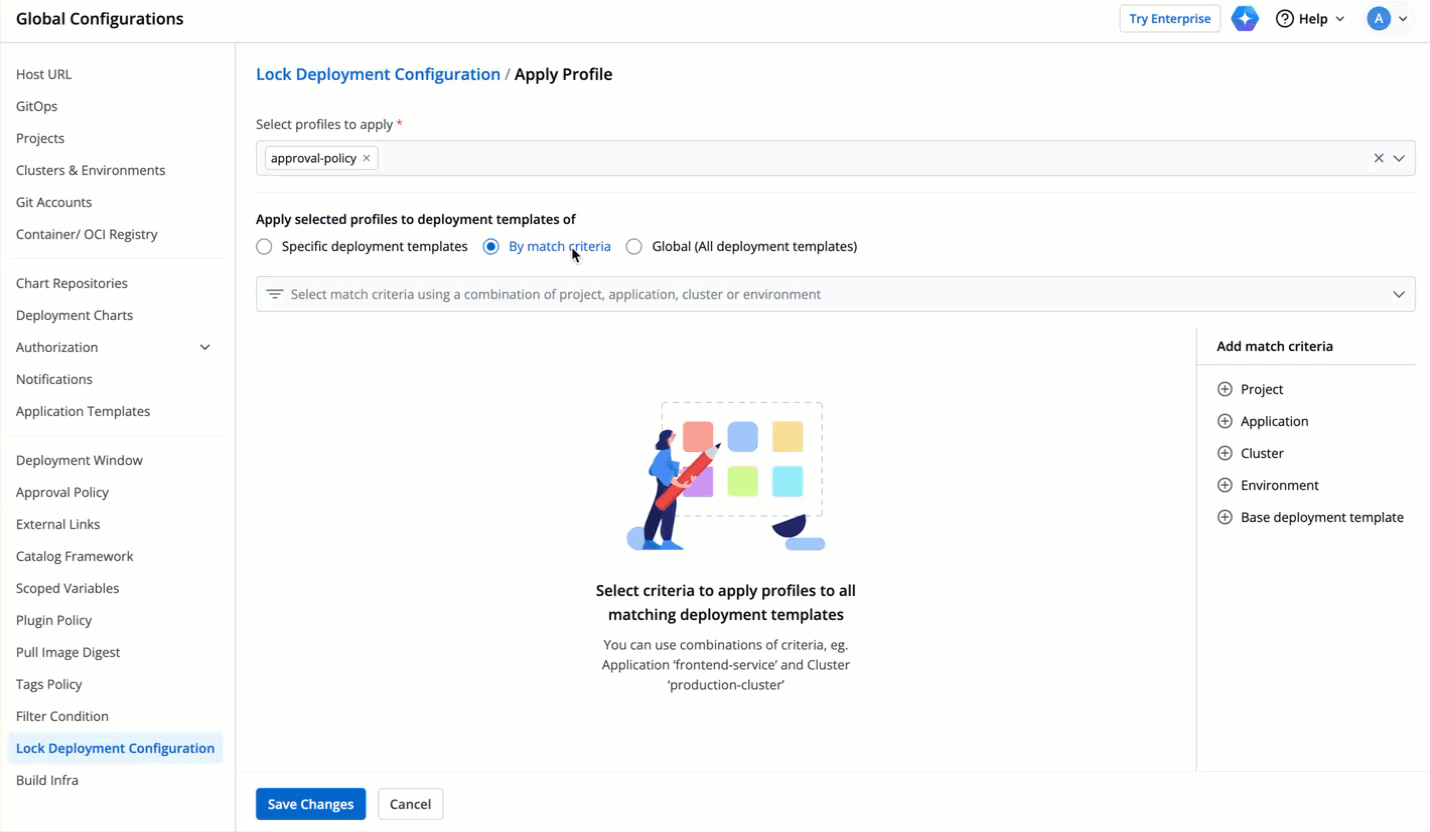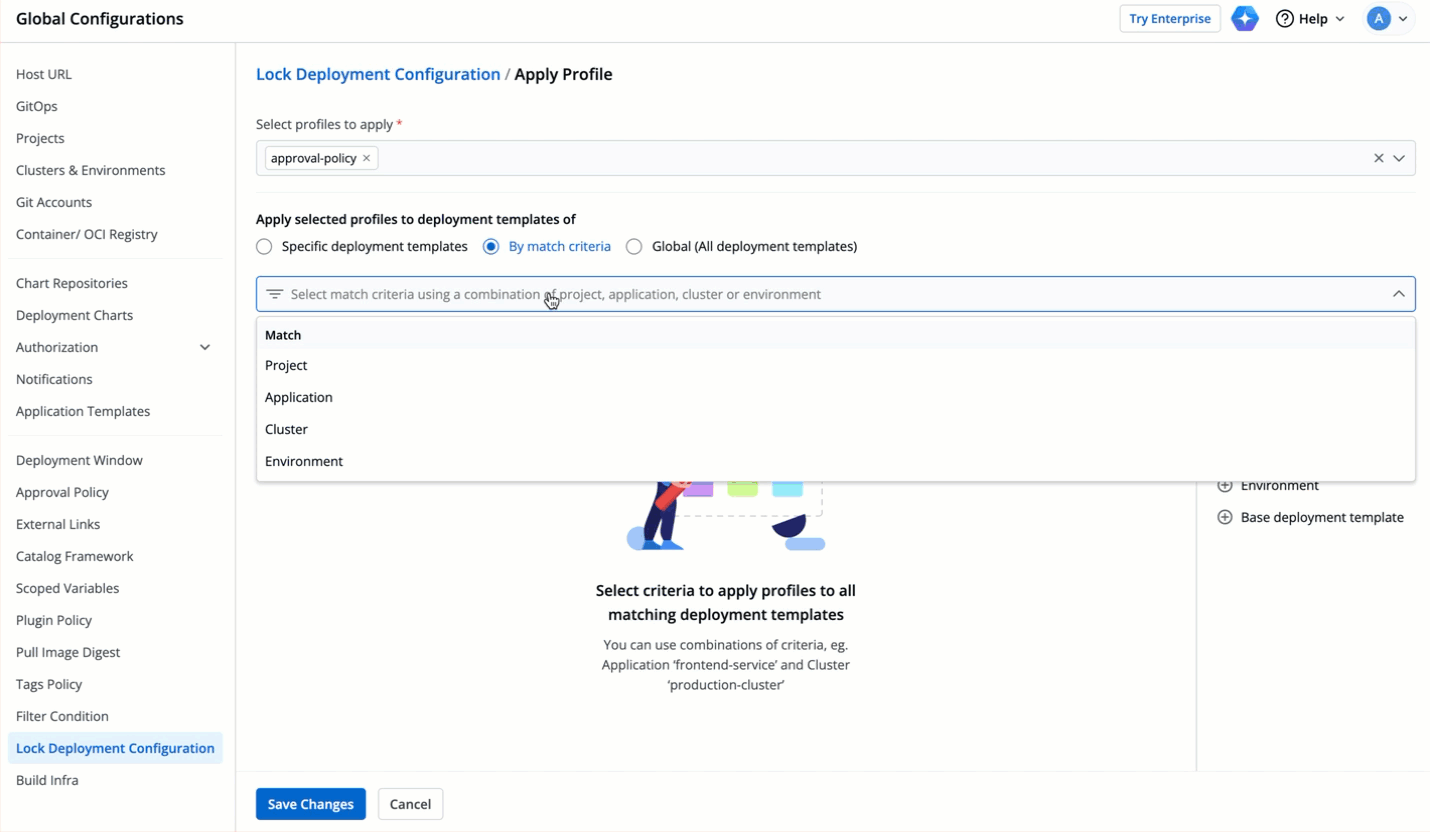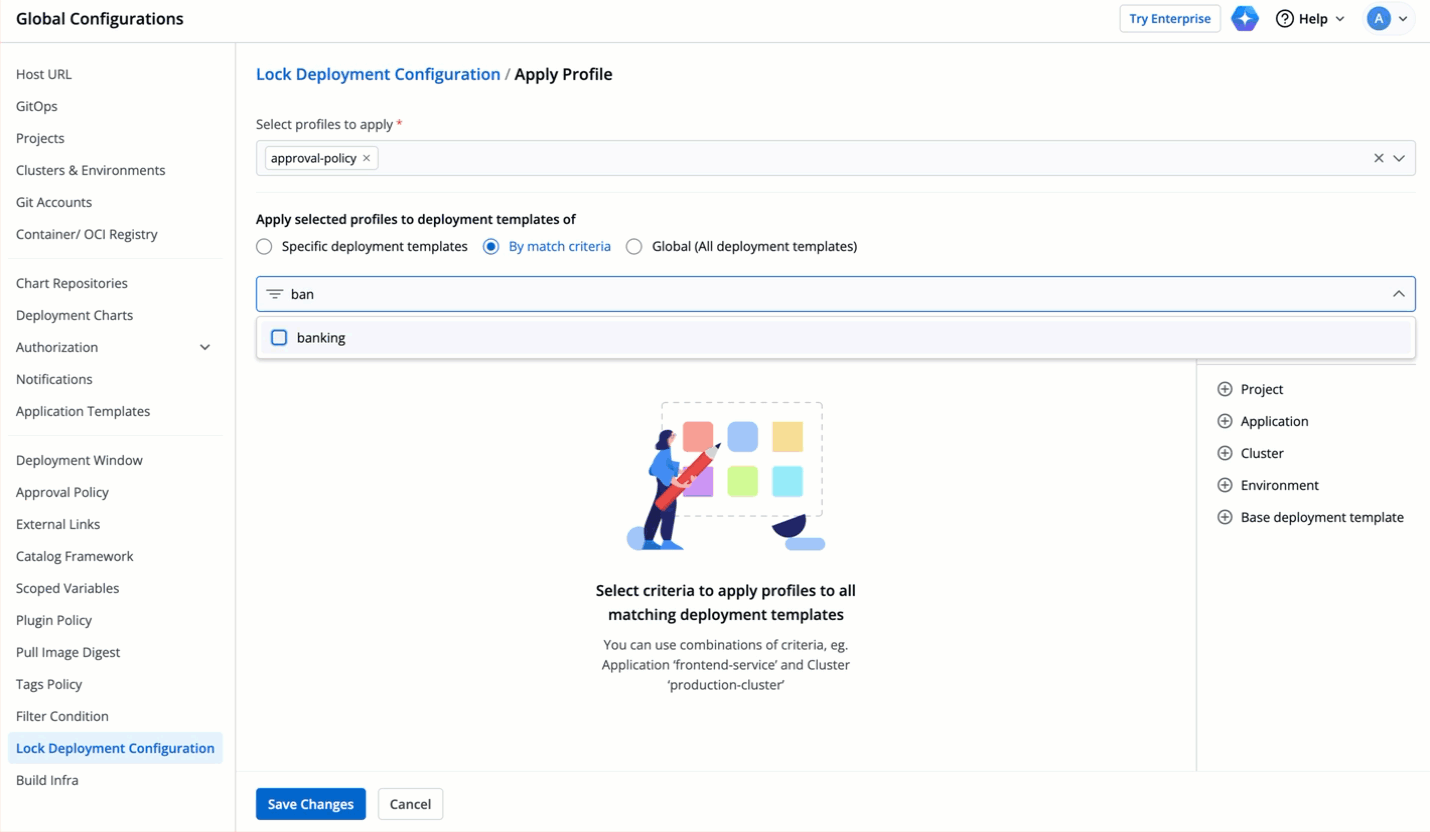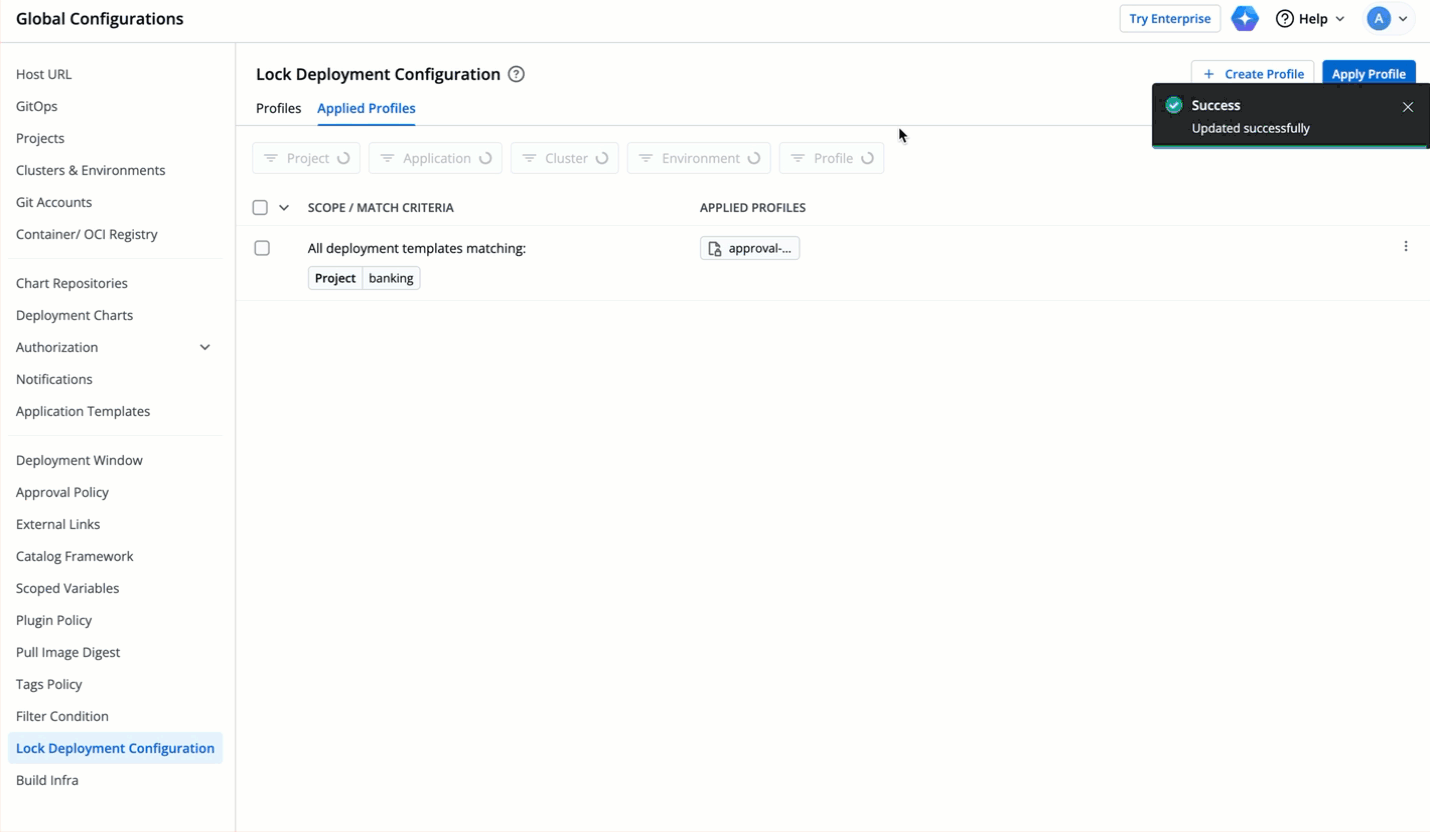 |
| 122 | + |
| 123 | + 3. **Global (All deployment templates)**: This option allows you to apply the lock deployment configuration profile to all the existing and future deployment templates across all the applications. |
| 124 | + |
| 125 | + 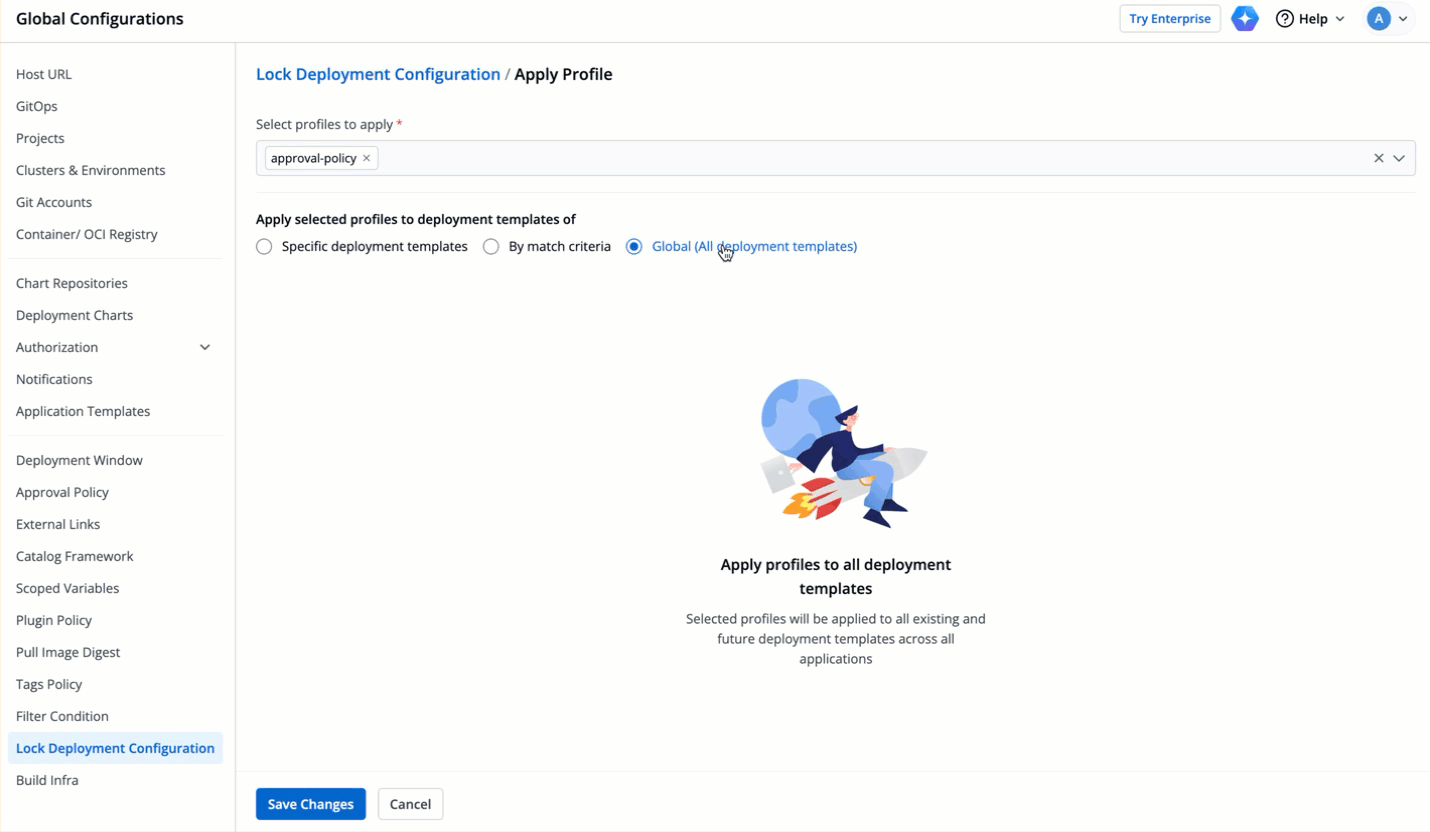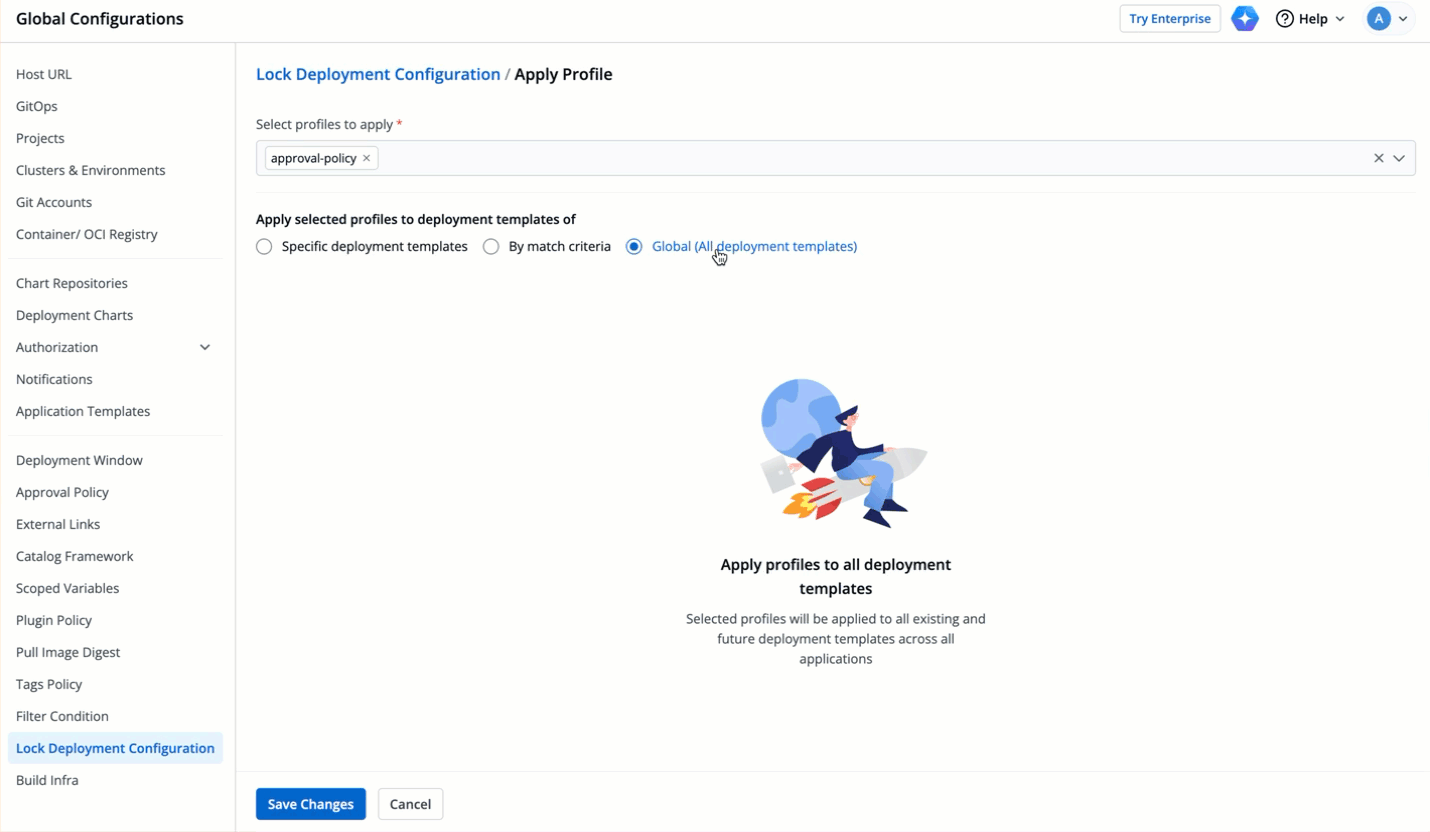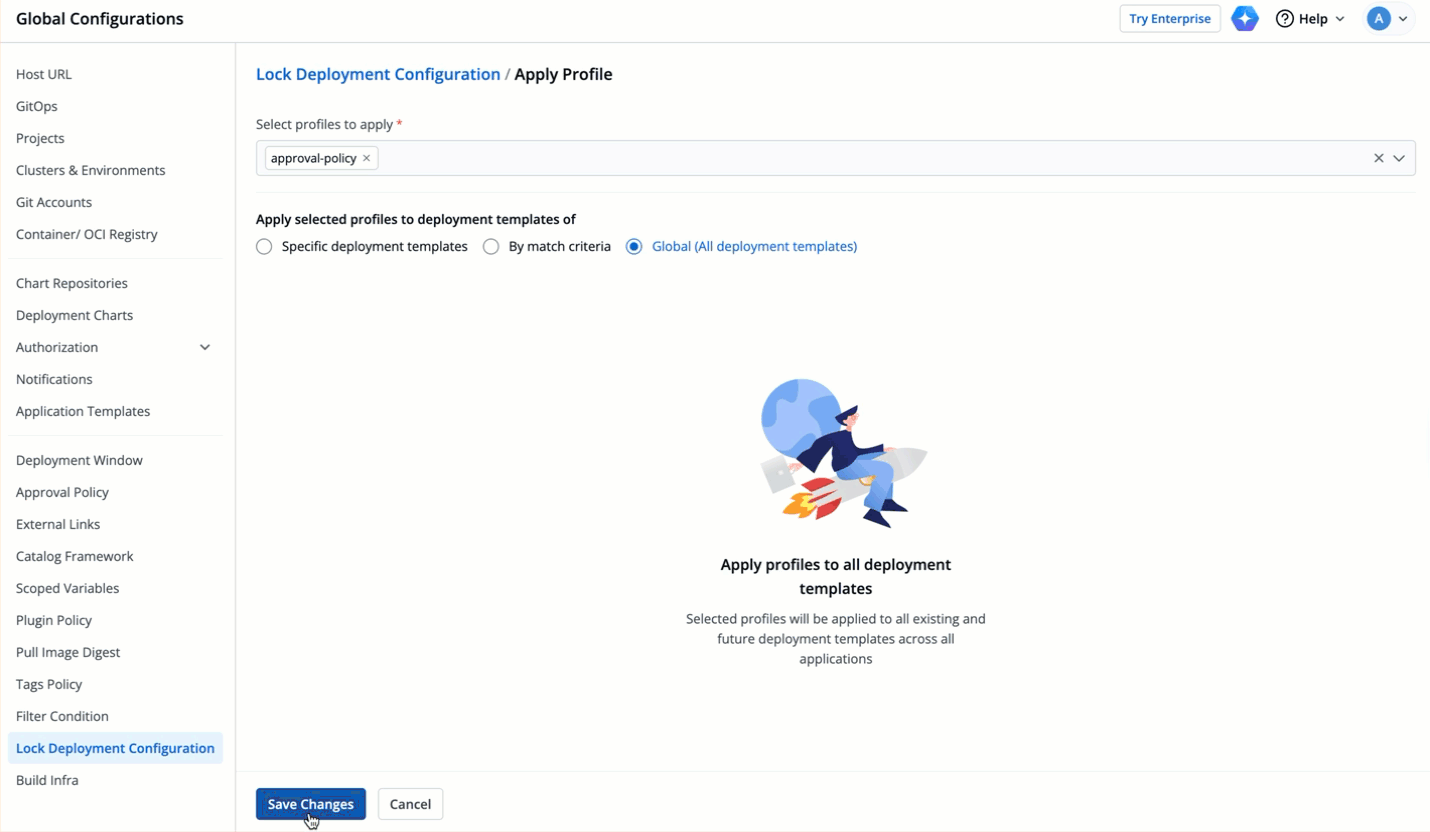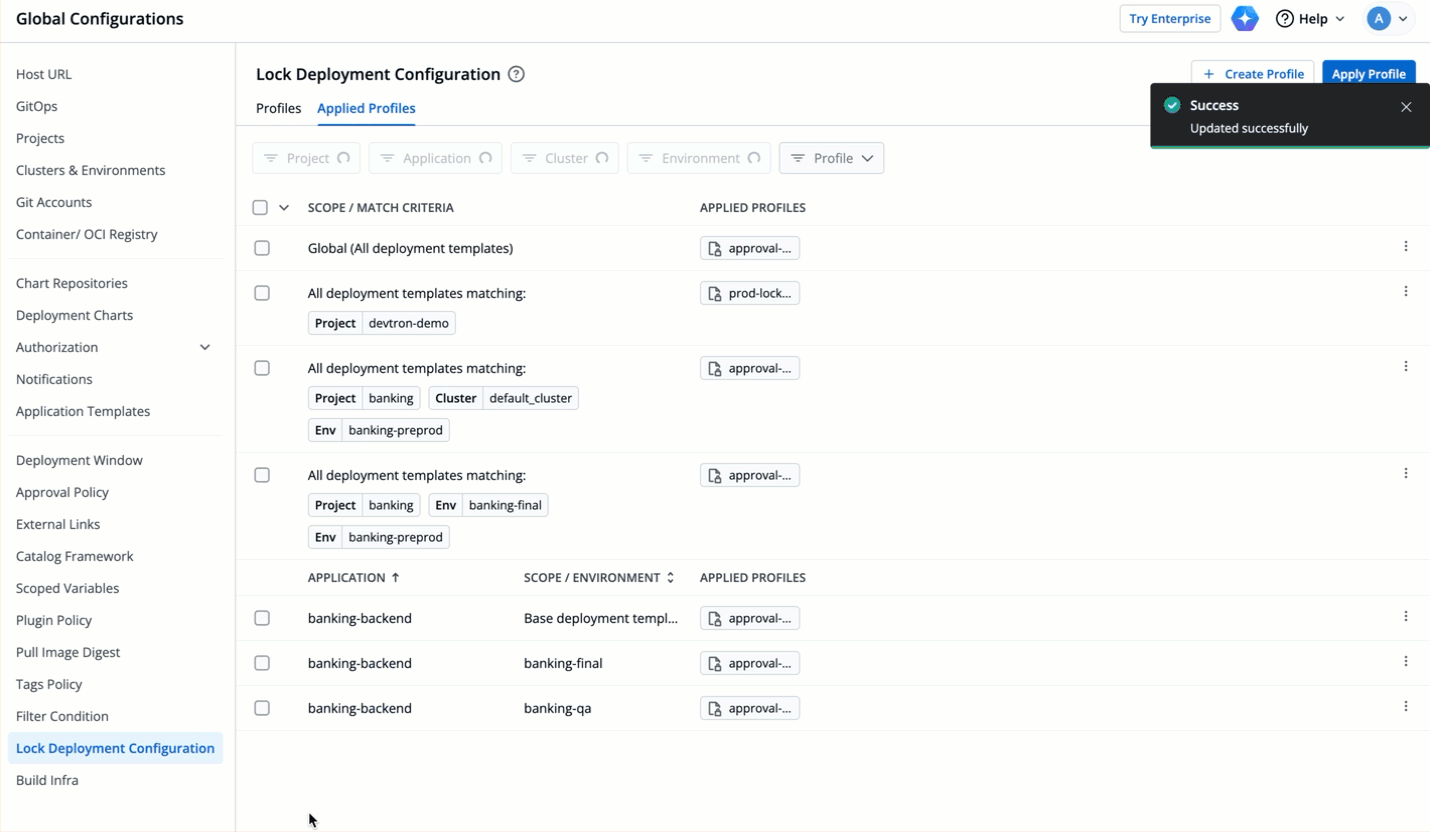 |
| 126 | + |
| 127 | +5. Click **Save Changes**, and the selected profiles will apply to the required deployment templates and be visible under the **Applied Profiles** tab. |
| 128 | + |
50 | 129 | --- |
51 | 130 |
|
52 | | -## Result |
| 131 | +## Effect on Deployment Templates |
| 132 | + |
| 133 | +Only super admins can edit the locked configurations directly once the lock deployment configuration profile is applied to the deployment templates. Non-super admin users cannot edit the locked keys for those deployment templates. |
53 | 134 |
|
54 | | -While super-admins can directly edit the locked keys, let's look at a scenario where a user (non-super-admin) tries to edit the same in an [unprotected](../../user-guide/creating-application/config-approval.md) base deployment template. |
| 135 | +Let's look at a scenario where a user (non-super-admin) tries to edit the same in an [unprotected](../../user-guide/creating-application/config-approval.md) base deployment template. |
55 | 136 |
|
56 | | -* User can hide/unhide the locked keys as shown below. |
57 | 137 |
|
58 | | - 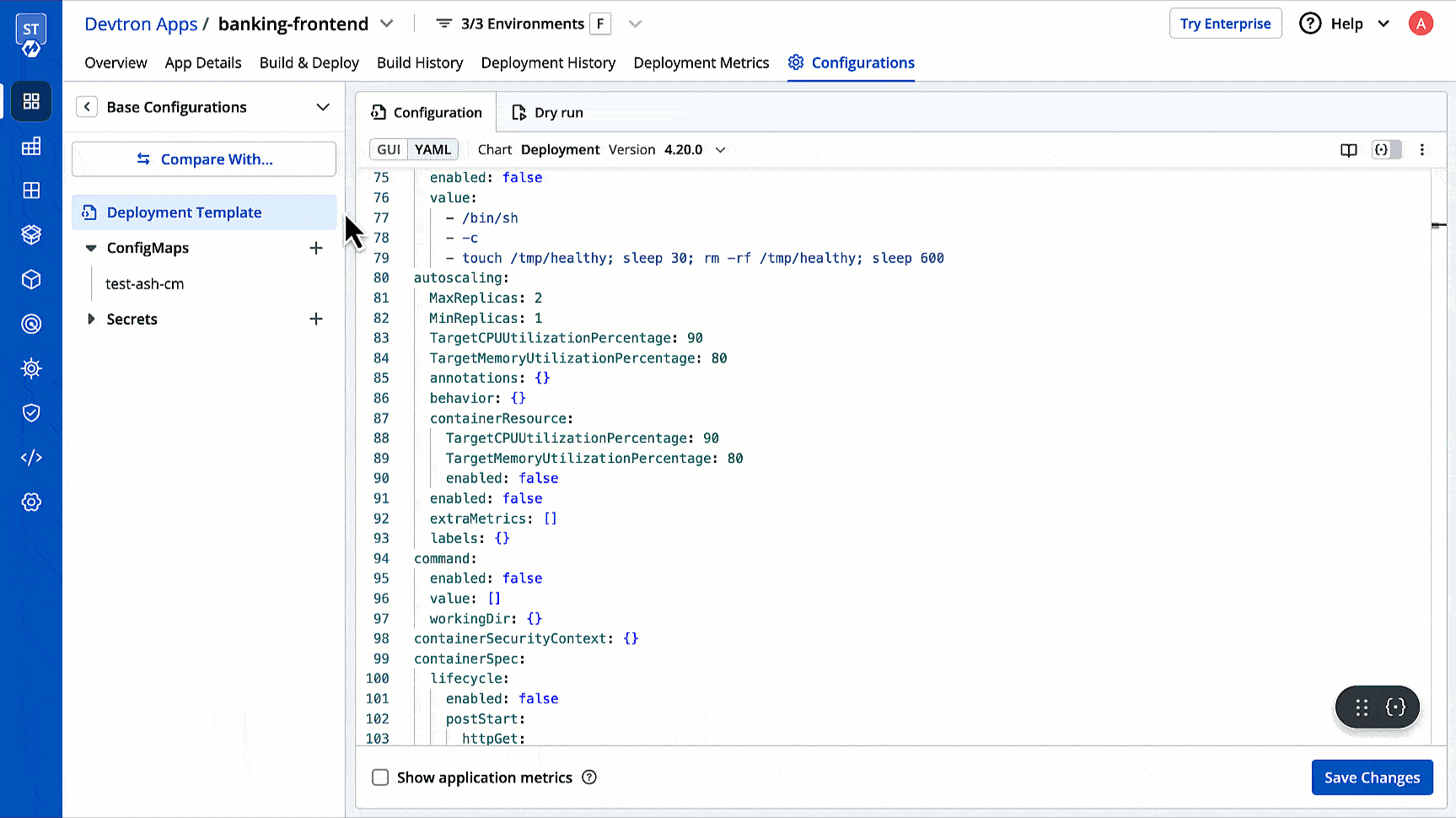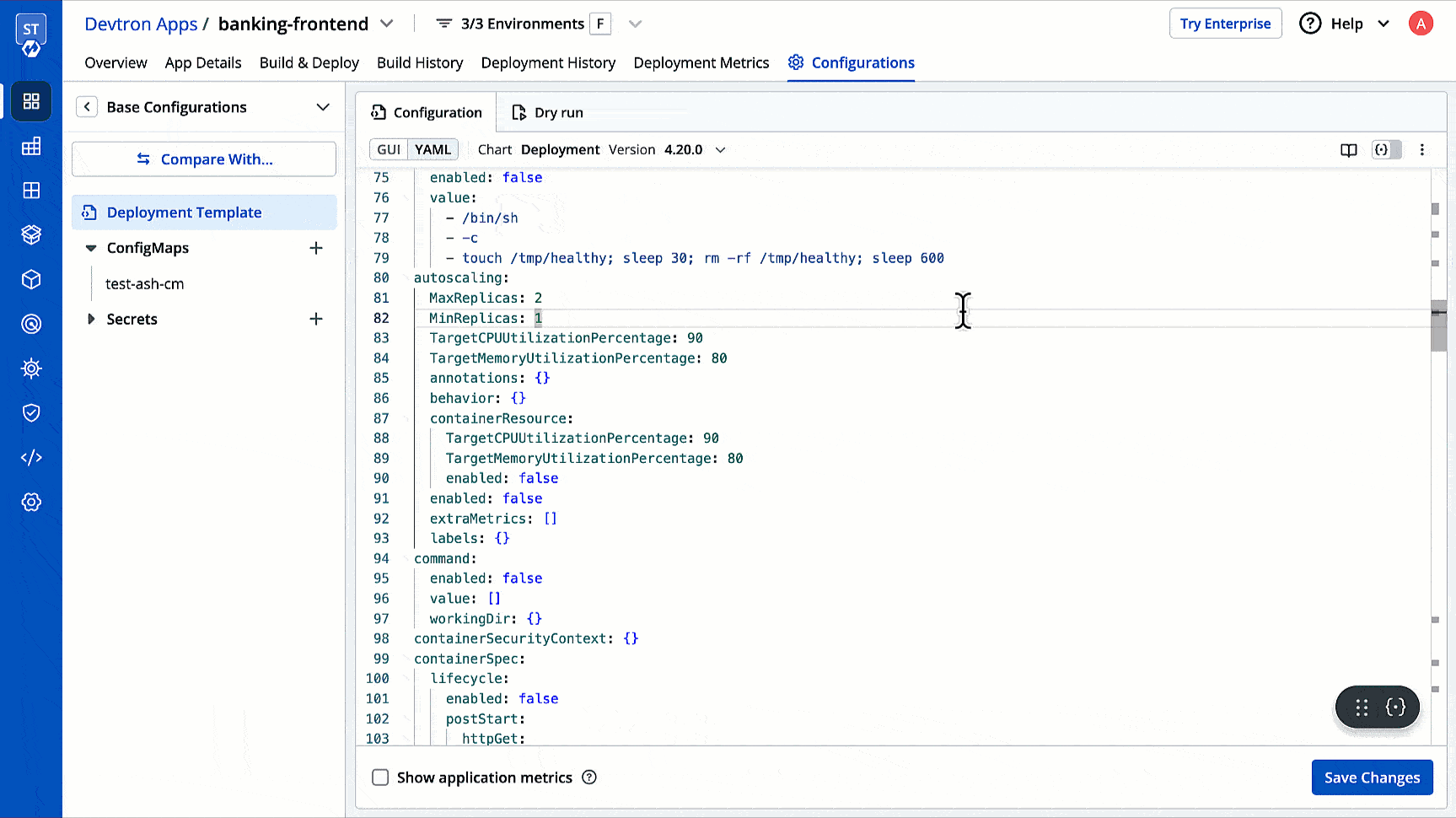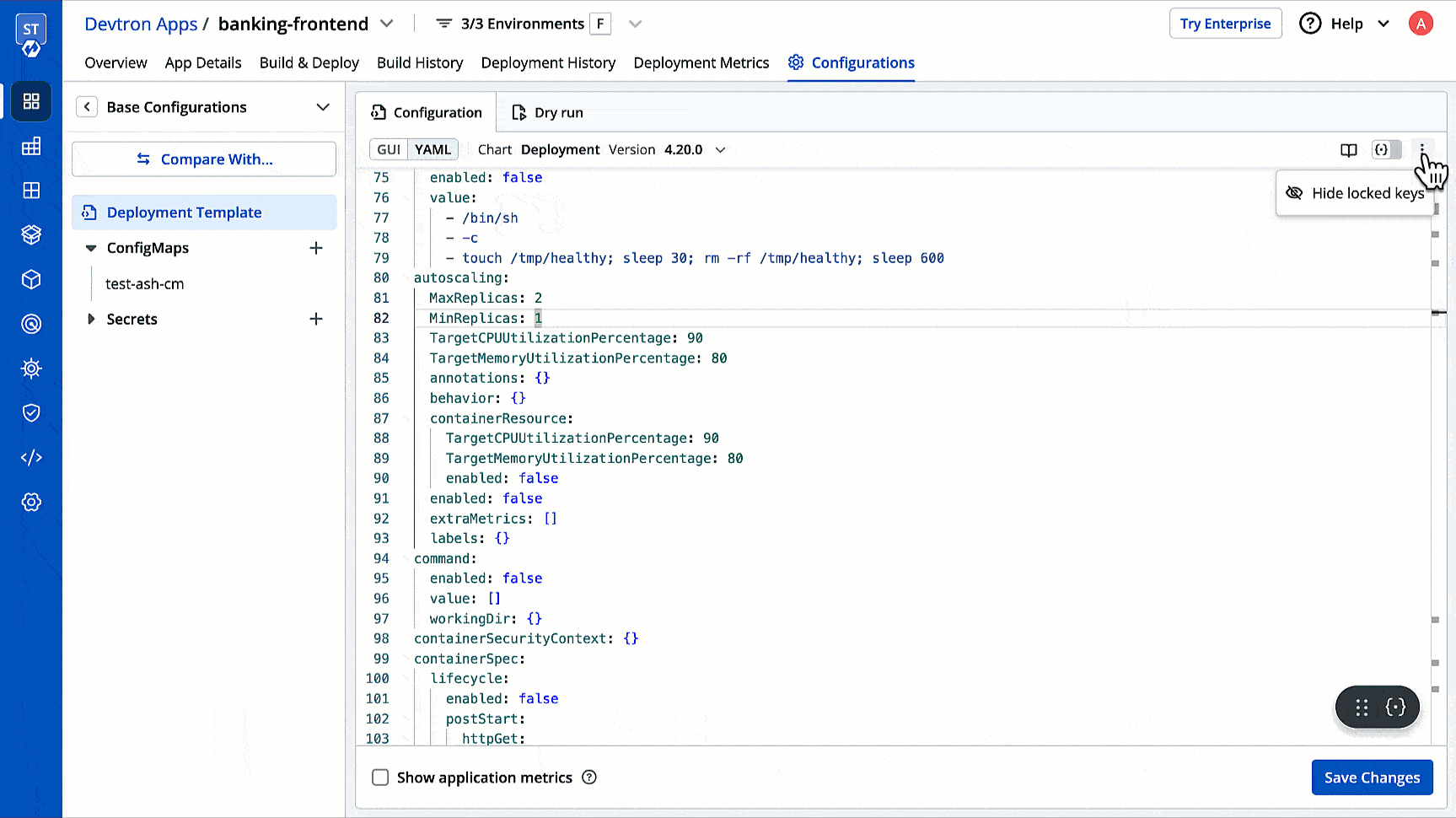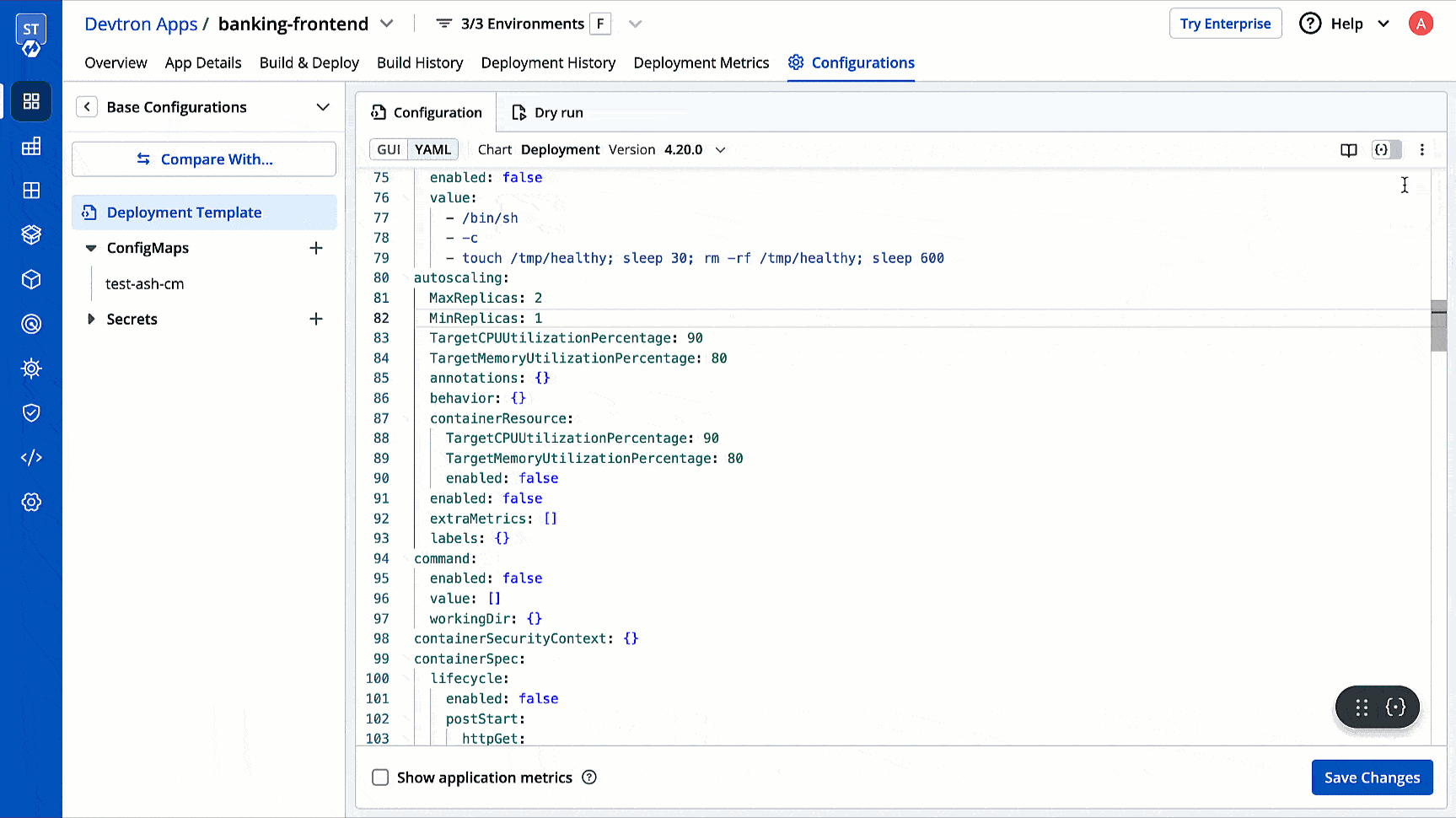 |
| 138 | +### Viewing Locked Configurations |
| 139 | + |
| 140 | +* User can hide/unhide the locked configurations as shown below. |
| 141 | + |
| 142 | +  |
| 143 | + |
| 144 | +### Editing Locked Configurations |
59 | 145 |
|
60 | 146 | {% hint style="info" %} |
61 | | -<span><img src="https://devtron-public-asset.s3.us-east-2.amazonaws.com/images/global-configurations/lock-dt/mode.jpg" alt="GUI or YAML Mode"></span> <br /> |
62 | | -If you select 'Basic' mode instead of 'Advanced (YAML)', all the keys meant for basic mode will be displayed in the GUI even if some are locked. While users can modify these keys, they cannot save the changes made to the locked keys. |
| 147 | +### GUI/YAML Mode |
| 148 | +<span><img src="https://devtron-public-asset.s3.us-east-2.amazonaws.com/images/global-configurations/lock-dt/mode1.jpg" alt="GUI or YAML Mode"></span> <br /> |
| 149 | +If you select 'GUI' mode instead of 'YAML', all the keys meant for GUI mode will be displayed in the GUI even if some are locked. While users can modify these keys, they cannot save the changes made to the locked keys. |
63 | 150 | {% endhint %} |
64 | 151 |
|
65 | 152 | * Let's assume the user edits one of the locked keys... |
66 | 153 |
|
67 | | - 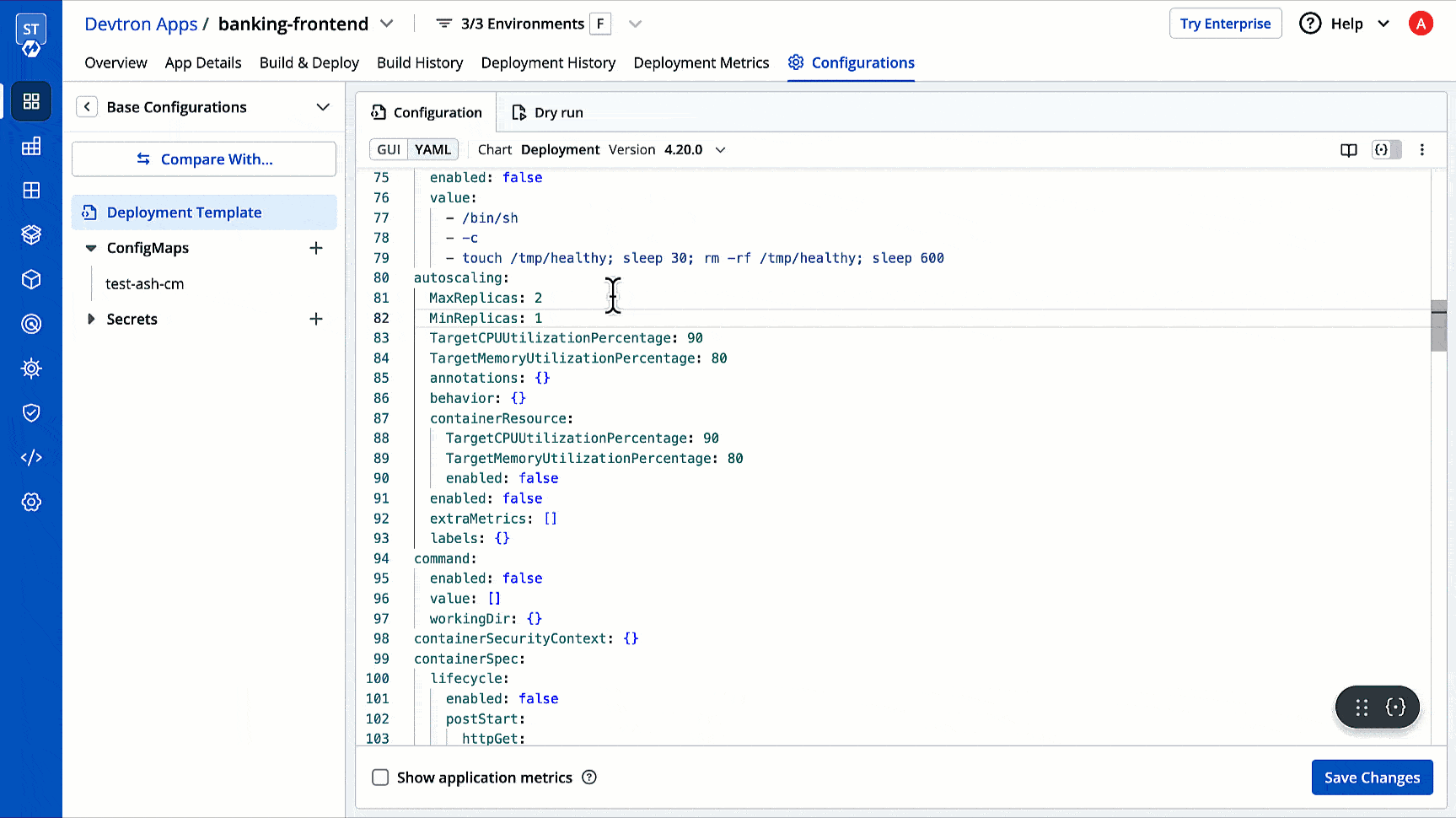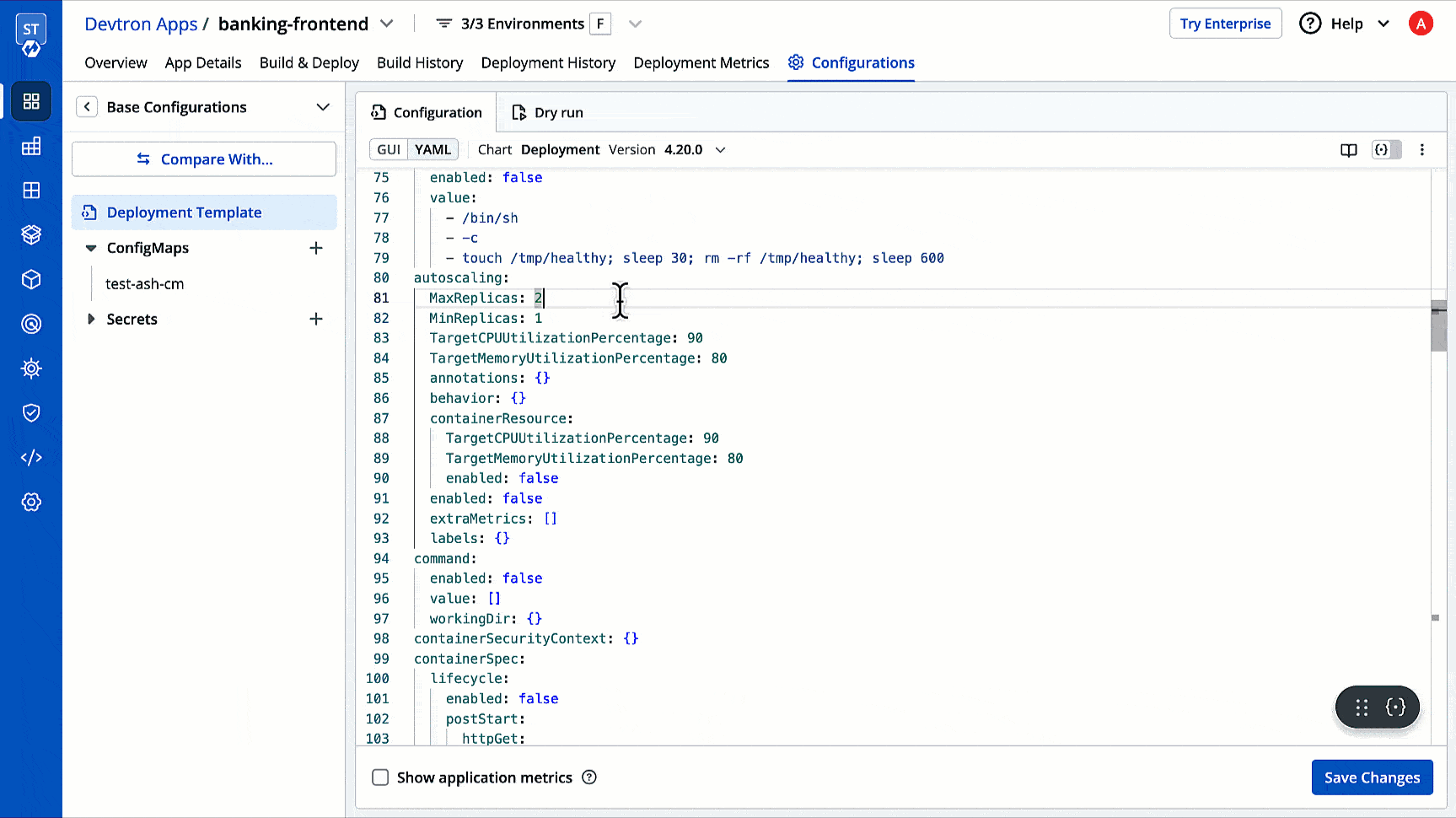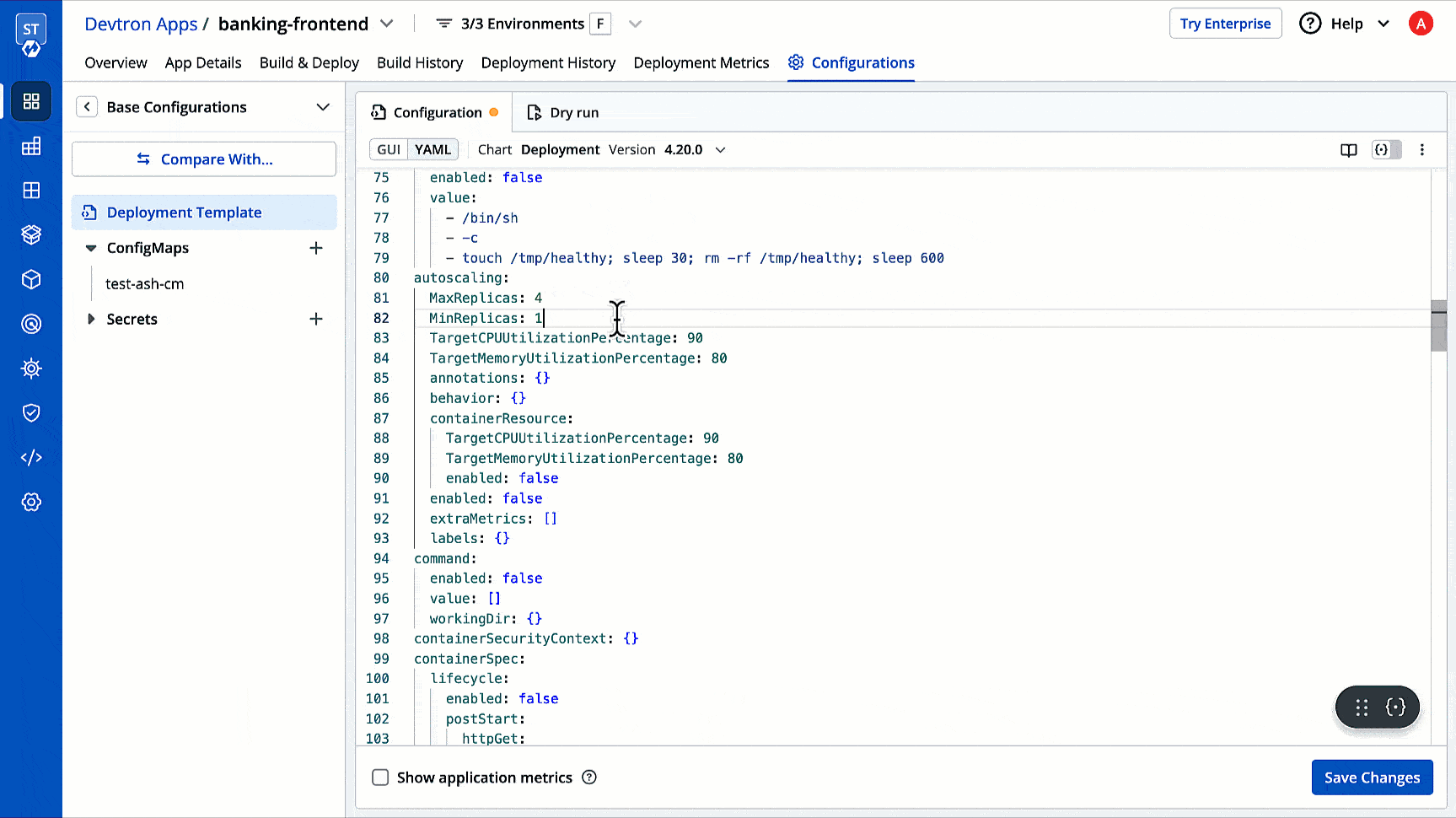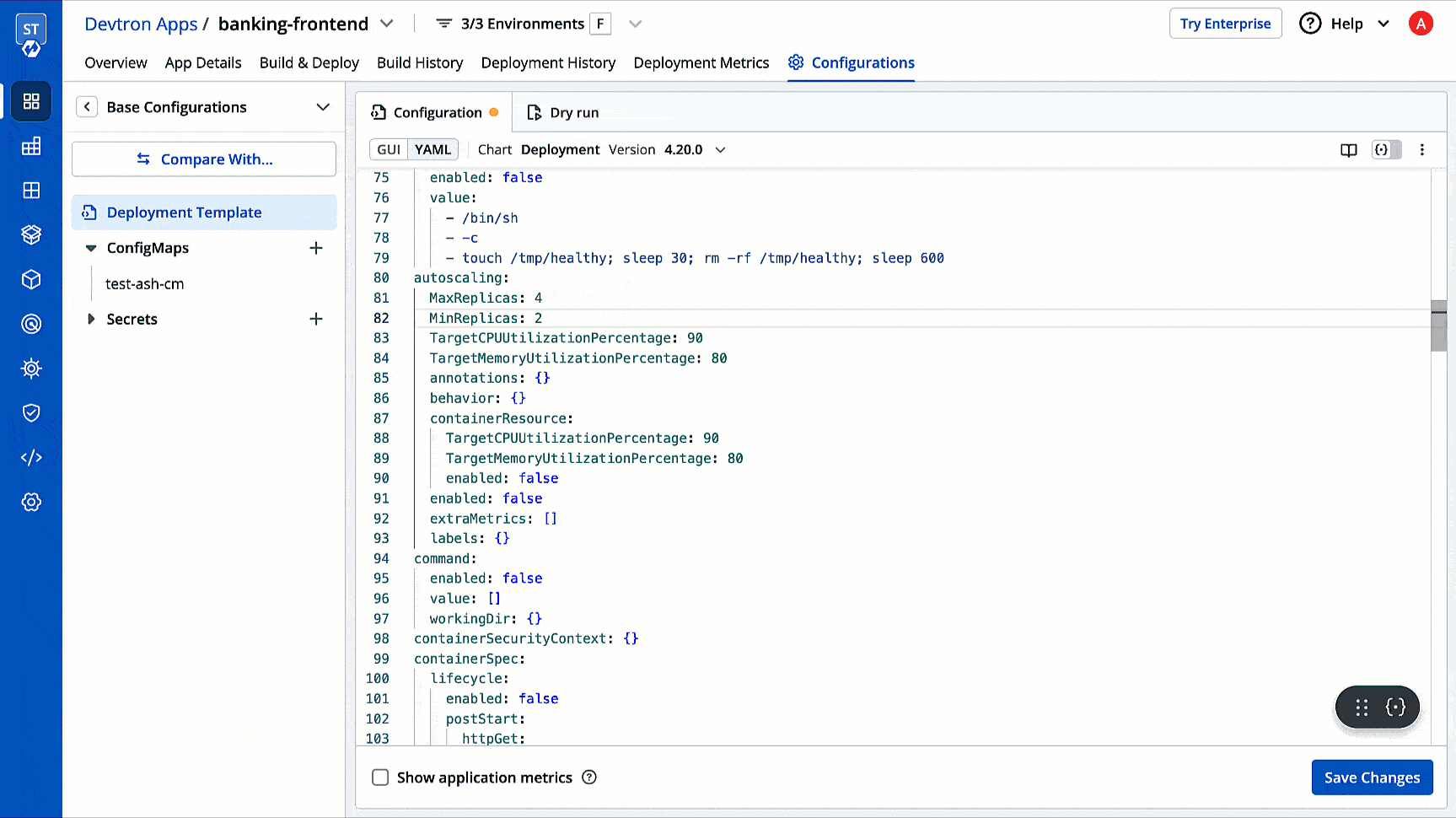 |
| 154 | +  |
68 | 155 |
|
69 | 156 | ...and saves the changes. |
70 | 157 |
|
71 | | - 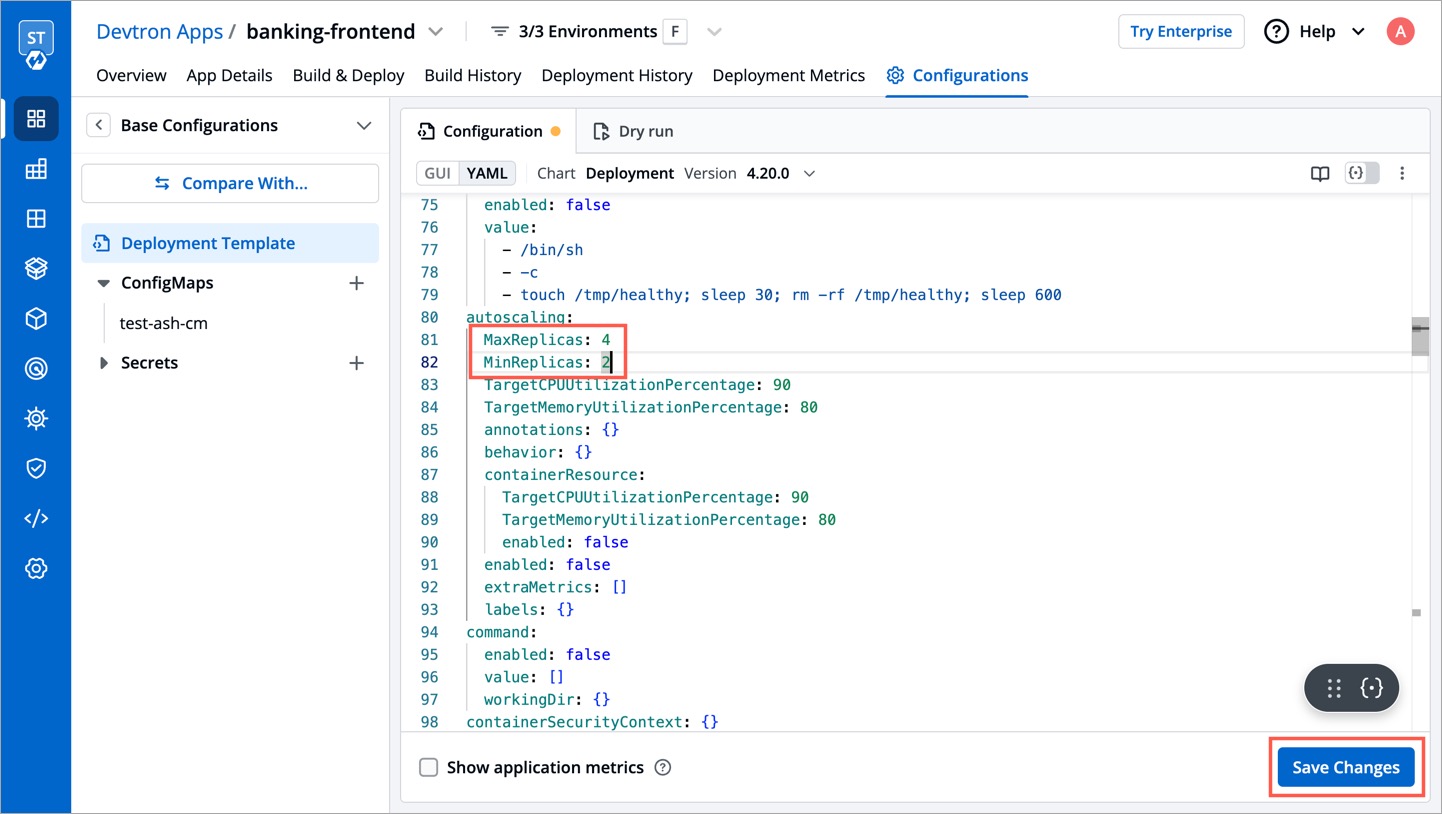 |
| 158 | +  |
72 | 159 |
|
73 | | -* A modal window will appear on the right highlighting the non-eligible edits. |
| 160 | +* A modal window highlighting the non-eligible edits will appear on the right. |
74 | 161 |
|
75 | | -  |
| 162 | +  |
| 163 | + |
| 164 | +### Editing Unlocked Keys |
76 | 165 |
|
77 | 166 | * Let's assume the user edits a key that is not locked or adds a new key. |
78 | 167 |
|
79 | | - 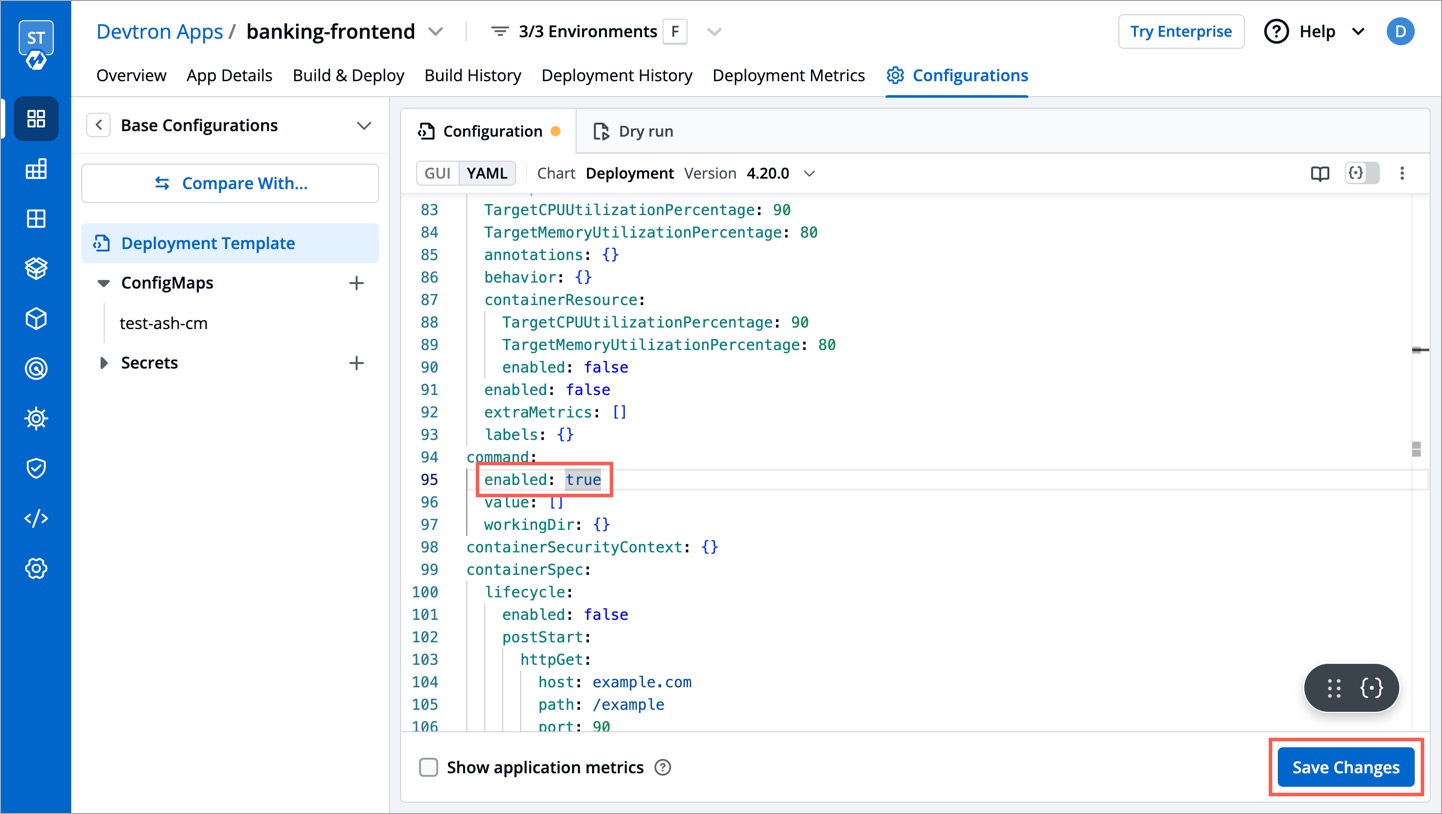 |
| 168 | +  |
80 | 169 |
|
81 | 170 | * The modal window will highlight the eligible edits. However, it will not let the user save those eligible edits unless the user clicks the checkbox: **Save changes which are eligible for update**. |
82 | 171 |
|
83 | | - 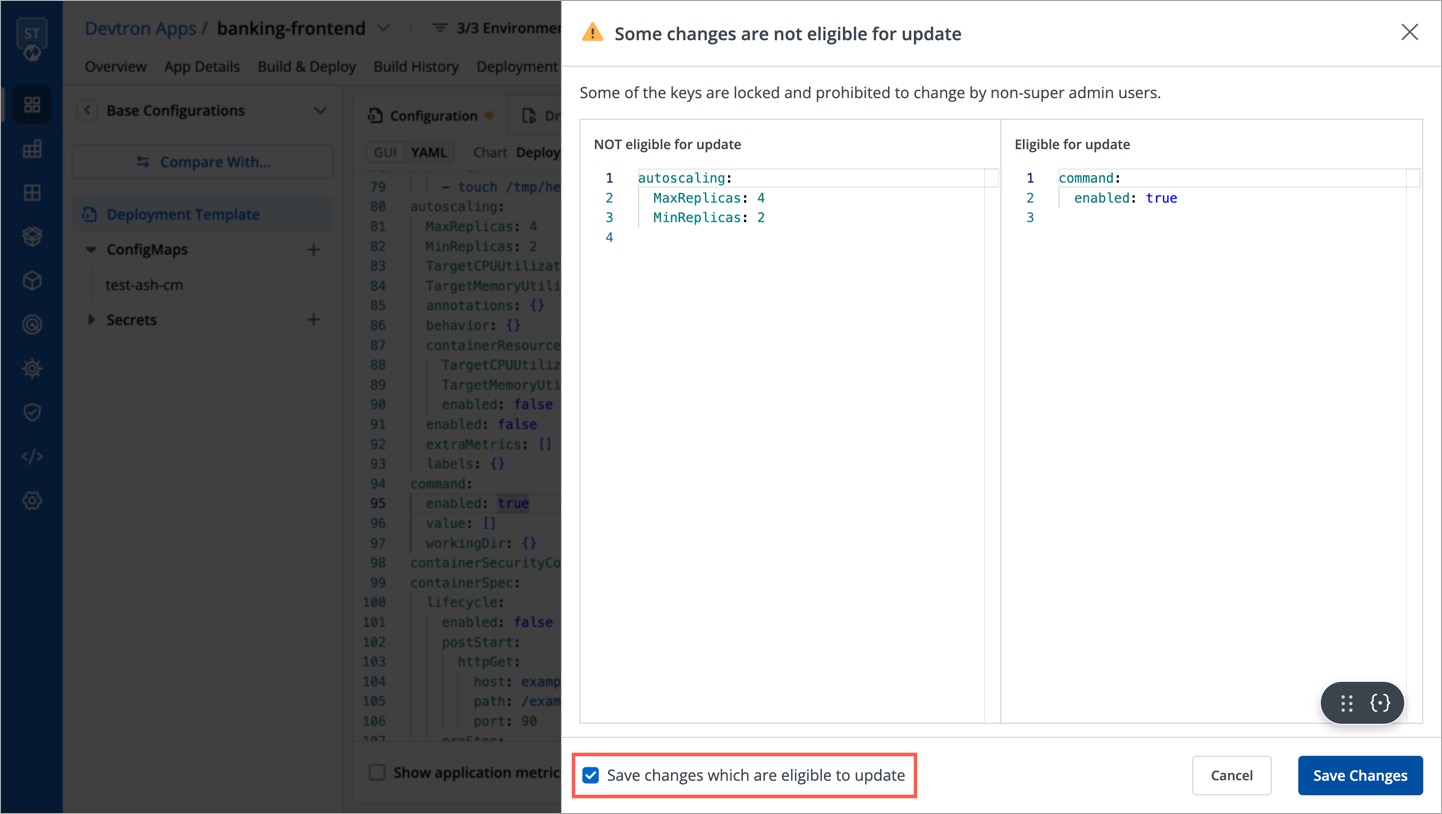 |
| 172 | +  |
84 | 173 |
|
85 | 174 | {% hint style="warning" %} |
86 | 175 | ### Who Can Perform This Action? |
87 | 176 | Only a super-admin, manager, or application admin can edit the configuration values. |
88 | 177 | {% endhint %} |
89 | 178 |
|
90 | | -* Once the user clicks the **Update** button, the permissible changes will reflect in the deployment template. |
| 179 | +* Once the user clicks the **Save Changes** button, the permissible changes will reflect in the deployment template. |
91 | 180 |
|
92 | | - 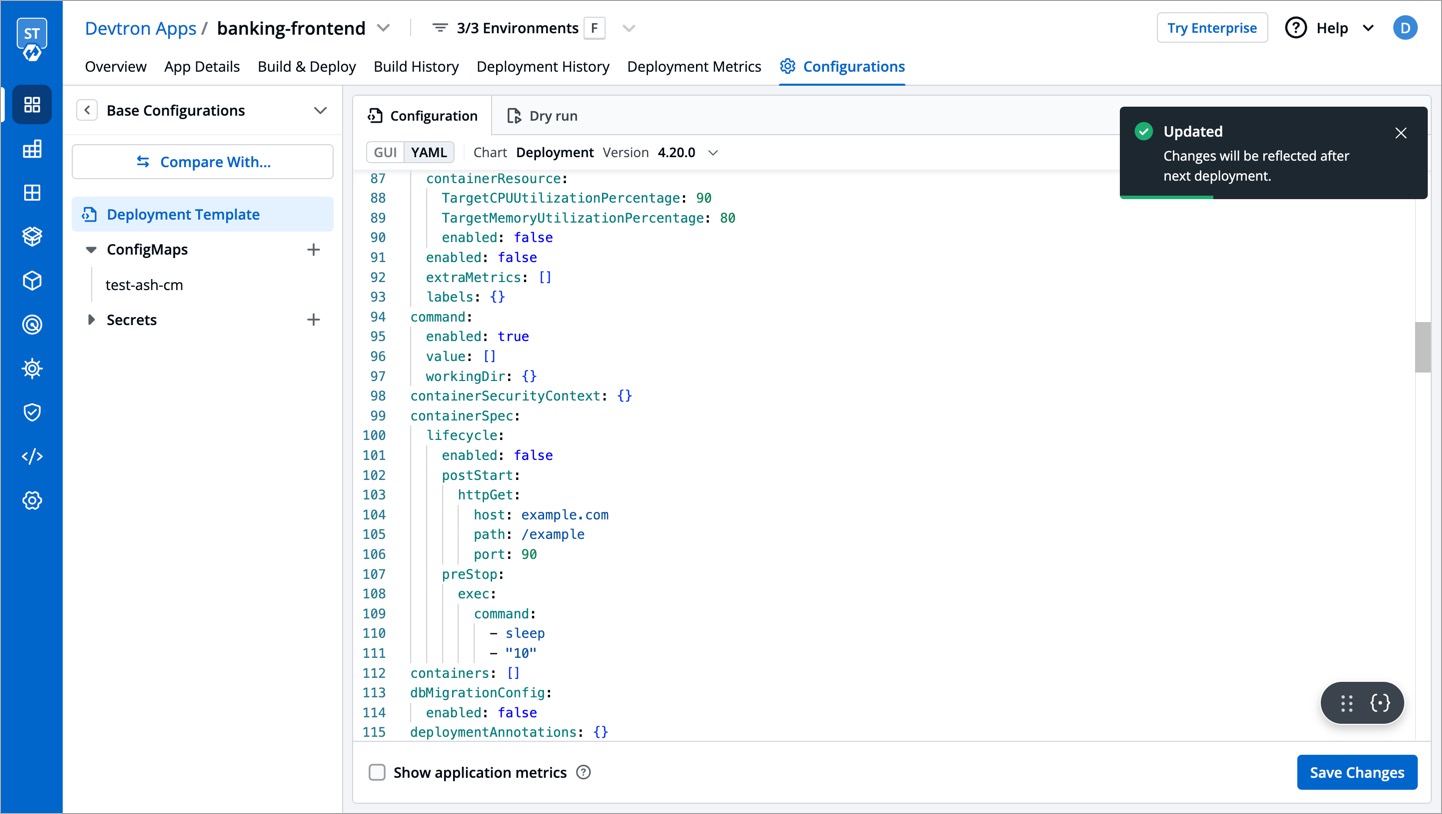 |
| 181 | +  |
93 | 182 |
|
94 | 183 | However, if it's a [protected template](../../user-guide/creating-application/config-approval.md), the user will require the approval of a [configuration approver](./user-access.md#devtron-apps-permissions) as shown below. |
95 | 184 |
|
96 | | - 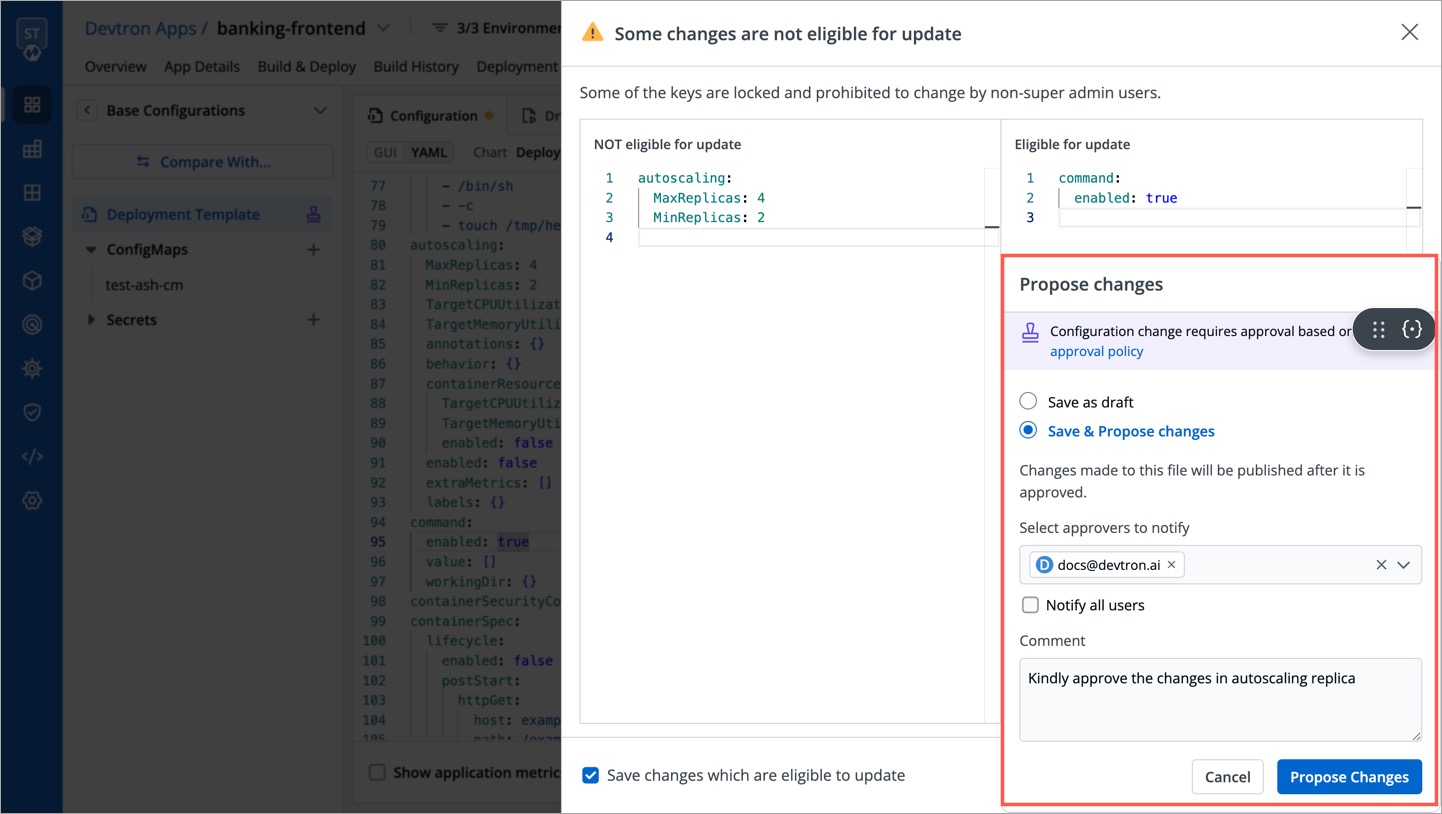 |
| 185 | +  |
97 | 186 |
|
98 | 187 | The same result can be seen if the user tries to edit environment-specific deployment templates. |
99 | 188 |
|
| 189 | +--- |
| 190 | + |
| 191 | +## Managing an Applied Profile |
| 192 | + |
| 193 | +To manage an existing applied profile, follow the steps below: |
| 194 | + |
| 195 | +1. Go to **Global Configurations** → **Lock Deployment Configuration**. |
| 196 | + |
| 197 | +2. Click the **Applied Profiles** tab and click the `⋮` button next to the preferred applied profile. |
| 198 | + |
| 199 | +3. Click **Manage Policy** to add or remove the profiles. If you have applied the profile using match criteria, then you can also click **Edit match criteria** to edit the match criteria. |
| 200 | + |
| 201 | +4. In case you want to delete an applied profile, click **Delete** and the applied profile will be removed. |
| 202 | + |
| 203 | +5. Click **Save Changes**. |
| 204 | + |
| 205 | +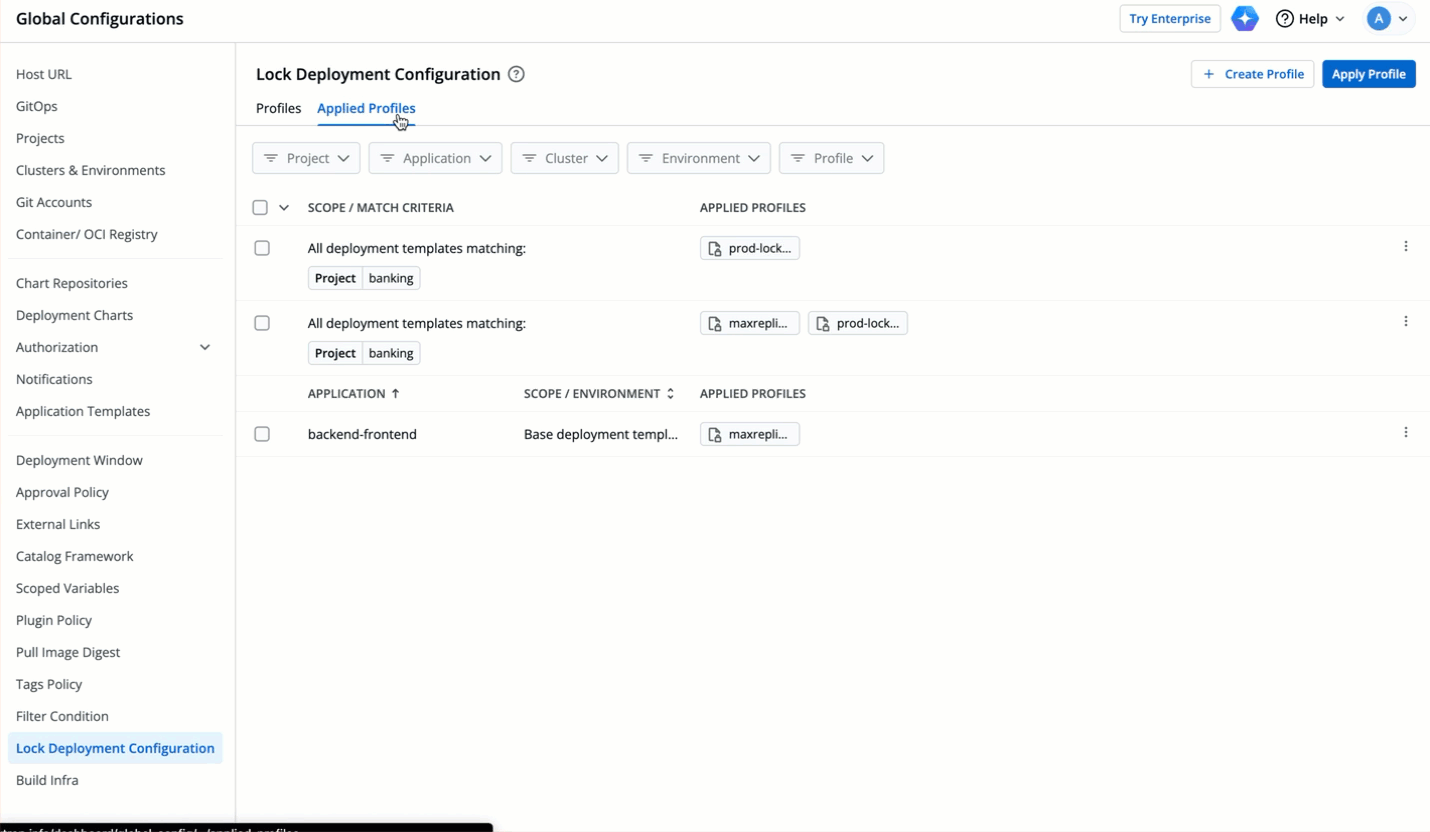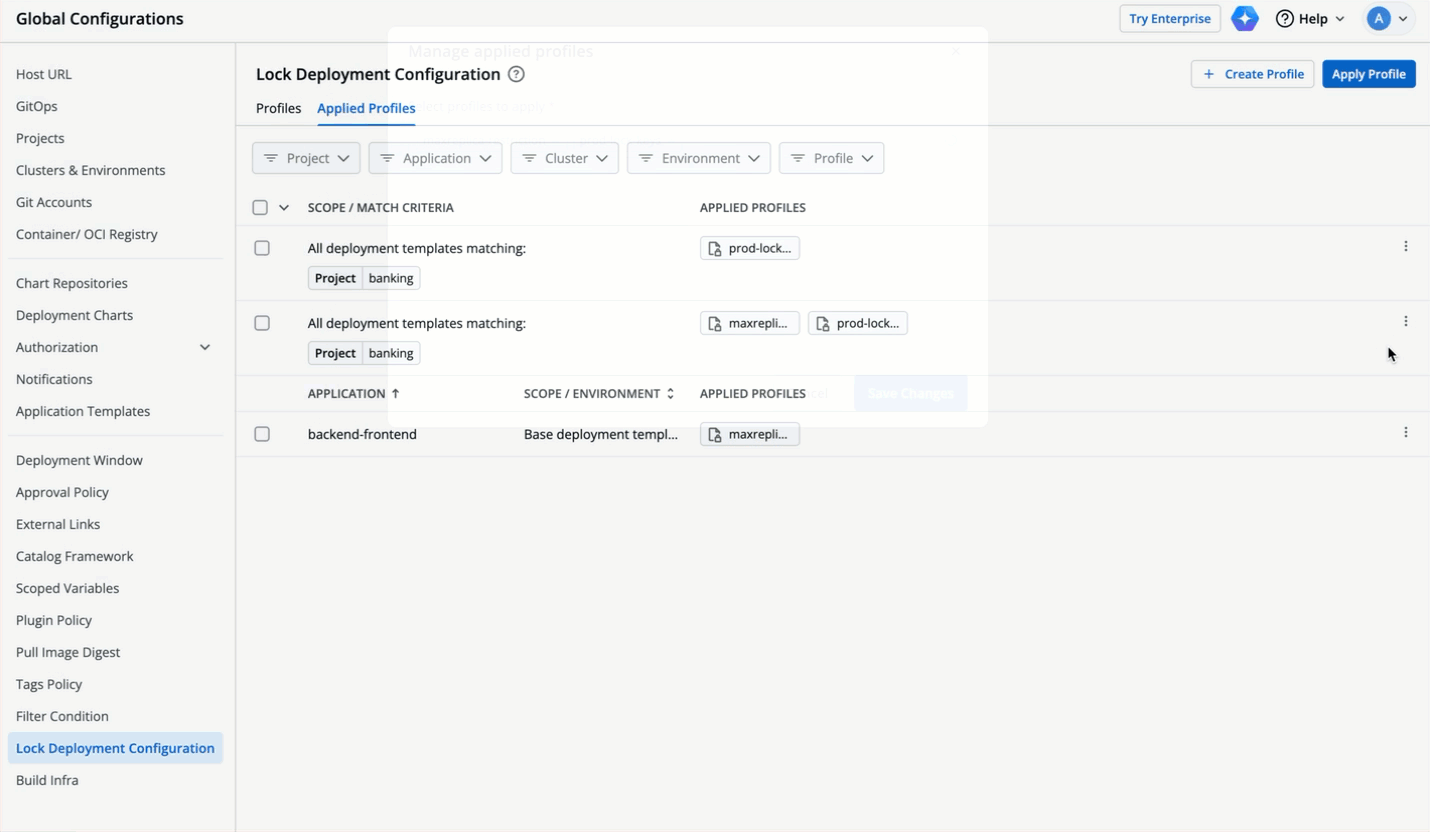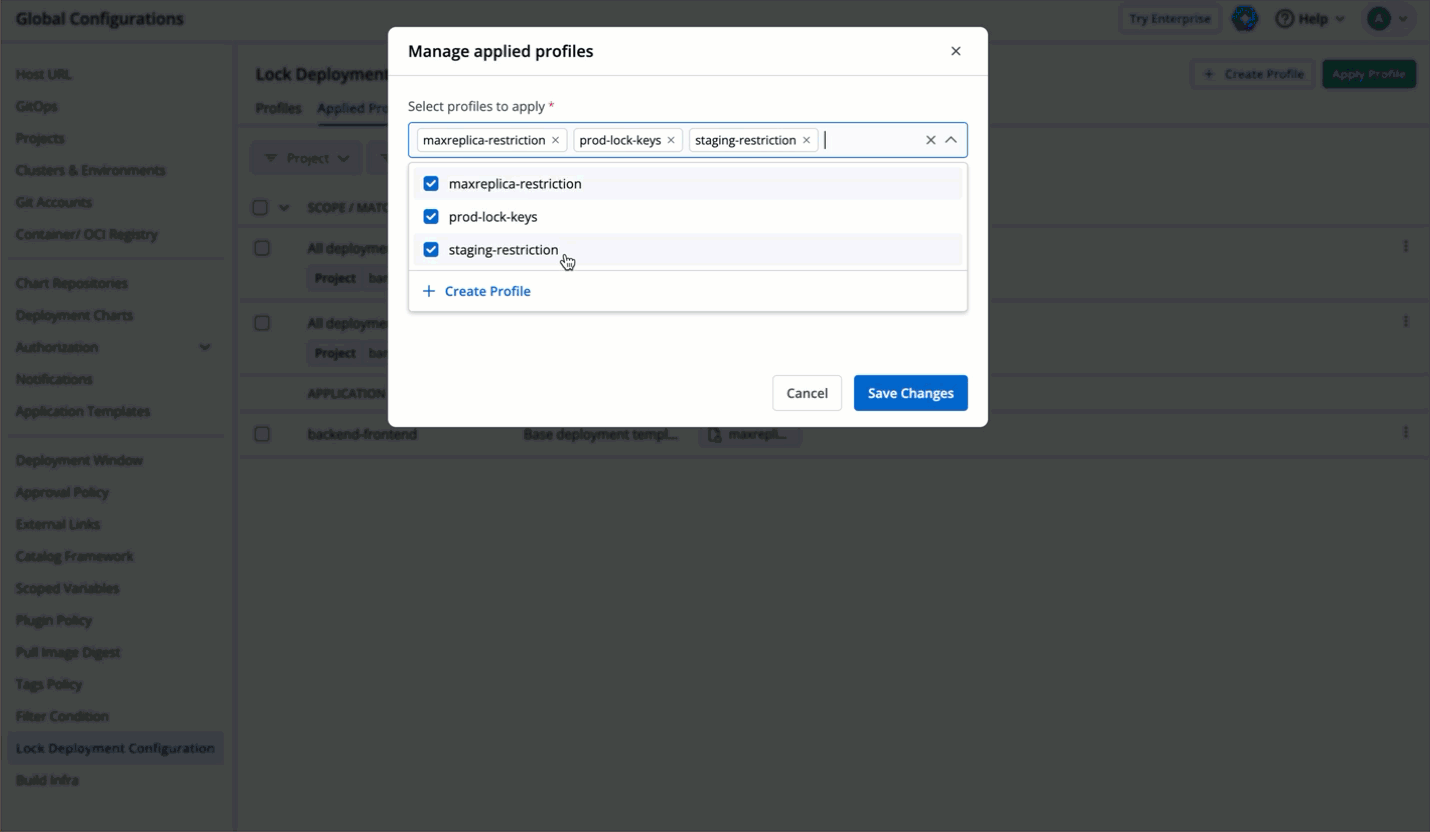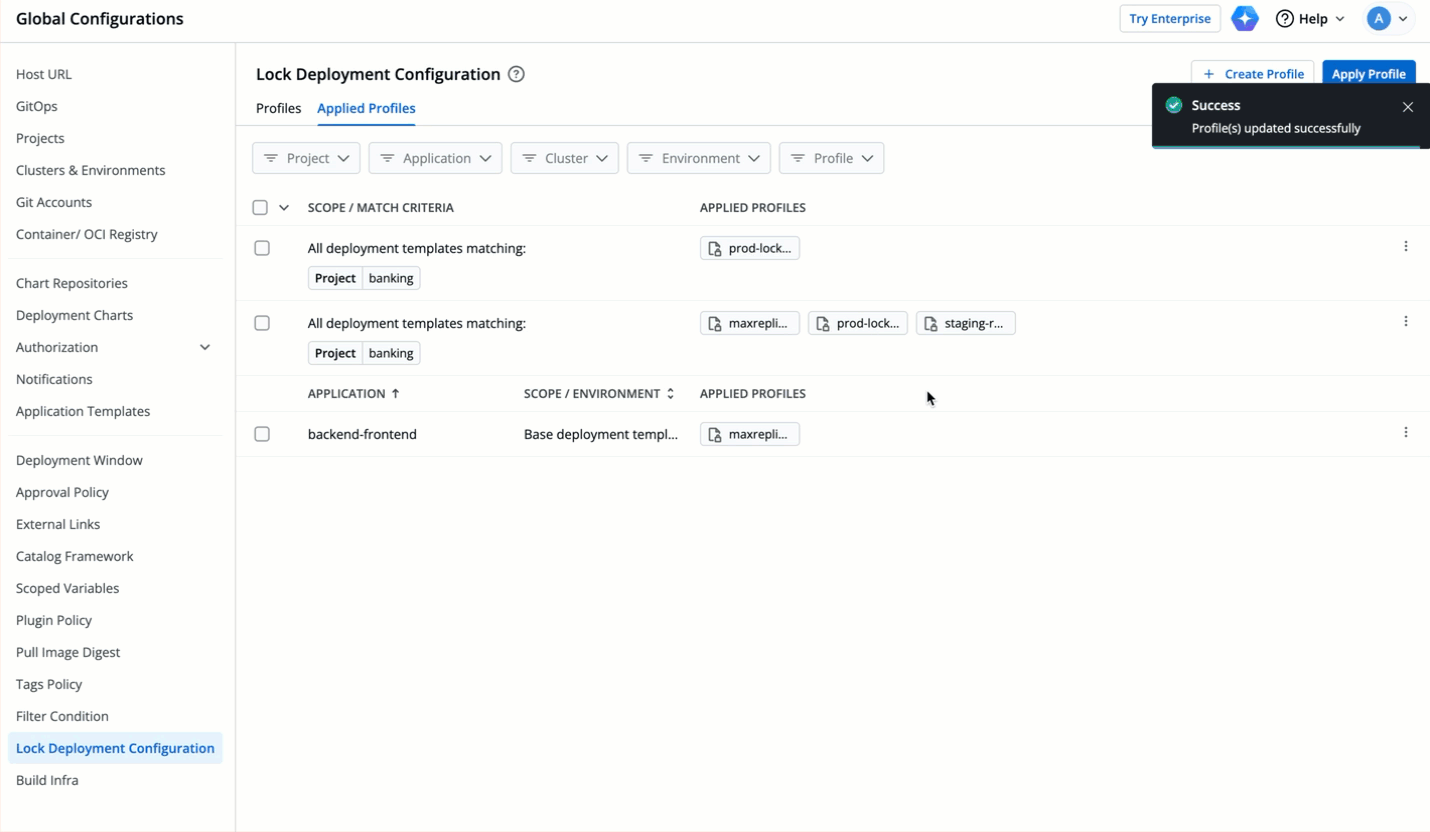 |
| 206 | + |
| 207 | +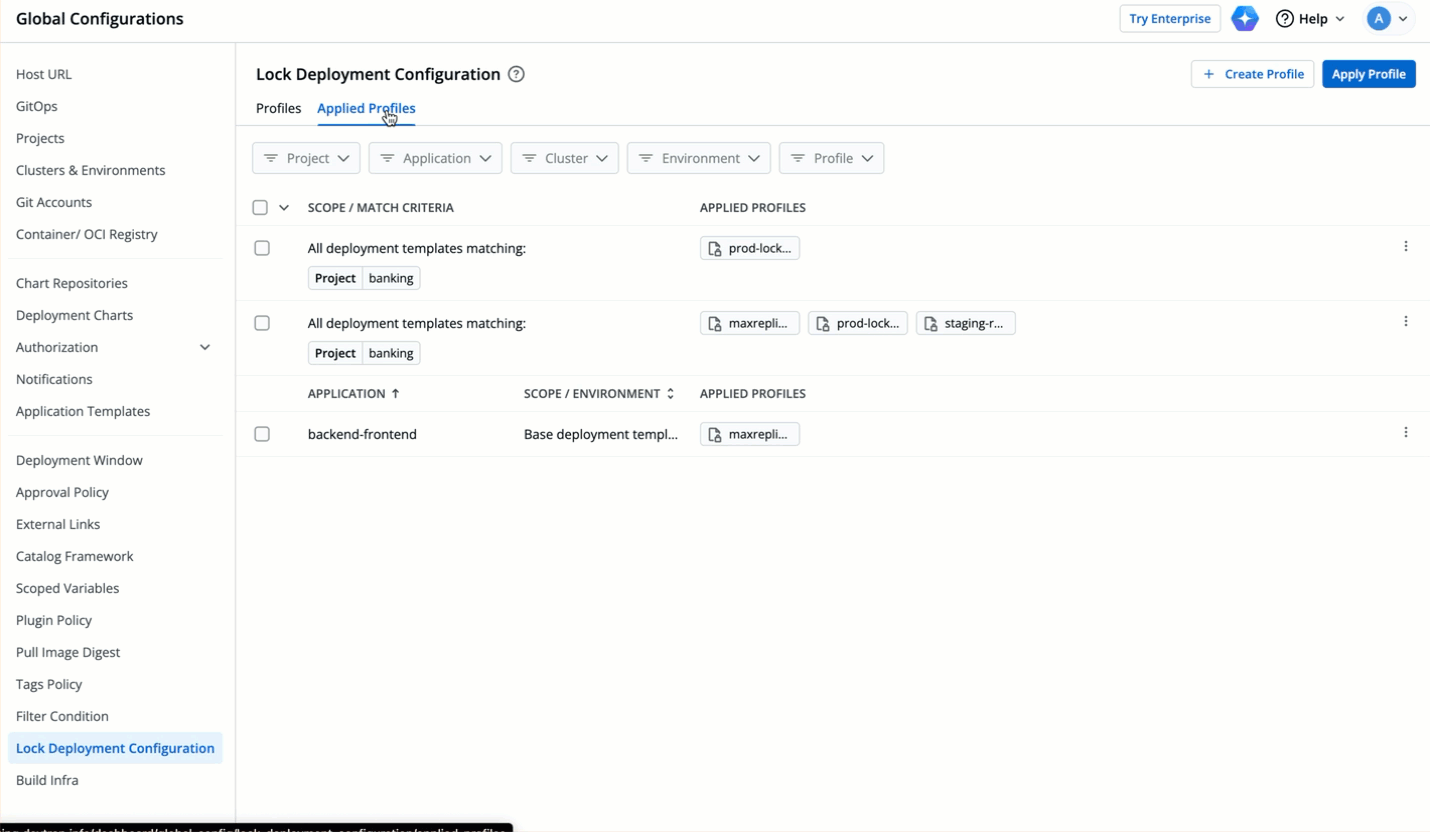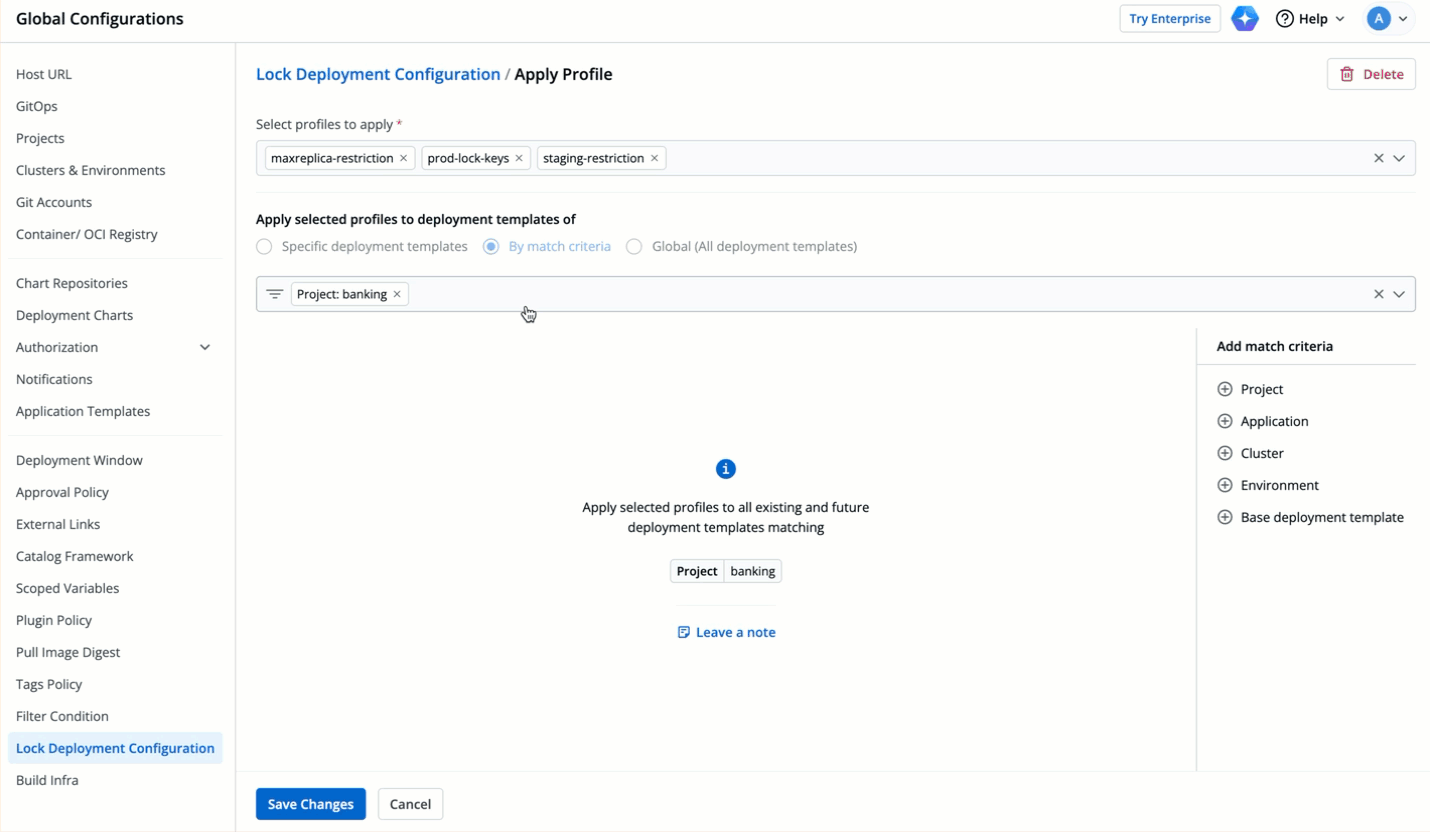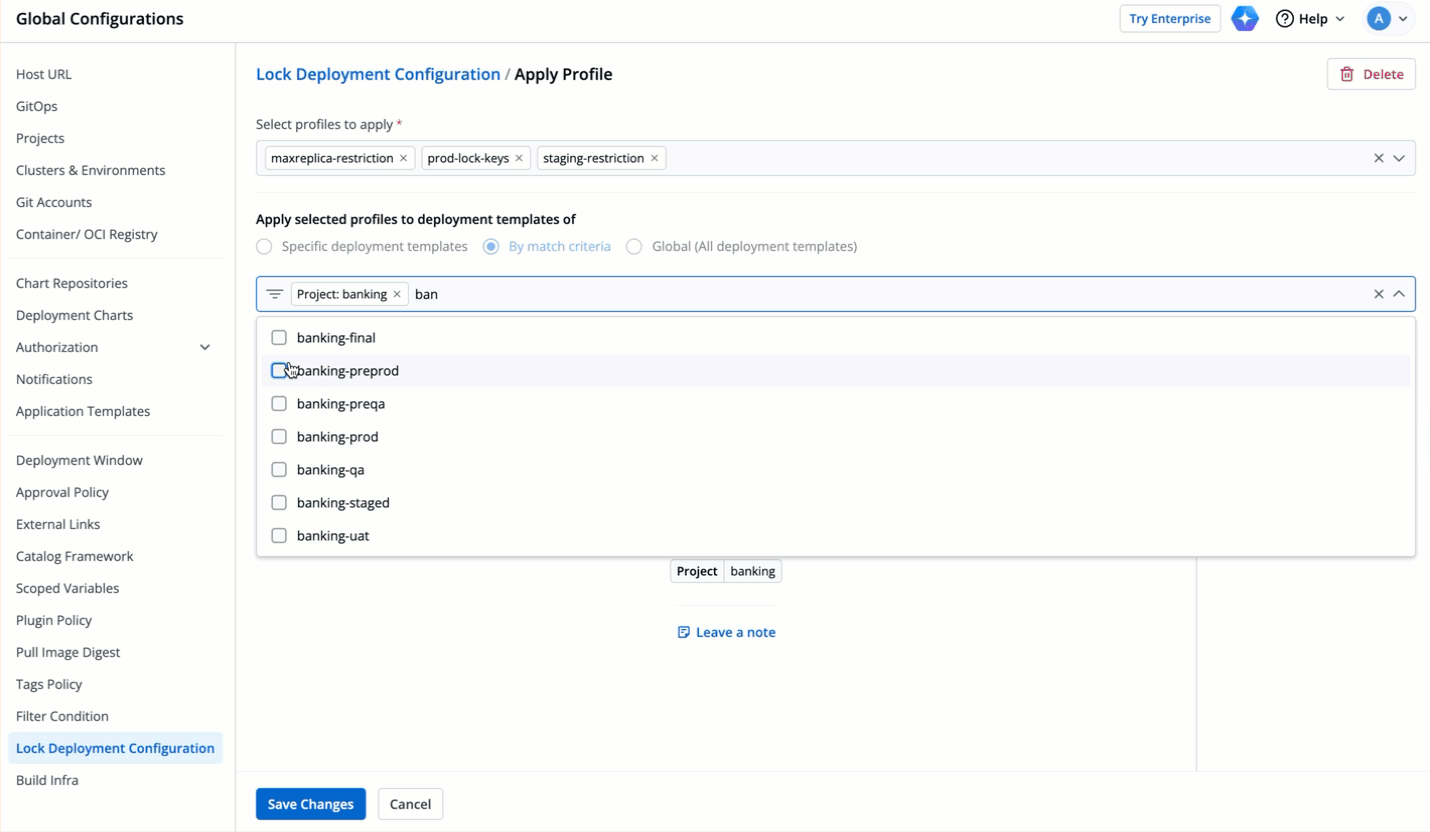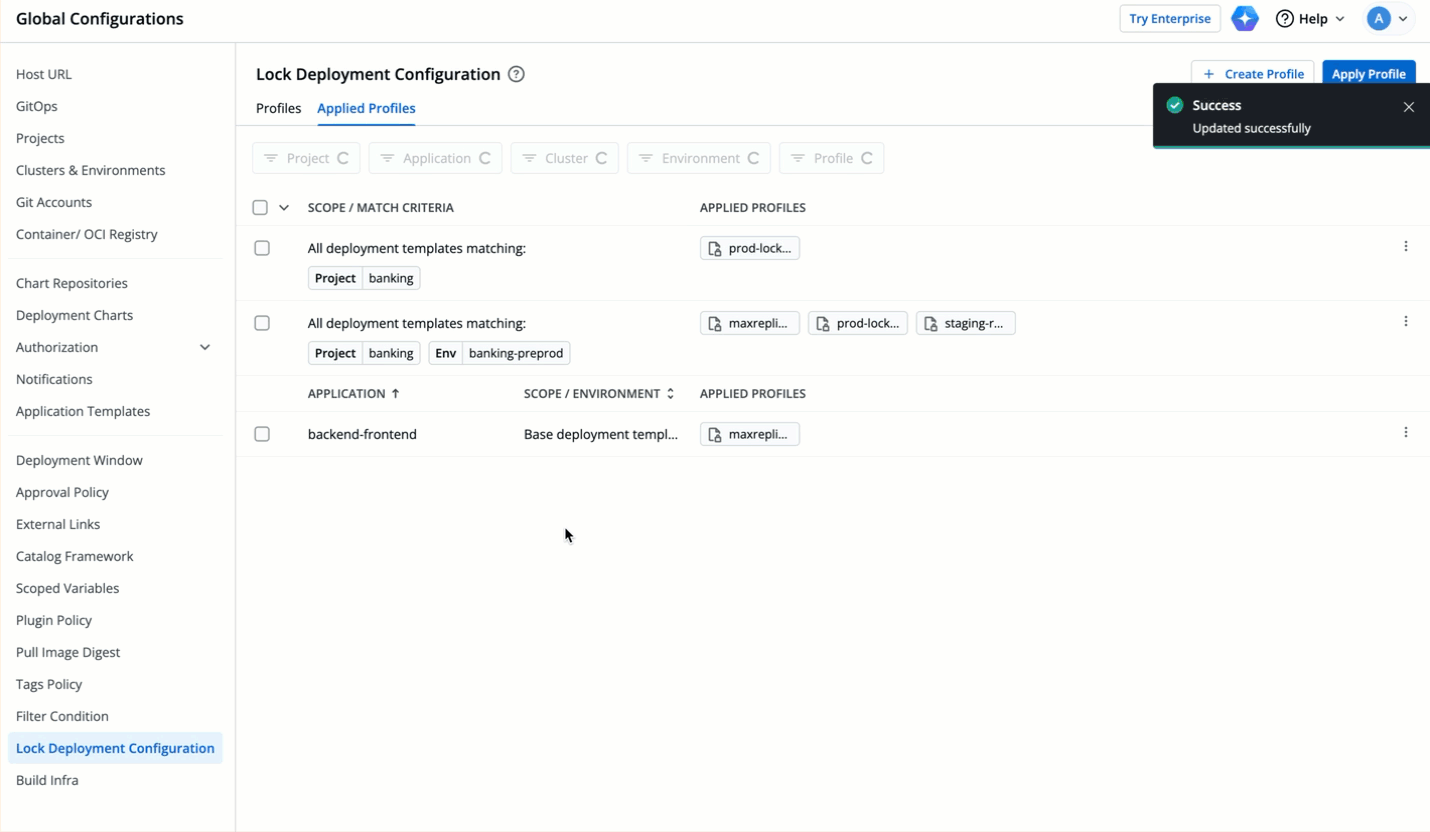 |
| 208 | + |
| 209 | +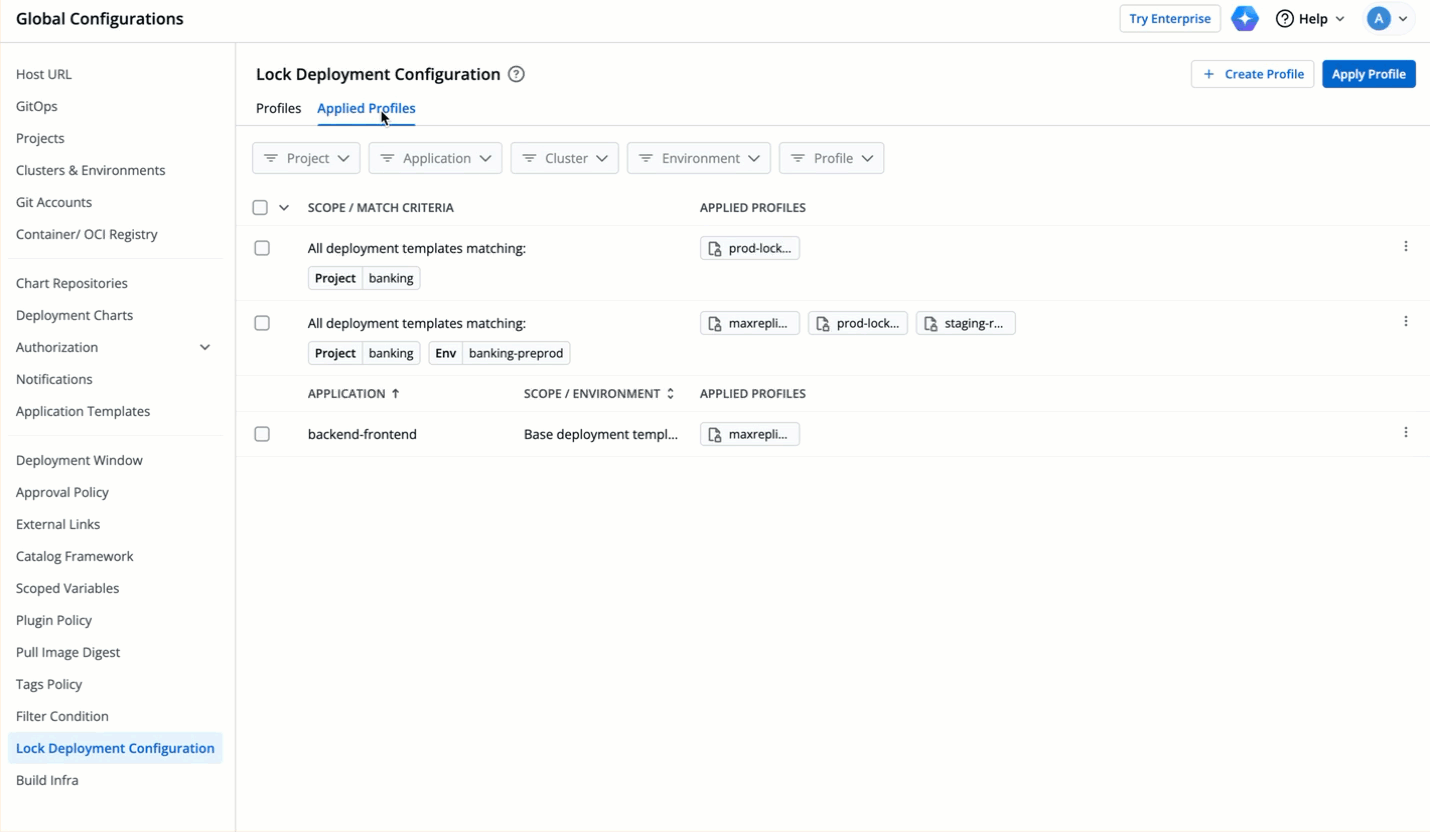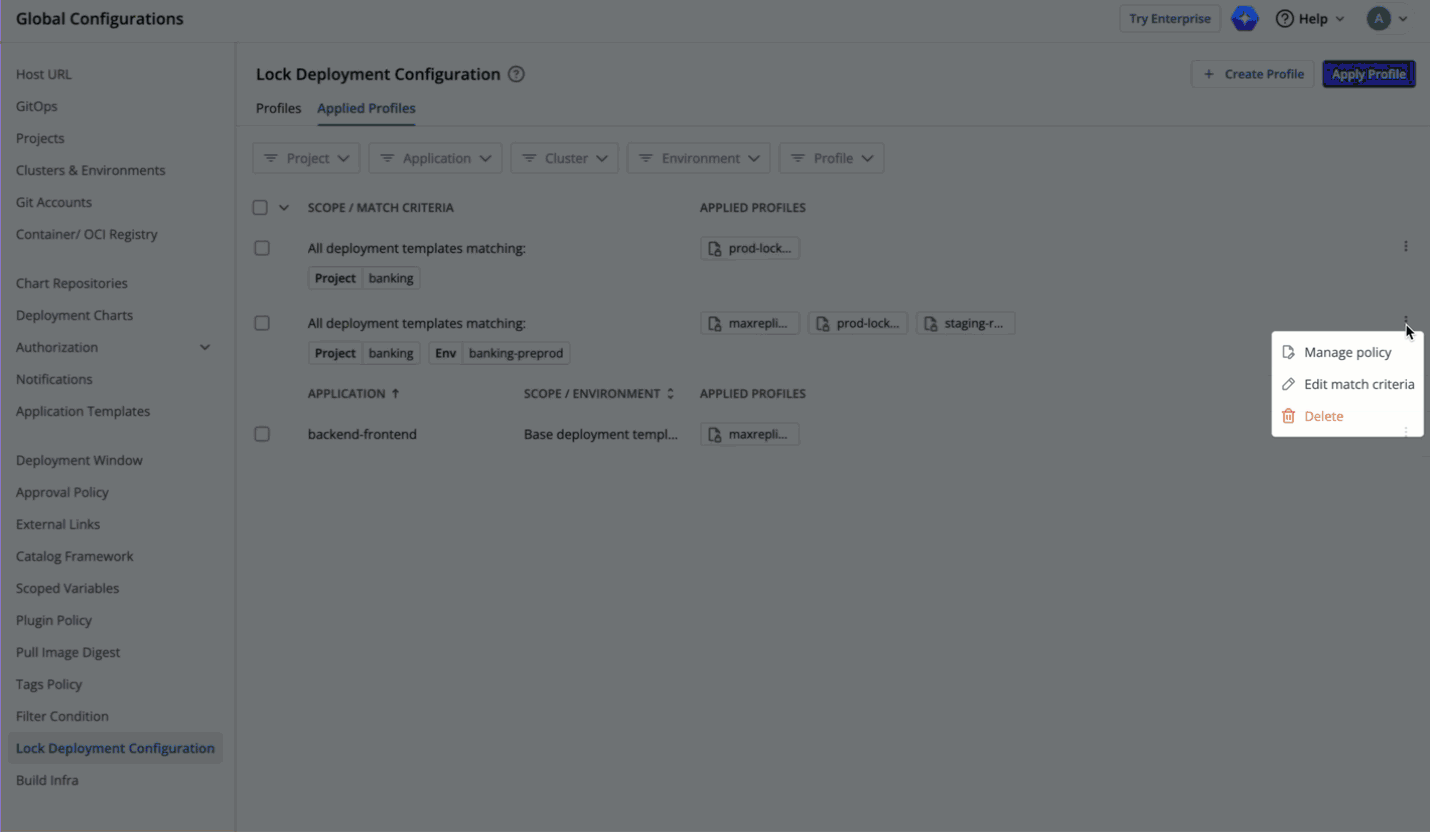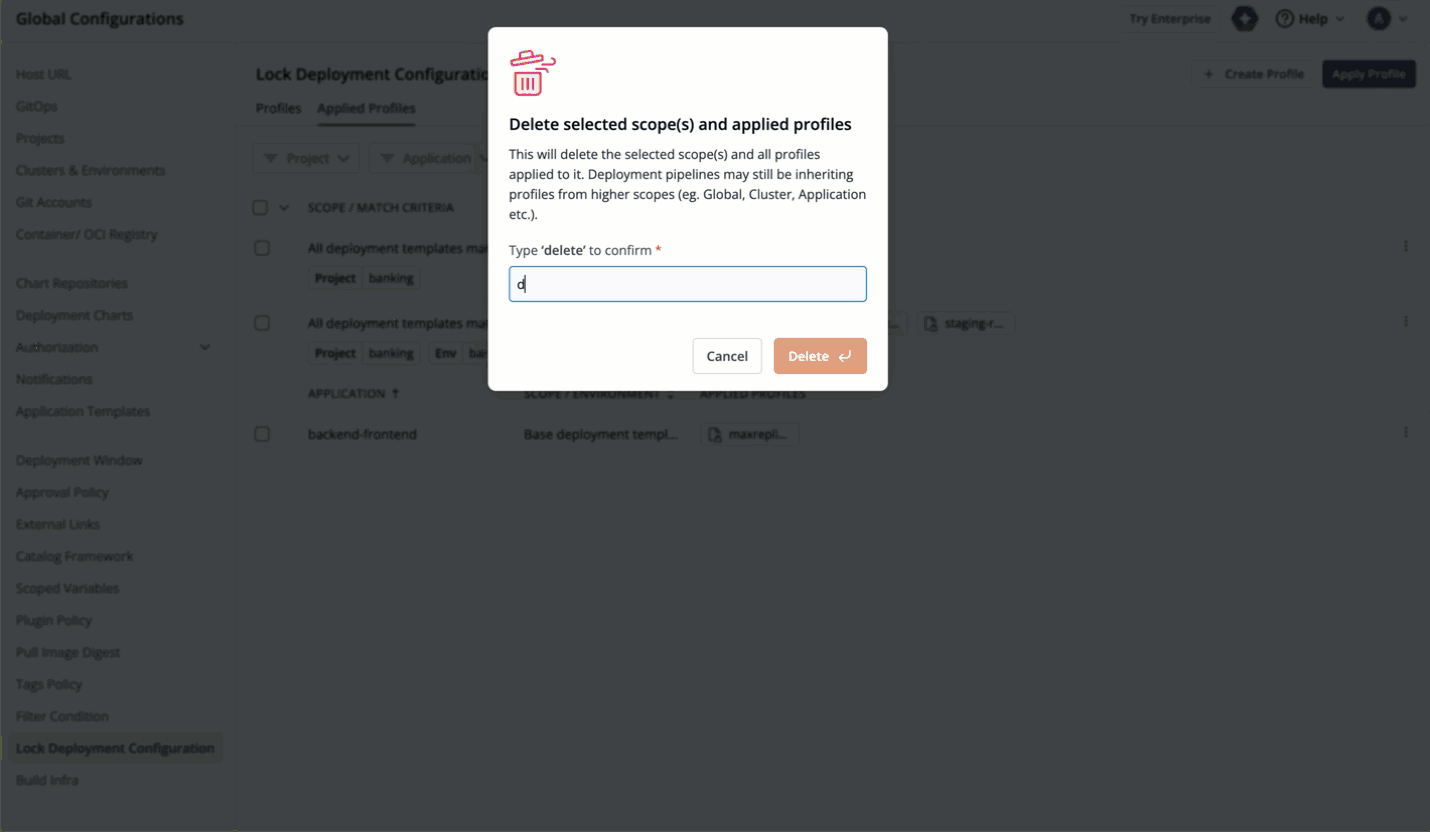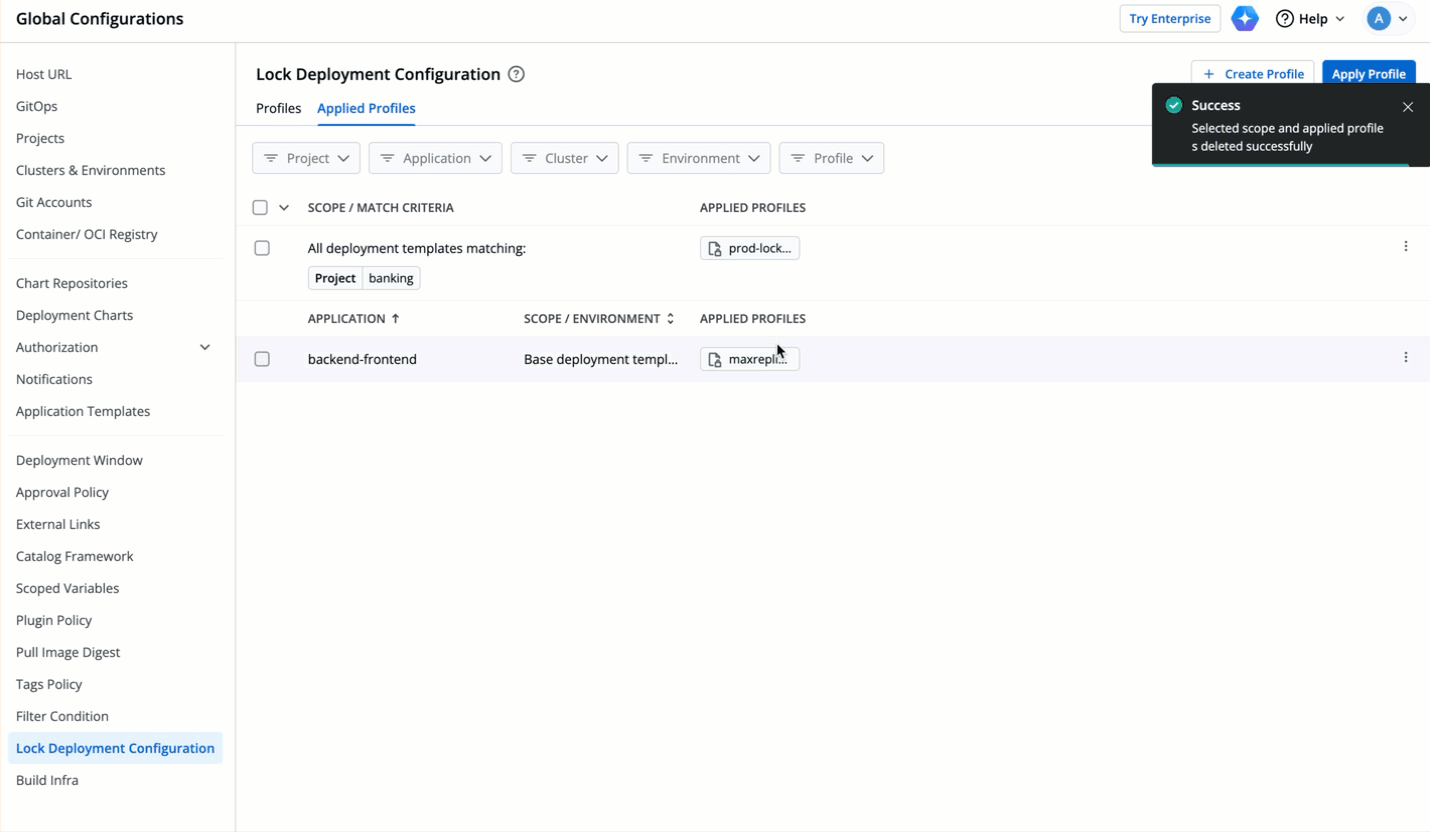 |
| 210 | + |
| 211 | +{% hint style="warning" %} |
| 212 | +### Note |
| 213 | +Removing an applied profile does not delete the lock deployment configuration profile. It only removes the associated restrictions from the deployment templates where the profile was applied. |
| 214 | +{% endhint %} |
| 215 | + |
| 216 | +--- |
| 217 | + |
| 218 | +## Updating Profile |
| 219 | + |
| 220 | +To update a lock deployment configuration file, follow the steps below: |
| 221 | + |
| 222 | +1. Go to **Global Configurations** → **Lock Deployment Configuration**. |
| 223 | + |
| 224 | +2. Click the **Profiles** tab and then click the edit button next to the preferred profile. |
| 225 | + |
| 226 | +3. Edit the profile. |
| 227 | + |
| 228 | +4. Click **Save Changes**. |
| 229 | + |
| 230 | +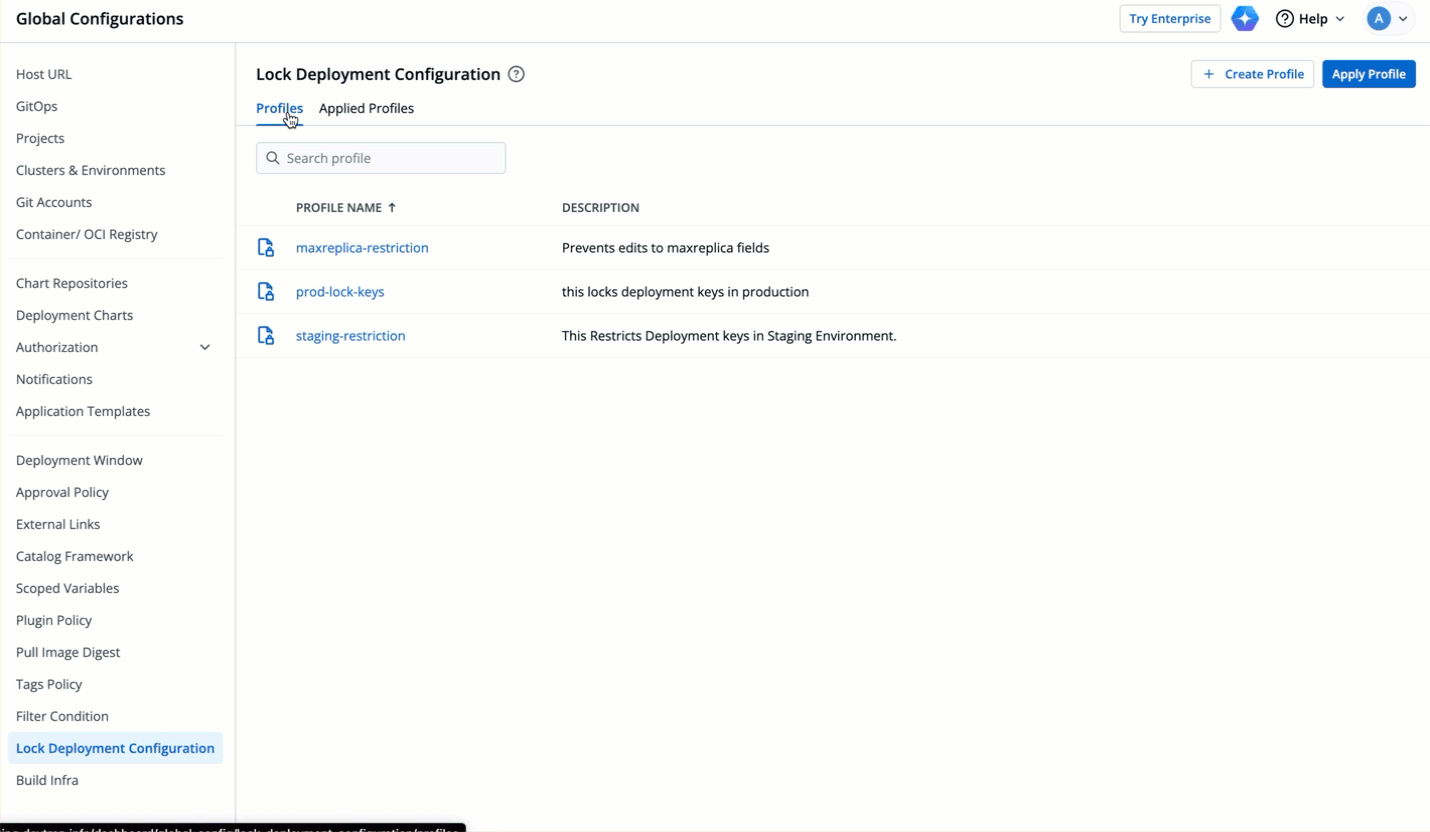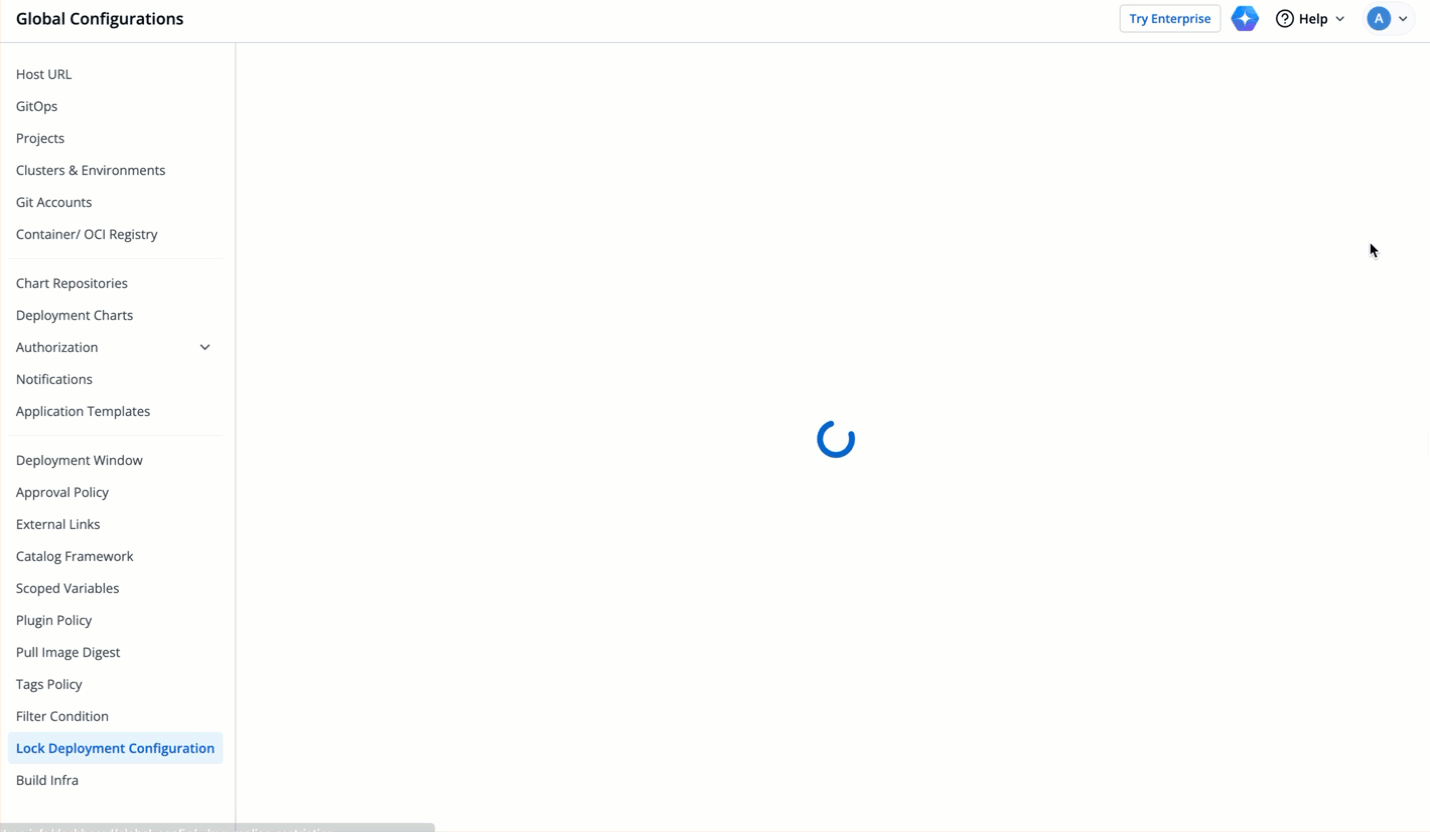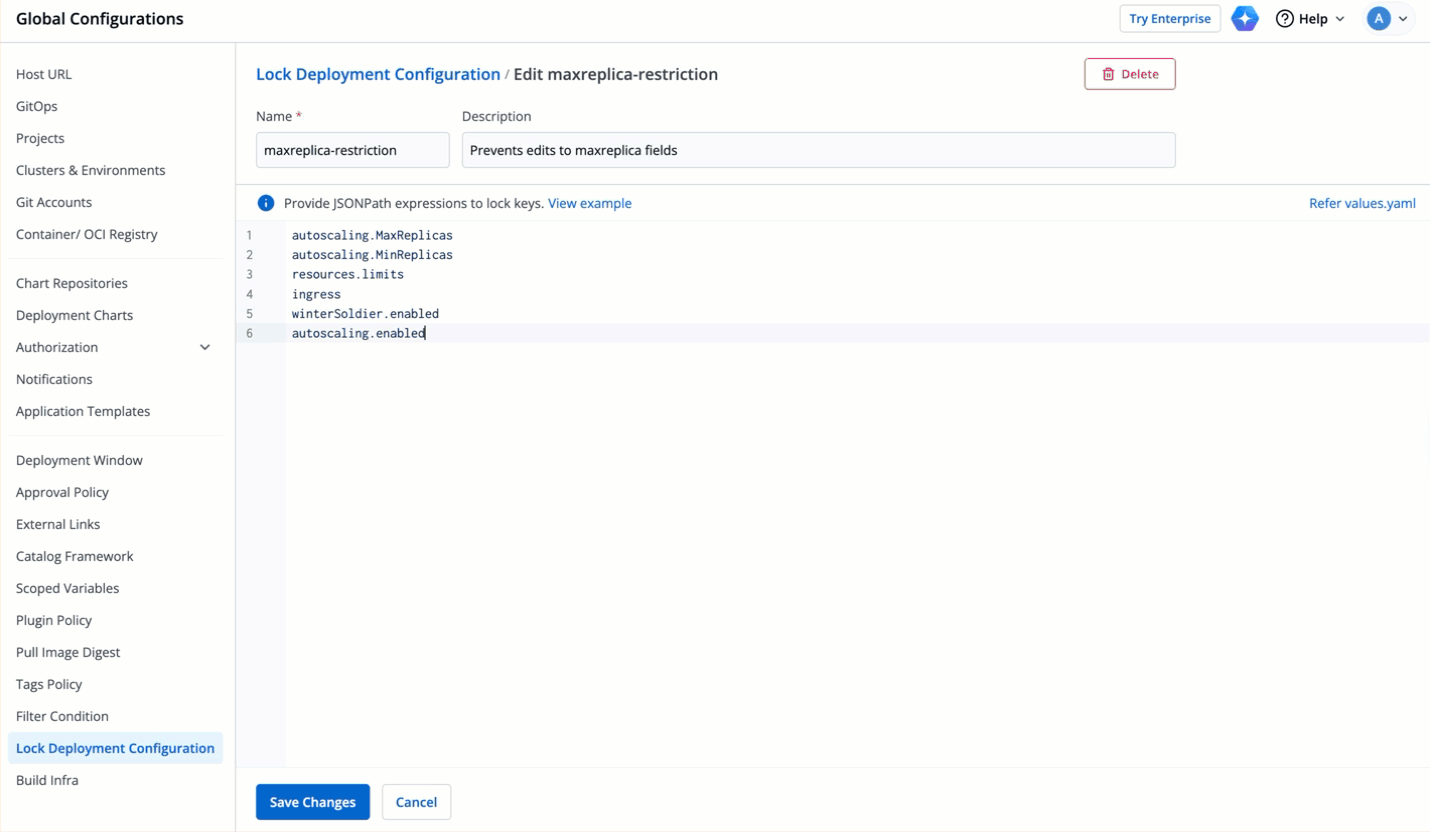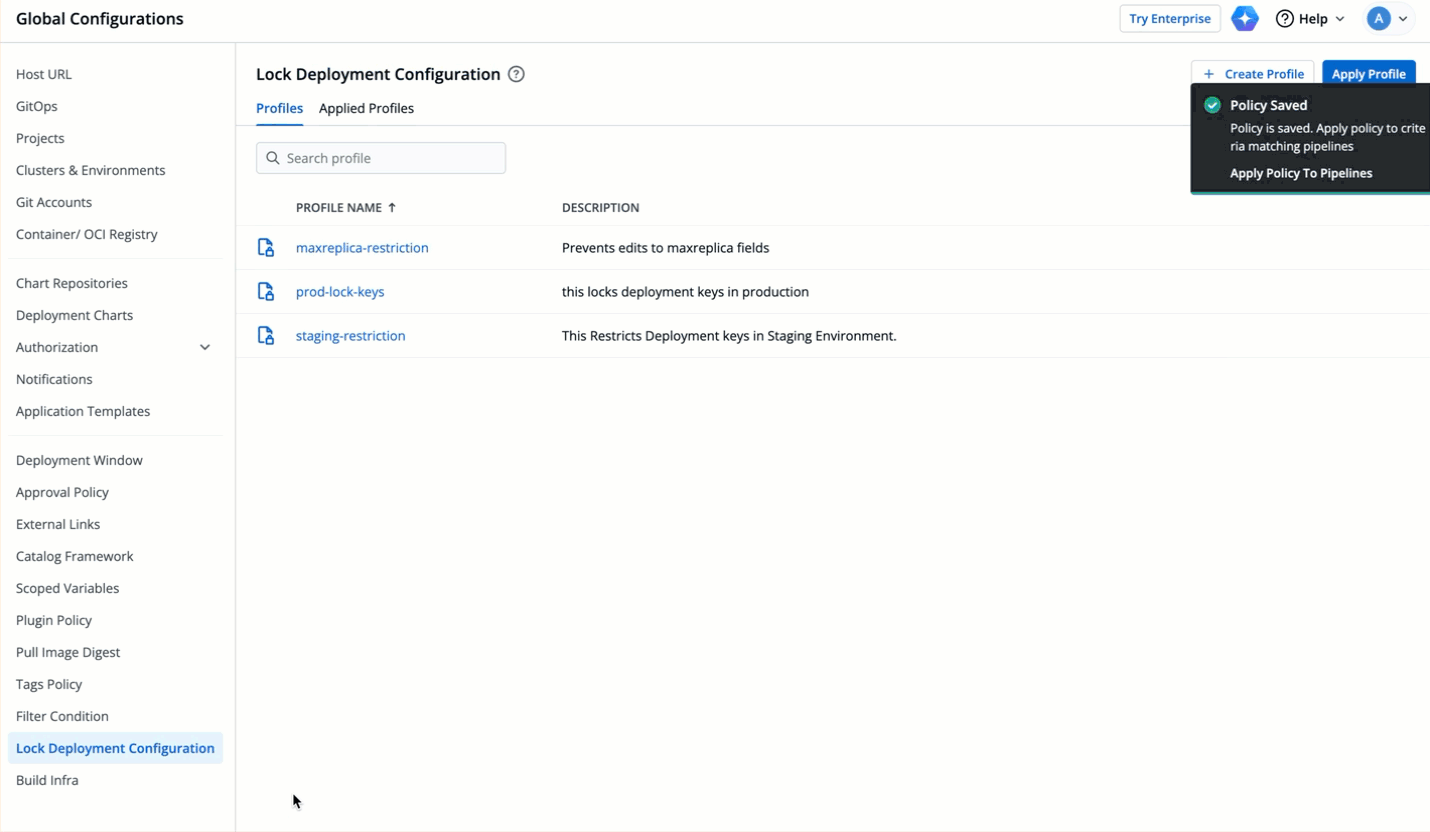 |
| 231 | + |
| 232 | +--- |
| 233 | + |
| 234 | +## Deleting Profile |
| 235 | + |
| 236 | +To delete a lock deployment configuration file, follow the steps below: |
| 237 | + |
| 238 | +1. Go to **Global Configurations** → **Lock Deployment Configuration**. |
| 239 | + |
| 240 | +2. Click the **Profiles** tab and then click the delete button next to the preferred profile. |
| 241 | + |
| 242 | +3. A pop-up window will appear, prompting you to enter the profile name for confirmation. |
| 243 | + |
| 244 | +4. Enter the name of the profile and click **Delete**. |
| 245 | + |
| 246 | +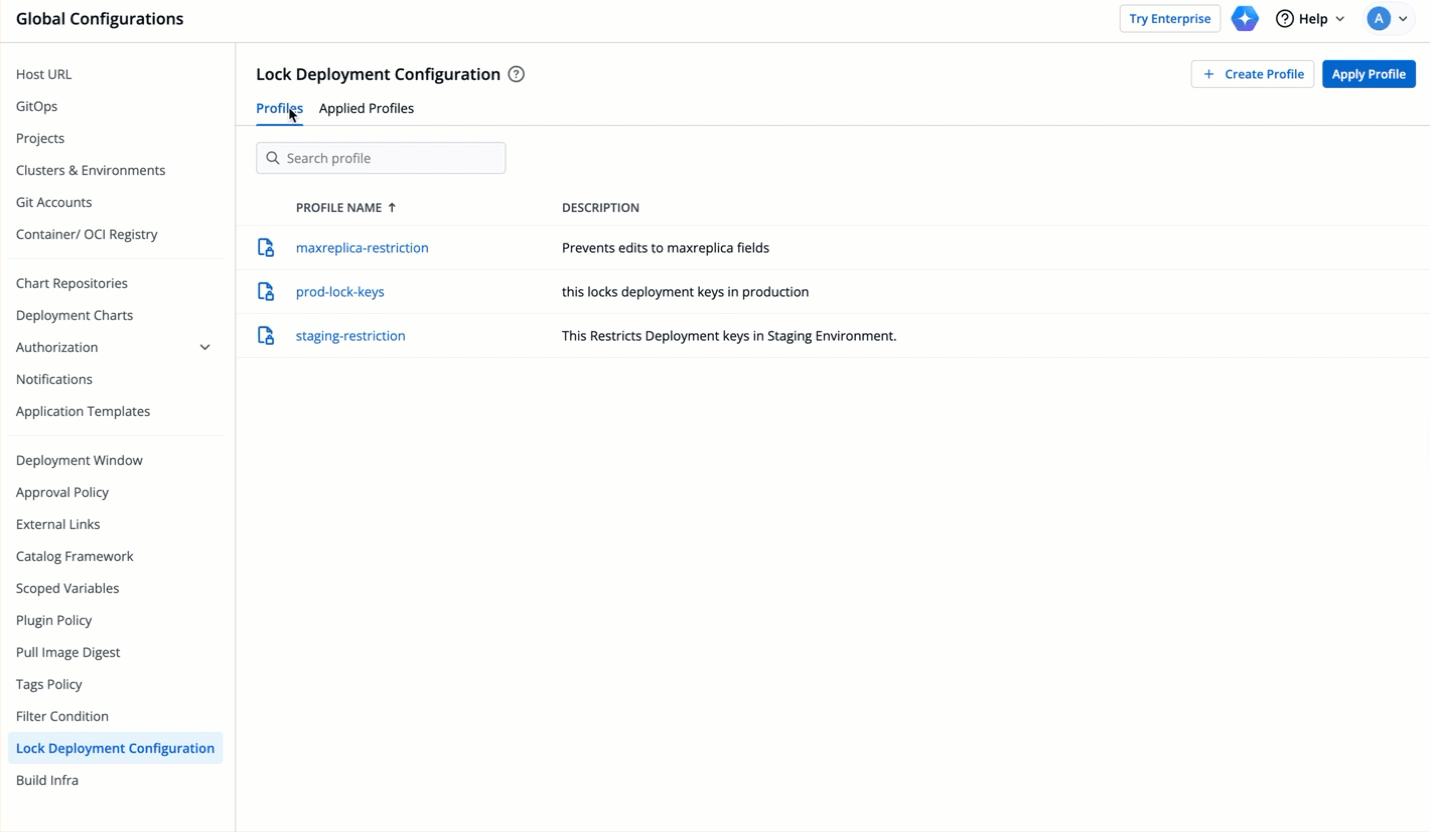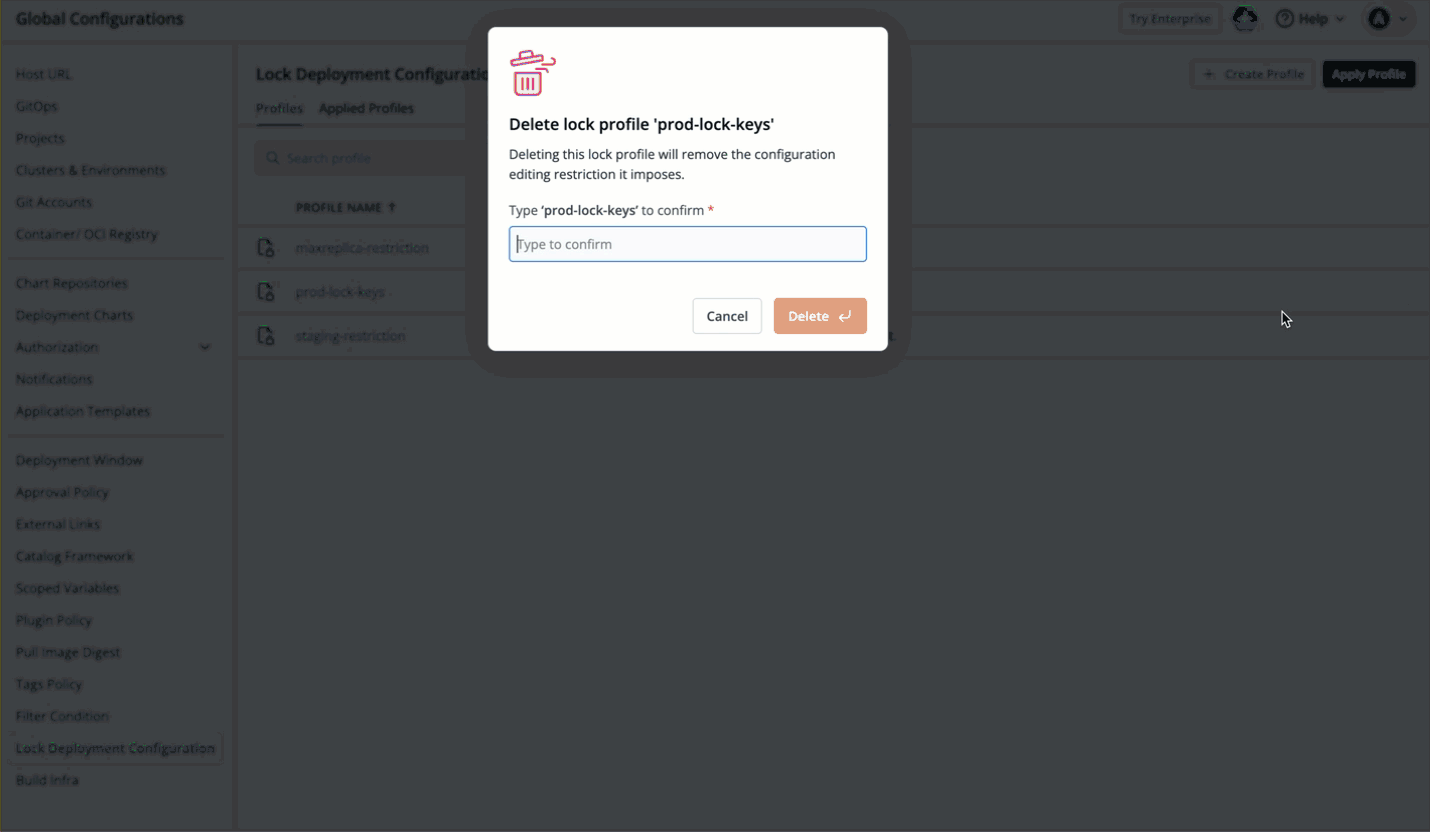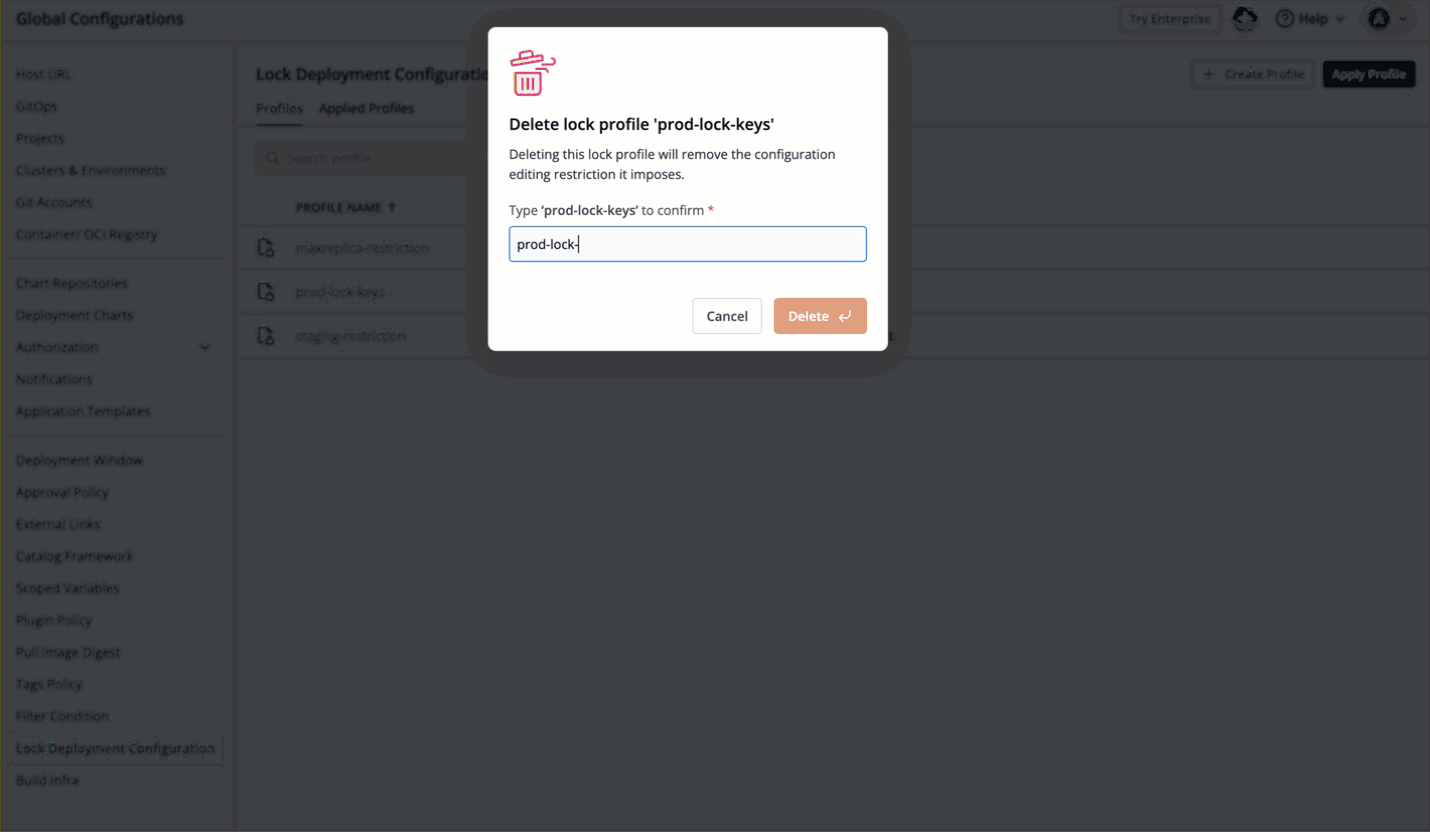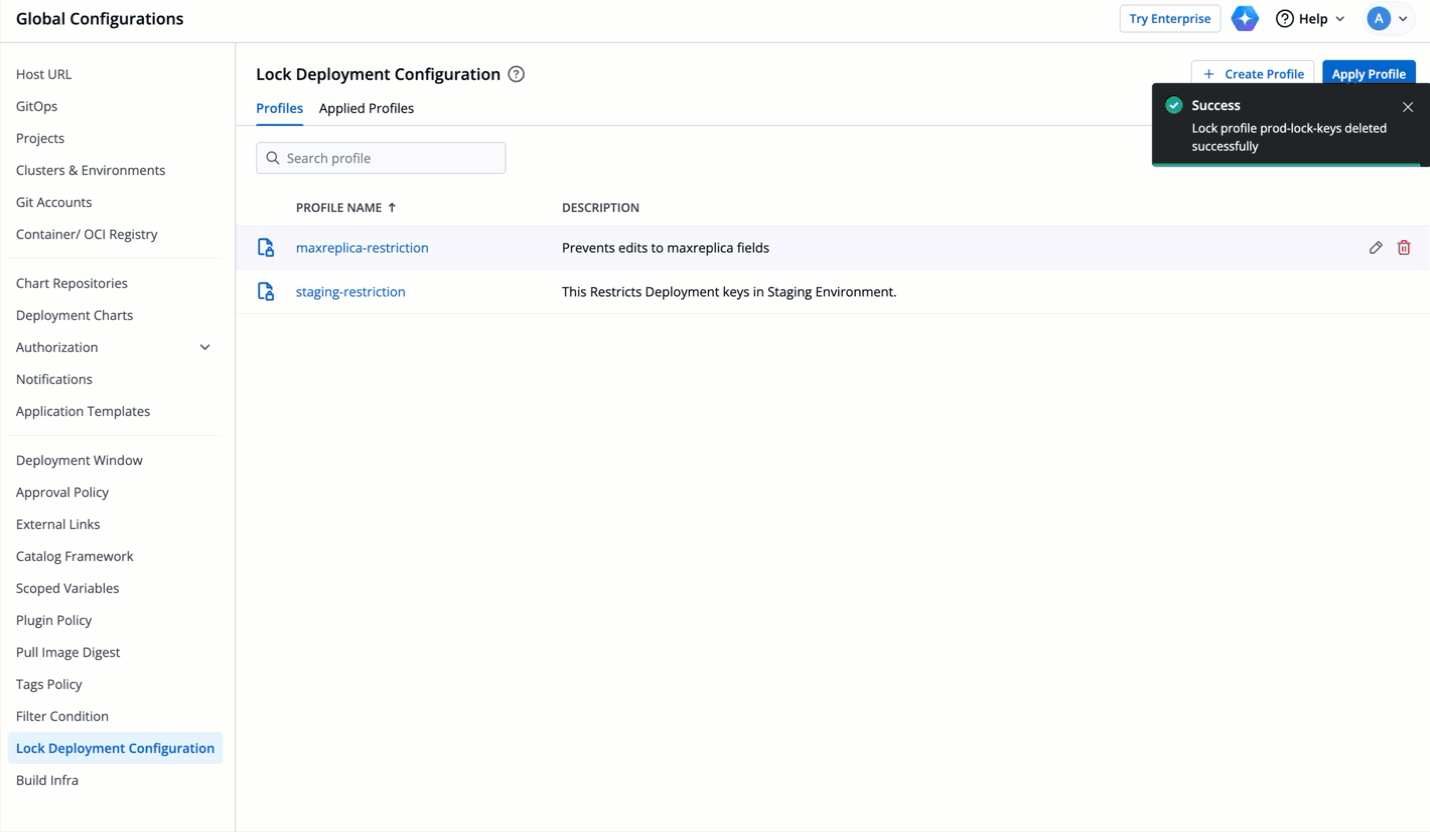 |
| 247 | + |
| 248 | +{% hint style="warning" %} |
| 249 | +### Note |
| 250 | +Deleting a profile will automatically remove it from the Applied Profiles tab and remove its restrictions from all deployment templates where it was previously applied. |
| 251 | +{% endhint %} |
| 252 | + |
| 253 | + |
| 254 | +## Use Cases |
| 255 | + |
| 256 | +### Locking Resources |
| 257 | + |
| 258 | +Managing resources configurations (CPU & Memory) is critical for application stability (specifically in production environments). |
| 259 | + |
| 260 | +To prevent accidental or unauthorized changes to resource configurations (CPU & Memory), you can create a lock deployment configuration profile which locks resource configurations, and then you can apply it to the relevant deployment templates. |
| 261 | + |
| 262 | +**Lock Deployment Configuration Profile** |
| 263 | + |
| 264 | +```yaml |
| 265 | +resources.limits.cpu |
| 266 | +resources.limits.memory |
| 267 | +resources.requests.cpu |
| 268 | +resources.requests.memory |
| 269 | +``` |
| 270 | + |
| 271 | +This ensures that only super admins can modify critical resource configurations (increasing CPU or reducing memory) especially in sensitive environments like production. |
| 272 | + |
| 273 | +### Locking Autoscaling |
| 274 | + |
| 275 | +Autoscaling configurations controls how your application scales based on traffic or resource usage. If not managed properly, accidental or unauthorized changes to autoscaling configurations can cause resource overuse resulting in high cost or application instability. |
| 276 | + |
| 277 | +To prevent accidental or unauthorized changes to autoscaling configurations, you can create a lock deployment configuration profile which locks autoscaling configurations, and then you can apply it to the relevant deployment templates. |
| 278 | + |
| 279 | +**Lock Deployment Configuration Profile** |
| 280 | + |
| 281 | +```yaml |
| 282 | +autoscaling.MaxReplicas |
| 283 | +autoscaling.MinReplicas |
| 284 | +autoscaling.TargetCPUUtilizationPercentage |
| 285 | +autoscaling.TargetMemoryUtilizationPercentage |
| 286 | +autoscaling.annotations |
| 287 | +autoscaling.behavior |
| 288 | +autoscaling.containerResource.TargetCPUUtilizationPercentage |
| 289 | +autoscaling.containerResource.TargetMemoryUtilizationPercentage |
| 290 | +autoscaling.containerResource.enabled |
| 291 | +autoscaling.enabled |
| 292 | +autoscaling.extraMetrics |
| 293 | +autoscaling.labels |
| 294 | +``` |
| 295 | + |
| 296 | +### Locking Ingress |
| 297 | + |
| 298 | +Ingress configuration defines how external traffic is routed to your application. Unauthorized or accidental changes to ingress rules (hostnames or paths), can lead to incorrect routing, broken endpoints, or access to unintended environments. |
| 299 | + |
| 300 | +To prevent accidental or unauthorized changes to ingress configurations, you can create a lock deployment configuration profile which locks ingress configurations, and then you can apply it to the relevant deployment templates. |
| 301 | + |
| 302 | +**Lock Deployment Configuration Profile** |
| 303 | + |
| 304 | +```yaml |
| 305 | +ingress |
| 306 | +ingressinternal.hosts |
| 307 | +ingressInternal.hosts[*].pathType |
| 308 | +``` |
0 commit comments