Important
For new deployments we now recommend using Azure Verified Modules for Platform Landing Zones. Please see the documentation at https://aka.ms/alz/tf. This module will continue to be supported for existing deployments.
Detailed information about how to use, configure and extend this module can be found on our Wiki:
We are planning to make some breaking changes to the module in the next release (Q4 2024).
- Module defaults will updated to deploy zone redundant SKUs by default - this applies to:
- Firewall
- Public IP
- Virtual Network Gateway
We will publish guidance on how to avoid re-deployment of existing resources nearer the time.
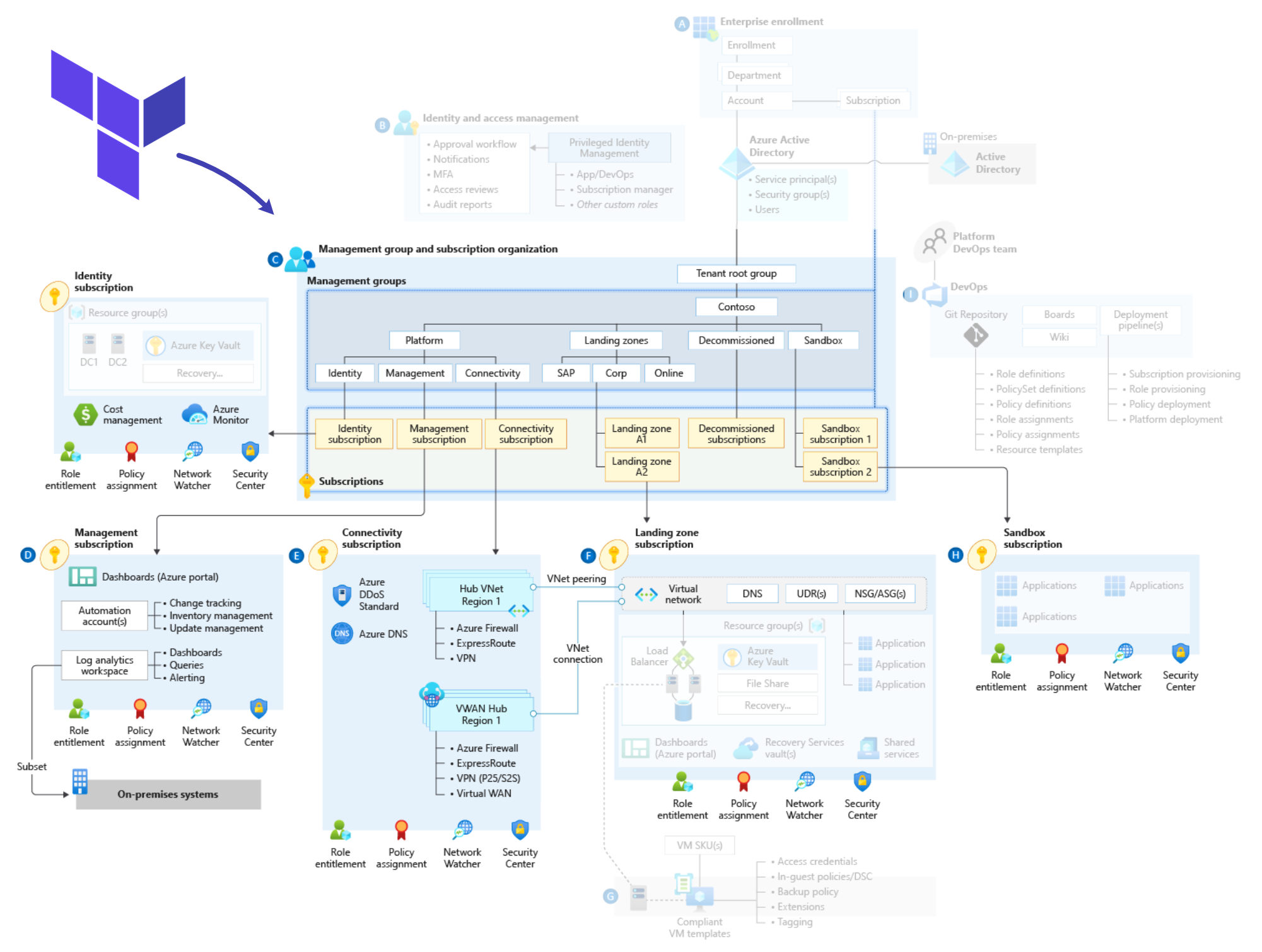
The Azure landing zones Terraform module is designed to accelerate deployment of platform resources based on the Azure landing zones conceptual architecture using Terraform.
This is currently split logically into the following capabilities within the module (links to further guidance on the Wiki):
| Module capability | Scope | Design area |
|---|---|---|
| Core Resources | Management group and subscription organization | Resource organization |
| Management Resources | Management subscription | Management |
| Connectivity Resources | Connectivity subscription | Network topology and connectivity |
| Identity Resources | Identity subscription | Identity and access management |
Using a very simple initial configuration, the module will deploy a management group hierarchy based on the above diagram.
This includes the recommended governance baseline, applied using Azure Policy and Access control (IAM) resources deployed at the management group scope.
The default configuration can be easily extended to meet differing requirements, and includes the ability to deploy platform resources in the management and connectivity subscriptions.
NOTE: In addition to setting input variables to control which resources are deployed, the module requires setting a Provider Configuration block to enable deployment across multiple subscriptions.
Although resources are logically grouped to simplify operations, the modular design of the module also allows resources to be deployed using different Terraform workspaces. This allows customers to address concerns around managing large state files, or assigning granular permissions to pipelines based on the principle of least privilege. (more information coming soon in the Wiki)
This module has been tested using Terraform 1.7.0 and AzureRM Provider 3.108.0 as a baseline, and various versions to up the latest at time of release.
In some cases, individual versions of the AzureRM provider may cause errors.
If this happens, we advise upgrading to the latest version and checking our troubleshooting guide before raising an issue.
We recommend starting with the following configuration in your root module to learn what resources are created by the module and how it works.
This will deploy the core components only.
NOTE: For production use we highly recommend using the Terraform Registry and pinning to the latest stable version, as per the example below. Pinning to the
mainbranch in GitHub will give you the latest updates quicker, but increases the likelihood of unplanned changes to your environment and unforeseen issues.
# Configure Terraform to set the required AzureRM provider
# version and features{} block.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~> 3.107"
}
}
}
provider "azurerm" {
features {}
}
# Get the current client configuration from the AzureRM provider.
# This is used to populate the root_parent_id variable with the
# current Tenant ID used as the ID for the "Tenant Root Group"
# management group.
data "azurerm_client_config" "core" {}
# Use variables to customize the deployment
variable "root_id" {
type = string
default = "es"
}
variable "root_name" {
type = string
default = "Enterprise-Scale"
}
variable "default_location" {
type = string
}
# Declare the Azure landing zones Terraform module
# and provide a base configuration.
module "enterprise_scale" {
source = "Azure/caf-enterprise-scale/azurerm"
version = "<version>" # change this to your desired version, https://www.terraform.io/language/expressions/version-constraints
default_location = var.default_location
providers = {
azurerm = azurerm
azurerm.connectivity = azurerm
azurerm.management = azurerm
}
root_parent_id = data.azurerm_client_config.core.tenant_id
root_id = var.root_id
root_name = var.root_name
}NOTE: For additional guidance on how to customize your deployment using the advanced configuration options for this module, please refer to our User Guide and the additional examples in our documentation.
Please refer to our Module Permissions guide on the Wiki.
The following list outlines some of our most popular examples:
For the complete list of our latest examples, please refer to our Examples page on the Wiki.
Please see the releases page for the latest module updates.
For upgrade guides from previous versions, please refer to the following links:
- Upgrade from v5.2.1 to v6.0.0
- Upgrade from v4.2.0 to v5.0.0
- Upgrade from v3.3.0 to v4.0.0
- Upgrade from v2.4.1 to v3.0.0
- Upgrade from v1.1.4 to v2.0.0
- Upgrade from v0.4.0 to v1.0.0
- Upgrade from v0.3.3 to v0.4.0
- Upgrade from v0.1.2 to v0.2.0
- Upgrade from v0.0.8 to v0.1.0
| Name | Version |
|---|---|
| terraform | ~> 1.7 |
| azapi | ~> 1.13, != 1.13.0 |
| azurerm | >= 3.108.0, < 5.0.0 |
| random | ~> 3.6 |
| time | ~> 0.11 |
| Name | Source | Version |
|---|---|---|
| connectivity_resources | ./modules/connectivity | n/a |
| identity_resources | ./modules/identity | n/a |
| management_group_archetypes | ./modules/archetypes | n/a |
| management_resources | ./modules/management | n/a |
| role_assignments_for_policy | ./modules/role_assignments_for_policy | n/a |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| default_location | Must be specified, e.g eastus. Will set the Azure region in which region bound resources will be deployed. Please see: https://azure.microsoft.com/en-gb/global-infrastructure/geographies/ |
string |
n/a | yes |
| root_parent_id | The root_parent_id is used to specify where to set the root for all Landing Zone deployments. Usually the Tenant ID when deploying the core Enterprise-scale Landing Zones. | string |
n/a | yes |
| archetype_config_overrides | If specified, will set custom Archetype configurations for the core ALZ Management Groups. Does not work for management groups specified by the 'custom_landing_zones' input variable. To override the default configuration settings for any of the core Management Groups, add an entry to the archetype_config_overrides variable for each Management Group you want to customize. To create a valid archetype_config_overrides entry, you must provide the required values in the archetype_config_overrides object for the Management Group you wish to re-configure. To do this, simply create an entry similar to the root example below for one or more of the supported core Management Group IDs: - root - decommissioned - sandboxes - landing-zones - platform - connectivity - management - identity - corp - online - sap terraforme.g. terraform |
any |
{} |
no |
| configure_connectivity_resources | If specified, will customize the "Connectivity" landing zone settings and resources. Notes for the configure_connectivity_resources variable:- settings.hub_network_virtual_network_gateway.config.address_prefix- Only support adding a single address prefix for GatewaySubnet subnet - settings.hub_network_virtual_network_gateway.config.gateway_sku_expressroute- If specified, will deploy the ExpressRoute gateway into the GatewaySubnet subnet - settings.hub_network_virtual_network_gateway.config.gateway_sku_vpn- If specified, will deploy the VPN gateway into the GatewaySubnet subnet - settings.hub_network_virtual_network_gateway.config.advanced_vpn_settings.private_ip_address_allocation- Valid options are "", "Static" or "Dynamic". Will set private_ip_address_enabled and private_ip_address_allocation as needed.- settings.azure_firewall.config.address_prefix- Only support adding a single address prefix for AzureFirewallManagementSubnet subnet |
object({ |
{} |
no |
| configure_identity_resources | If specified, will customize the "Identity" landing zone settings. | object({ |
{} |
no |
| configure_management_resources | If specified, will customize the "Management" landing zone settings and resources. | object({ |
{} |
no |
| create_duration_delay | Used to tune terraform apply when faced with errors caused by API caching or eventual consistency. Sets a custom delay period after creation of the specified resource type. | object({ |
{} |
no |
| custom_landing_zones | If specified, will deploy additional Management Groups alongside Enterprise-scale core Management Groups. Although the object type for this input variable is set to any, the expected object is based on the following structure:terraformThe decision not to hard code the structure in the input variable type is by design, as it allows Terraform to handle the input as a dynamic object type.This was necessary to allow the parameters value to be correctly interpreted.Without this, Terraform would throw an error if each parameter value wasn't a consistent type, as it would incorrectly identify the input as a tuple which must contain consistent type structure across all entries.> Note the id of the custom landing zone will be appended to var.root_id. The maximum length of the resulting name must be less than 90 characters.The custom_landing_zones object is used to deploy additional Management Groups within the core Management Group hierarchy.The main object parameters are display_name, parent_management_group_id, subscription_idsand archetype_config.- display_name is the name assigned to the Management Group.- parent_management_group_id is the name of the parent Management Group and must be a valid Management Group ID.- subscription_ids is an object containing a list of Subscription IDs to assign to the current Management Group.- archetype_config is used to configure the configuration applied to each Management Group. This object must contain valid entries for the archetype_id parameters, and access_control attributes.The following example shows how you would add a simple Management Group under the myorg-landing-zones Management Group, where root_id = "myorg" and using the default_empty archetype definition.terraform |
any |
{} |
no |
| custom_policy_roles | If specified, the custom_policy_roles variable overrides which Role Definition ID(s) (value) to assign for Policy Assignments with a Managed Identity, if the assigned "policyDefinitionId" (key) is included in this variable. | map(list(string)) |
{} |
no |
| default_tags | If specified, will set the default tags for all resources deployed by this module where supported. | map(string) |
{} |
no |
| deploy_connectivity_resources | If set to true, will enable the "Connectivity" landing zone settings and add "Connectivity" resources into the current Subscription context. | bool |
false |
no |
| deploy_core_landing_zones | If set to true, module will deploy the core Enterprise-scale Management Group hierarchy, including "out of the box" policies and roles. | bool |
true |
no |
| deploy_corp_landing_zones | If set to true, module will deploy the "Corp" Management Group, including "out of the box" policies and roles. | bool |
false |
no |
| deploy_demo_landing_zones | If set to true, module will deploy the demo "Landing Zone" Management Groups ("Corp", "Online", and "SAP") into the core Enterprise-scale Management Group hierarchy. | bool |
false |
no |
| deploy_diagnostics_for_mg | If set to true, will deploy Diagnostic Settings for management groups | bool |
false |
no |
| deploy_identity_resources | If set to true, will enable the "Identity" landing zone settings. | bool |
false |
no |
| deploy_management_resources | If set to true, will enable the "Management" landing zone settings and add "Management" resources into the current Subscription context. | bool |
false |
no |
| deploy_online_landing_zones | If set to true, module will deploy the "Online" Management Group, including "out of the box" policies and roles. | bool |
false |
no |
| deploy_sap_landing_zones | If set to true, module will deploy the "SAP" Management Group, including "out of the box" policies and roles. | bool |
false |
no |
| destroy_duration_delay | Used to tune terraform deploy when faced with errors caused by API caching or eventual consistency. Sets a custom delay period after destruction of the specified resource type. | object({ |
{} |
no |
| disable_base_module_tags | If set to true, will remove the base module tags applied to all resources deployed by the module which support tags. | bool |
false |
no |
| disable_telemetry | If set to true, will disable telemetry for the module. See https://aka.ms/alz-terraform-module-telemetry. | bool |
false |
no |
| library_path | If specified, sets the path to a custom library folder for archetype artefacts. | string |
"" |
no |
| policy_non_compliance_message_default | If set overrides the default non-compliance message used for policy assignments. | string |
"This resource {enforcementMode} be compliant with the assigned policy." |
no |
| policy_non_compliance_message_default_enabled | If set to true, will enable the use of the default custom non-compliance messages for policy assignments if they are not provided. | bool |
true |
no |
| policy_non_compliance_message_enabled | If set to false, will disable non-compliance messages altogether. | bool |
true |
no |
| policy_non_compliance_message_enforced_replacement | If set overrides the non-compliance replacement used for enforced policy assignments. | string |
"must" |
no |
| policy_non_compliance_message_enforcement_placeholder | If set overrides the non-compliance message placeholder used in message templates. | string |
"{enforcementMode}" |
no |
| policy_non_compliance_message_not_enforced_replacement | If set overrides the non-compliance replacement used for unenforced policy assignments. | string |
"should" |
no |
| policy_non_compliance_message_not_supported_definitions | If set, overrides the list of built-in policy definition that do not support non-compliance messages. | list(string) |
[ |
no |
| resource_custom_timeouts | Optional - Used to tune terraform deploy when faced with errors caused by API limits. For each supported resource type, there is a child object that specifies the create, update, and delete timeouts. Each of these arguments takes a string representation of a duration, such as "60m" for 60 minutes, "10s" for ten seconds, or "2h" for two hours. If a timeout is not specified, the default value for the resource will be used. e.g. hcl |
object({ |
{} |
no |
| root_id | If specified, will set a custom Name (ID) value for the Enterprise-scale "root" Management Group, and append this to the ID for all core Enterprise-scale Management Groups. | string |
"es" |
no |
| root_name | If specified, will set a custom Display Name value for the Enterprise-scale "root" Management Group. | string |
"Enterprise-Scale" |
no |
| strict_subscription_association | If set to true, subscriptions associated to management groups will be exclusively set by the module and any added by another process will be removed. If set to false, the module will will only enforce association of the specified subscriptions and those added to management groups by other processes will not be removed. Default is false as this works better with subscription vending. | bool |
false |
no |
| subscription_id_connectivity | If specified, identifies the Platform subscription for "Connectivity" for resource deployment and correct placement in the Management Group hierarchy. | string |
"" |
no |
| subscription_id_identity | If specified, identifies the Platform subscription for "Identity" for resource deployment and correct placement in the Management Group hierarchy. | string |
"" |
no |
| subscription_id_management | If specified, identifies the Platform subscription for "Management" for resource deployment and correct placement in the Management Group hierarchy. | string |
"" |
no |
| subscription_id_overrides | If specified, will be used to assign subscription_ids to the default Enterprise-scale Management Groups. | map(list(string)) |
{} |
no |
| template_file_variables | If specified, provides the ability to define custom template variables used when reading in template files from the built-in and custom library_path. | any |
{} |
no |
| Name | Description |
|---|---|
| ama_user_assigned_identity | The user assigned identity for Azure Monitor Agent that is created by this module. |
| azurerm_automation_account | Returns the configuration data for all Automation Accounts created by this module. |
| azurerm_dns_zone | Returns the configuration data for all DNS Zones created by this module. |
| azurerm_express_route_gateway | Returns the configuration data for all (Virtual WAN) ExpressRoute Gateways created by this module. |
| azurerm_firewall | Returns the configuration data for all Azure Firewalls created by this module. |
| azurerm_firewall_policy | Returns the configuration data for all Azure Firewall Policies created by this module. |
| azurerm_log_analytics_linked_service | Returns the configuration data for all Log Analytics linked services created by this module. |
| azurerm_log_analytics_solution | Returns the configuration data for all Log Analytics solutions created by this module. |
| azurerm_log_analytics_workspace | Returns the configuration data for all Log Analytics workspaces created by this module. |
| azurerm_management_group | Returns the configuration data for all Management Groups created by this module. |
| azurerm_management_group_policy_assignment | Returns the configuration data for all Management Group Policy Assignments created by this module. |
| azurerm_management_group_subscription_association | Returns the configuration data for all Management Group Subscription Associations created by this module. |
| azurerm_network_ddos_protection_plan | Returns the configuration data for all DDoS Protection Plans created by this module. |
| azurerm_policy_definition | Returns the configuration data for all Policy Definitions created by this module. |
| azurerm_policy_set_definition | Returns the configuration data for all Policy Set Definitions created by this module. |
| azurerm_private_dns_zone | Returns the configuration data for all Private DNS Zones created by this module. |
| azurerm_private_dns_zone_virtual_network_link | Returns the configuration data for all Private DNS Zone network links created by this module. |
| azurerm_public_ip | Returns the configuration data for all Public IPs created by this module. |
| azurerm_resource_group | Returns the configuration data for all Resource Groups created by this module. |
| azurerm_role_assignment | Returns the configuration data for all Role Assignments created by this module. |
| azurerm_role_definition | Returns the configuration data for all Role Definitions created by this module. |
| azurerm_subnet | Returns the configuration data for all Subnets created by this module. |
| azurerm_virtual_hub | Returns the configuration data for all Virtual Hubs created by this module. |
| azurerm_virtual_hub_connection | Returns the configuration data for all Virtual Hub Connections created by this module. |
| azurerm_virtual_hub_routing_intent | Returns the configuration data for all Virtual Hub Routing Intents created by this module. |
| azurerm_virtual_network | Returns the configuration data for all Virtual Networks created by this module. |
| azurerm_virtual_network_gateway | Returns the configuration data for all Virtual Network Gateways created by this module. |
| azurerm_virtual_network_peering | Returns the configuration data for all Virtual Network Peerings created by this module. |
| azurerm_virtual_wan | Returns the configuration data for all Virtual WANs created by this module. |
| azurerm_vpn_gateway | Returns the configuration data for all (Virtual WAN) VPN Gateways created by this module. |
| data_collection_rules | A map of the data collection rules created by this module. |
NOTE: The following statement is applicable from release v2.0.0 onwards
When you deploy one or more modules using the Azure landing zones Terraform module, Microsoft can identify the installation of said module/s with the deployed Azure resources. Microsoft can correlate these resources used to support the software. Microsoft collects this information to provide the best experiences with their products and to operate their business. The telemetry is collected through customer usage attribution. The data is collected and governed by Microsoft's privacy policies.
If you don't wish to send usage data to Microsoft, details on how to turn it off can be found here.